Your cart is currently empty!

The Most Common Cybersecurity Interview Questions and Answers
I’m here to share insights and advice on how to approach the top 50 common cybersecurity interview questions you might encounter.
While it’s crucial to adapt your answers to your unique experiences, understanding what hiring managers are looking for can give you a significant advantage.
50+ most common cybersecurity job interview questions
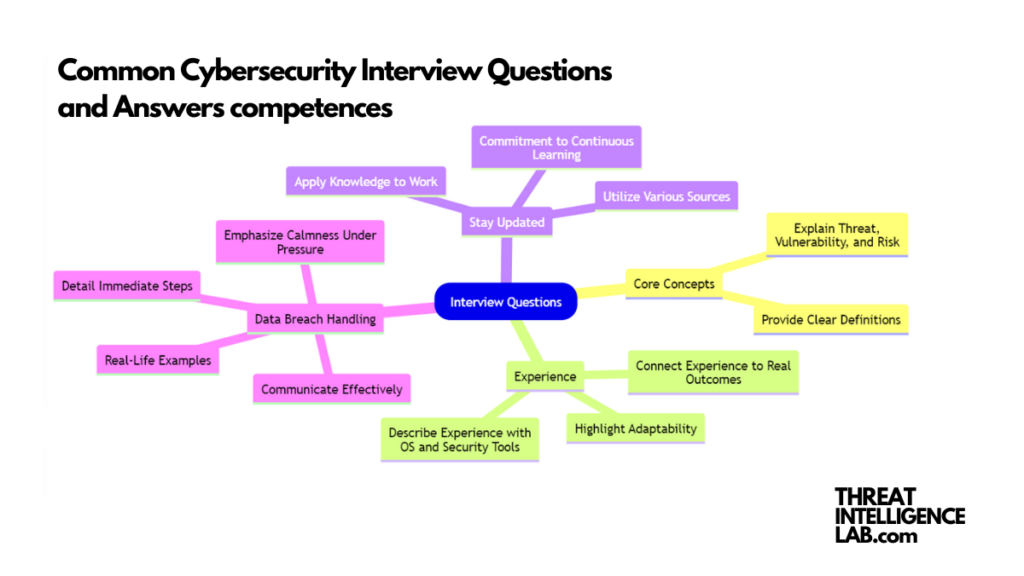
1. Can you explain the difference between a threat, a vulnerability, and a risk?
Understanding core concepts is vital in cybersecurity. Each term defines a specific aspect of security weakness and its potential impact. Don’t mix these up or give vague definitions; clarity here shows your foundational knowledge.
To illustrate, a threat is any potential malicious attack or event that can harm an organization, a vulnerability is a weakness or gap in the security system that could be exploited by threats, and risk is the potential for loss or damage when a threat takes advantage of a vulnerability. Understanding the interplay between these elements helps in planning and implementing effective security measures.
Possible answer: “In cybersecurity, a threat refers to any potential malicious activity or attack targeting our organization’s assets and data. A vulnerability signifies a weakness or gap in our system’s security posture that could be exploited by these threats. Risk, on the other hand, encapsulates the potential consequences and impact if a threat successfully exploits a vulnerability. It’s essentially the likelihood of harm or loss resulting from a cyber incident.”
2. Describe your experience with different operating systems and security tools.
Don’t just list the operating systems and tools you’ve used; connect your experience to real outcomes and projects. Highlight your adaptability and willingness to learn new technologies. For example, discuss how you used a particular tool to solve a security challenge or improve system efficiency. Employers seek candidates who not only have experience but can also apply that experience effectively.
Possible answer: “In my previous role as a sys admin, I worked extensively with Linux and Windows servers. I utilized tools like Wireshark for network analysis and Snort for intrusion detection, which significantly improved our system’s security posture.”
3. How do you stay updated with the latest cybersecurity trends and threats?
Show your commitment to continuous learning and improvement. Mention specific sources and methods you use to stay informed. It’s not just about reading articles or watching videos; discuss how you apply what you learn to your work, whether it’s updating policies, implementing new technologies, or educating colleagues.
Possible answer: “I regularly follow cybersecurity blogs like Krebs on Security, participate in online forums, and take part in webinars and local meetups. Recently, I applied a technique from a webinar to enhance our network’s defense against ransomware attacks, significantly reducing our system’s vulnerabilities.”
- How to Conduct an Effective Cyber Threat Intelligence Stand-Up Meeting
- Avoiding Pitfalls: Top 10 Rookie Cybersecurity Career Mistakes
- Land Your First Junior Security Engineer Position
- How to Land Your First Job as a Junior Malware Analyst
- Landing a Junior Penetration Tester Position
4. How would you handle a data breach in your company?
Detail matters here. Walk through your immediate steps, the investigation process, and long-term measures to prevent future breaches. Emphasize your ability to remain calm under pressure, think critically, and communicate effectively with different stakeholders. Real-life examples will strengthen your answer.
Possible answer: “In case of a data breach, my first step is to contain the breach to prevent further data loss, followed by a detailed investigation to identify the breach’s source. I’d then work on recovery and post-incident analysis to improve our defenses. At my last job, I led the response to a breach, which resulted in a faster recovery than previous incidents.”
5. Explain the importance of user education in cybersecurity.
Don’t just say it’s important; explain why. Connect user education to broader security objectives and describe how informed users can significantly reduce risks. Share examples of effective education strategies or campaigns you’ve been part of, and discuss their impact.
Possible answer: “User education is critical because many security breaches are due to human error. At my previous job, I initiated a monthly security newsletter and regular training sessions. Educating users turns them into a proactive defense layer.”
6. What’s your approach to securing a new network?
Be specific about your strategies and methodologies. Explain how you assess the network’s current security posture and outline the steps you take to enhance its security, such as implementing firewalls, intrusion detection systems, and regular audits. Real examples will add credibility to your answer.
Possible answer: “When securing a new network, I start with a comprehensive risk assessment to identify vulnerabilities and prioritize them based on potential impact. At my last job, I implemented a multi-layered security approach, including firewall upgrades and regular penetration testing, which resulted in a 40% reduction in vulnerabilities within the first six months.”
7. Describe a time when you had to manage a security breach. What were the steps you took?
Outline a clear, step-by-step response that demonstrates your ability to act swiftly and effectively. Highlight your role in the incident response team, how you communicated with stakeholders, and the lessons learned from the experience.
Possible answer: “In my previous role, I led the response to a phishing attack that compromised several user accounts. I immediately initiated our incident response plan, isolating affected systems and working with the IT team to reset passwords and patch vulnerabilities. Post-incident, I conducted a debriefing to update our response strategies, significantly improving our reaction time for future incidents.”
8. How do you evaluate the effectiveness of a cybersecurity program?
Discuss the metrics and benchmarks you use to assess a security program’s success, such as incident response times, the number of detected threats, or user compliance rates. Explain how continuous improvement is integral to cybersecurity.
Possible answer: “To evaluate a cybersecurity program, I track key performance indicators like incident detection and response times, system uptime, and user compliance with security policies. At my previous job, I introduced regular security audits and training sessions, which improved our threat detection rate by 25% in one year.”
9. Explain the role of encryption in cybersecurity.
Demonstrate your understanding of encryption and its importance in protecting data integrity and confidentiality. Discuss different types of encryption and their applications, such as SSL/TLS for web traffic and end-to-end encryption for messaging apps.
Possible answer: “Encryption serves as a fundamental pillar in cybersecurity, safeguarding data integrity and confidentiality against unauthorized access. Its significance lies in its ability to encode sensitive information, rendering it unreadable to anyone without the proper decryption key.
One prominent application of encryption is SSL/TLS, which secures web traffic by encrypting data exchanged between a user’s browser and a website’s server, thereby thwarting eavesdropping and data interception attempts. Additionally, end-to-end encryption, commonly utilized in messaging apps, ensures that only the sender and intended recipient possess the keys to decrypt messages, thus bolstering confidentiality and privacy.”
10. How do you ensure compliance with data protection regulations?
Show your knowledge of relevant regulations like GDPR, HIPAA, or CCPA and describe the steps you take to ensure your organization complies with these laws. Mention conducting audits, implementing data protection policies, and employee training programs.
Possible answer: “To ensure compliance, I stay updated with current regulations and implement comprehensive data protection strategies. At my previous job, I led a project to align our data handling processes with GDPR, which involved revamping our data storage practices and training staff on data privacy principles.”
- How to Conduct an Effective Cyber Threat Intelligence Stand-Up Meeting
- Avoiding Pitfalls: Top 10 Rookie Cybersecurity Career Mistakes
- Land Your First Junior Security Engineer Position
- How to Land Your First Job as a Junior Malware Analyst
- Landing a Junior Penetration Tester Position
11. What strategies do you use to mitigate the risk of insider threats?
Insider threats can be as damaging as external attacks. Discuss how you implement a combination of technical controls, employee training, and a culture of security to mitigate these risks.
Possible answer: “To mitigate insider threats, I advocate for a zero-trust security model, regular access audits, and continuous employee education on security best practices. At my last job, I used a system for monitoring unusual network activity, which helped us quickly identify and address a potential insider threat.”
12. Describe your experience with cloud security.
With many organizations moving to the cloud, this area is critical. Talk about your experience with cloud platforms like AWS, Azure, or Google Cloud, and discuss specific security measures you’ve implemented, such as identity and access management or encryption.
Possible answer: “In my previous role, I was responsible for migrating our data to AWS, ensuring all data was securely transferred and stored. I implemented strict access controls and regular security assessments to maintain a strong security posture in our cloud environment.”
13. How do you approach security awareness training for employees?
Explain your methods for educating non-technical staff on cybersecurity best practices. Discuss how you make training engaging and ensure information retention, such as through regular updates, quizzes, or interactive sessions.
Possible answer: “I believe in making security awareness training engaging and relevant. At my last job, we developed a monthly newsletter and hosted interactive workshops that covered current threats and best practices. This approach helped reduce phishing success rates by 50% among our staff.”
14. How do you balance business needs with security requirements?
This question addresses the often delicate balance between security and usability. Discuss how you work with other departments to ensure security measures do not hinder business operations while still protecting the organization’s assets.
Possible answer: “I collaborate closely with department heads to understand their operational needs and tailor security measures that provide robust protection without impeding business processes. For example, I could implement a secure file-sharing system that allows seamless collaboration while maintaining strict data security standards.”
15. What’s your experience with incident response plans? How do you test and update them?
Explain how you’ve developed or improved incident response plans and the importance of regular testing through drills or simulations. Discuss how you incorporate lessons learned from incidents and tests into plan updates.
Possible answer: “I’ve developed and refined incident response plans throughout my career, ensuring they are comprehensive and up-to-date. At my last job, I organized quarterly incident response drills, which helped identify gaps in our plan and improved our team’s response times significantly.”
16. How did you hear about this position?
When answering this question, it’s crucial to show your active interest and how you’re connected to the industry. Mention specific channels or networks that led you to the opportunity, reflecting your involvement in the cybersecurity community.
Possible answer: “I learned about this position through an online cybersecurity forum where professionals share opportunities, insights, and challenges. I’ve been an active member there for years, which keeps me well-informed about the latest trends and job openings in our field.”
17. Why do you want to work at this company?
Highlight unique aspects of the company that align with your skills and interests in cybersecurity. Show that you’ve done your homework and understand what makes the company special.
Possible answer: “I’ve always admired this company’s commitment to innovative cybersecurity solutions and its open approach to sharing knowledge within the community. Your recent whitepaper on cloud security challenges resonated with my experiences and the solutions I’ve applied in past roles.”
18. Why do you want this job?
Express your passion for cybersecurity and how the job aligns with your career goals. Mention specific aspects of the job that excite you and how they relate to your previous experiences.
Possible answer: “This role excites me because it emphasizes threat analysis and response, areas I’ve been deeply involved with in my previous job as a junior SOC analyst. I thrived on identifying and mitigating threats in real-time, and I’m eager to apply and expand those skills here.”
19. Why should we hire you?
Focus on your unique blend of skills, experiences, and perspectives. Highlight how they align with the needs of the team and contribute to the company’s cybersecurity goals.
Possible answer: “You should hire me because of my proven track record in threat detection and incident response. In my last role, I was frequently commended for my ability to identify subtle signs of system compromises, which prevented several potential data breaches.”
20. What can you bring to the company?
Discuss specific skills or perspectives you offer, and connect them to how they can help address current challenges the company faces. Reference any research you’ve done about the company’s current projects or objectives.
Possible answer: “I bring a strong background in network security and a fresh perspective on cybersecurity strategies. For example, I’ve extensively used behavioral analysis techniques to detect anomalies, which I understand aligns with your team’s focus on advanced threat detection methods.”
- How to Conduct an Effective Cyber Threat Intelligence Stand-Up Meeting
- Avoiding Pitfalls: Top 10 Rookie Cybersecurity Career Mistakes
- Land Your First Junior Security Engineer Position
- How to Land Your First Job as a Junior Malware Analyst
- Landing a Junior Penetration Tester Position
21. What are your greatest strengths?
Choose strengths that are most relevant to the role and provide examples from your work to illustrate them. This shows your self-awareness and ability to contribute positively.
Possible answer: “One of my greatest strengths is my analytical mindset, which has been crucial in identifying and resolving complex security vulnerabilities. In my role as a sys admin, I applied this skill to enhance our network monitoring systems, resulting in a 30% decrease in unnoticed security incidents.”
22. What do you consider to be your weaknesses?
Be honest but strategic; choose a weakness that is genuine but not critical to the role, and discuss how you are addressing it. This shows self-awareness and a commitment to professional growth.
Possible answer: “In the past, I’ve found public speaking to be challenging. However, recognizing its importance, especially in crisis communication, I’ve been actively seeking opportunities to present at team meetings and local cybersecurity meetups to improve my skills.”
23. What is your greatest professional achievement?
Select an achievement that is relevant and significant, and use it to demonstrate your contribution to cybersecurity. Describe the situation, your action, and the result, highlighting your role.
Possible answer: “My greatest achievement was leading a team response to a significant ransomware attack. By coordinating a swift and effective response, we minimized data loss and restored critical services within hours. This experience taught me the value of preparedness and teamwork in crisis situations.”
24. Tell me about a challenge or conflict you’ve faced at work, and how you dealt with it.
Choose a situation that demonstrates your problem-solving and interpersonal skills. Explain the challenge, how you addressed it, and what you learned from the experience.
Possible answer: “I once faced a conflict with a team member over the implementation of a new security protocol. We had differing opinions on the approach. I addressed this by initiating a meeting to discuss our viewpoints and finding common ground, leading to a more effective solution that combined our ideas.”
25. Tell me about a time you demonstrated leadership skills.
Even if you haven’t held a formal leadership position, you can discuss situations where you guided a project or led an initiative. Highlight your ability to inspire, motivate, and steer a group towards a common goal.
Possible answer: “During a critical system upgrade, I took the lead in organizing the team’s efforts, delegating tasks based on each member’s strengths, and ensuring open communication throughout the process. My leadership helped complete the upgrade ahead of schedule with no security lapses.”
26. What’s a time you disagreed with a decision that was made at work?
Discuss a situation where you professionally expressed a differing opinion and how you contributed to a constructive outcome. This shows your ability to think critically and work collaboratively.
Possible answer: “When my previous employer decided to postpone a security update due to budget constraints, I expressed my concerns about the potential risks. I presented a detailed risk assessment and alternative solutions, leading to a compromise where critical updates were implemented while non-essential ones were delayed.”
27. Tell me about a time you made a mistake.
Choose an example where you took ownership of a mistake and learned from it. This illustrates your integrity and ability to learn and grow from errors.
Possible answer: “Once, I misconfigured a firewall rule, accidentally allowing unauthorized access to a segment of our network. I immediately reported the mistake to my team, corrected the error, and conducted a thorough review to ensure there were no breaches. This incident taught me the importance of double-checking critical configurations and fostered a more collaborative approach to reviewing changes within our team.”
28. Tell me about a time you failed.
Select a failure that led to significant learning and personal or professional growth. Show how it has made you a better cybersecurity professional.
Possible answer: “In my early days as a junior SOC analyst, I failed to detect a spear-phishing campaign that resulted in a data breach. This was a tough lesson in the subtleties of cyber threats. I took it upon myself to develop a deeper understanding of email-based threats, leading to the development of new detection techniques that benefited the entire team.”
29. Why are you leaving your current job?
Provide a positive reason focused on career growth and learning opportunities. Avoid criticizing your current employer or colleagues.
Possible answer: “I’m seeking a new opportunity that offers broader responsibilities and more challenging scenarios in cybersecurity. While I’ve learned a great deal and enjoyed working with my current team, I feel I’m ready to take on more strategic security initiatives and lead larger projects.”
30. Why were you fired?
If applicable, be honest but brief, focusing on what you learned from the experience and how you have improved since then.
Possible answer: “I was let go from a position early in my career due to downsizing. While it was initially a setback, I used the experience to reflect on my career direction and focus more intently on cybersecurity, which has become my passion and main area of expertise.”
- How to Conduct an Effective Cyber Threat Intelligence Stand-Up Meeting
- Avoiding Pitfalls: Top 10 Rookie Cybersecurity Career Mistakes
- Land Your First Junior Security Engineer Position
- How to Land Your First Job as a Junior Malware Analyst
- Landing a Junior Penetration Tester Position
31. Why was there a gap in your employment?
Explain any gaps positively, focusing on constructive activities you engaged in during that time, such as further education, research, or volunteering.
Possible answer: “I took a career break to enhance my cybersecurity skills through a comprehensive certification program. This time allowed me to deepen my knowledge and return to the workforce with a stronger skill set and a fresh perspective.”
32. Can you explain why you changed career paths?
Discuss your transition as a strategic move to align more closely with your interests and strengths, particularly in cybersecurity.
Possible answer: “I shifted my career path from IT support to cybersecurity because I found my passion lies in solving complex security challenges and protecting organizational assets. The transition was a natural progression that allowed me to leverage my IT background while focusing on areas where I can make the most impact.”
33. What’s your current salary?
If applicable, share your current salary honestly but clarify your expectations are based on the market and the specific role.
Possible answer: “While I’m currently earning 45000 EUR, I understand the range for this type of role varies. I’m more interested in finding a position that’s a good fit and aligns with my expertise and career goals. I’m open to discussing what you believe is a fair compensation for this position.”
34. What do you like least about your job?
Focus on aspects unrelated to team dynamics or company culture, and instead discuss how you’re looking for more opportunities to grow, particularly in cybersecurity challenges.
Possible answer: “While I appreciate many aspects of my current role, I find that there are limited opportunities to tackle the kind of advanced cybersecurity challenges I’m passionate about. I’m seeking a role where I can further engage with cutting-edge security technologies and practices.”
35. What are you looking for in a new position?
Highlight aspects that are directly related to the role you’re applying for, showing your enthusiasm for specific responsibilities or the company’s approach to cybersecurity.
Possible answer: “I’m looking for a position where I can apply my skills in threat analysis and incident response more extensively. I’m particularly drawn to roles that allow for strategic development of security policies and hands-on problem-solving in a dynamic, collaborative environment.”
36. What type of work environment do you prefer?
Describe your ideal work environment in a way that aligns with the company’s known culture or values, emphasizing aspects like collaboration, innovation, and a commitment to security.
Possible answer: “I thrive in environments that foster continuous learning and collaboration among team members. A place where proactive security measures are valued, and everyone contributes to the cybersecurity posture. From my research, it seems your company values these principles, which excites me about the opportunity.”
37. What’s your work style?
Discuss your work style in a way that highlights your suitability for the role, focusing on characteristics important to cybersecurity, such as detail-oriented, analytical, and proactive.
Possible answer: “I’m very analytical and detail-oriented, which helps in identifying and mitigating intricate security vulnerabilities. I value clear communication and teamwork, as I believe sharing knowledge and strategies is crucial for effective cybersecurity.”
38. How would you deal with an insider threat detected in the company?
Describe your approach to handling sensitive situations involving insider threats. Emphasize your ability to act discreetly, assess the situation accurately, and implement measures to minimize damage while adhering to legal and ethical standards.
Possible answer: “In dealing with an insider threat, I prioritize confidentiality and swift action. For instance, in my previous role, we detected suspicious data access patterns. I immediately collaborated with the IT security team to monitor the activities without alerting the individual, gathering necessary evidence. We then followed our predefined protocol, which included involving the legal department and human resources to address the situation appropriately and ensure a fair process.”
39. Describe a time when you had to respond to a high-pressure security breach. How did you handle it?
Provide a specific example that shows your ability to remain calm under pressure, make quick and informed decisions, and effectively communicate with your team and stakeholders.
Possible answer: “In my last position, we experienced a ransomware attack that encrypted several critical systems. I led the incident response team, prioritizing the containment of the breach to prevent further spread. We then systematically restored services from backups. Throughout the process, I kept management and affected departments informed of our recovery plan and timelines. Post-incident, I conducted a review to identify the breach’s entry point, which led to strengthened security measures.”
40. Imagine you discover a significant vulnerability in your company’s main product just before a major release. What would you do?
Discuss how you would balance the need for security with business objectives, demonstrating your ability to make tough decisions and communicate effectively with different stakeholders.
Possible answer: “Upon discovering a significant vulnerability, my priority would be to assess the risk to customers and the company. In a similar situation at my previous job, I immediately informed the product and security teams to evaluate the impact. We decided to delay the release to fix the vulnerability, which I believe was in the best interest of our customers and the company’s reputation. I helped communicate the decision to stakeholders, explaining the reasoning and the steps we were taking to address the issue.”
- How to Conduct an Effective Cyber Threat Intelligence Stand-Up Meeting
- Avoiding Pitfalls: Top 10 Rookie Cybersecurity Career Mistakes
- Land Your First Junior Security Engineer Position
- How to Land Your First Job as a Junior Malware Analyst
- Landing a Junior Penetration Tester Position
41. How would you handle a situation where your team disagrees on the severity of a vulnerability?
Explain how you would facilitate a productive discussion, ensuring all viewpoints are considered and leading your team to a consensus or informed decision.
Possible answer: “When faced with differing opinions on a vulnerability’s severity, I encourage open discussion to understand each team member’s perspective. In a past situation, I facilitated a meeting where we listed the potential impacts and likelihoods, using our risk assessment framework. This approach helped us reach a consensus on the severity and decide on the appropriate mitigation actions.”
42. What would you do if you were refused the budget for a necessary security tool or update?
Describe how you would handle financial constraints while still maintaining security standards, demonstrating your ability to be resourceful and persuasive.
Possible answer: “If denied the budget for a necessary tool, I’d present a detailed case outlining the risks of not implementing the update, supported by data and potential cost comparisons of a breach. At my previous job, when faced with budget constraints, I identified alternative solutions and demonstrated how a smaller investment could still significantly reduce our risk, which eventually led to approval.”
43. Share an experience where you had to enforce security policies with resistant staff or departments. How did you handle it?
Highlight your communication and negotiation skills, as well as your firmness in upholding security standards, demonstrating your ability to manage interpersonal conflict while maintaining a secure environment.
Possible answer: “In my previous role, I encountered resistance when implementing new password policies. I addressed this by explaining the reasoning and potential consequences of non-compliance in a series of staff meetings. I also provided training and resources to help staff adapt. By making the process transparent and supportive, we successfully transitioned to the new policies with minimal pushback.”
44. How would you proceed if you noticed unusual network activity, but there were no immediate signs of a breach?
Discuss your proactive approach to potential threats, emphasizing your attention to detail and thorough investigation skills.
Possible answer: “When noticing unusual network activity, I immediately initiate a preliminary investigation to assess the scope and potential impact, without jumping to conclusions. For example, I once noticed irregular traffic patterns and, by closely monitoring and analyzing the data, identified a misconfigured internal tool, not a breach. This incident reinforced the importance of vigilance and thoroughness in even seemingly minor anomalies.”
45. Describe how you have contributed to creating a security-conscious culture in your previous roles.
Explain your strategies for fostering an environment where security is everyone’s responsibility, showcasing your ability to lead by example and engage with employees at all levels.
Possible answer: “In my last role, I spearheaded a ‘Security Champion’ program, identifying individuals in different departments who could disseminate security best practices among their peers. I organized regular training sessions and created engaging content, such as newsletters and quizzes, to keep security at the forefront of everyone’s minds. This approach significantly improved our security posture by empowering employees to take an active role in cybersecurity.”
46. What other companies are you interviewing with?
While maintaining professionalism and confidentiality, share your job search status in a way that emphasizes your interest in the cybersecurity field without revealing specific company names or details.
Possible answer: “I am exploring a few opportunities within the cybersecurity sector that align with my skills and career goals. However, I am particularly interested in this role due to your company’s innovative approach to security challenges and commitment to advancing cybersecurity practices.”
47. What makes you unique?
Highlight a combination of your technical skills, personal attributes, and experiences that distinguish you from other candidates, focusing on those most relevant to the cybersecurity field.
Possible answer: “What makes me unique is my blend of experience in system administration and SOC analysis, coupled with my proactive approach to threat detection and passion for educating others about cybersecurity. I’ve also developed a unique method for analyzing network traffic patterns that has proven effective in identifying threats earlier than traditional methods.”
48. What should I know that’s not on your resume?
Discuss any relevant experiences, personal projects, or interests that demonstrate your dedication to cybersecurity, your willingness to go above and beyond, or your ability to bring a fresh perspective to the team.
Possible answer: “One thing not reflected in my resume is my involvement in an online cybersecurity community where I regularly contribute to discussions and write articles on emerging threats and defense strategies. This engagement keeps me at the cutting edge of cybersecurity trends and practices, enriching my professional skills and network.”
49. What would your first few months look like in this role?
Outline your plan for starting strong in the role, including how you would familiarize yourself with the company’s systems, culture, and security challenges, as well as any initial goals or projects you would like to tackle.
Possible answer: “In the first few months, I plan to immerse myself in understanding your security infrastructure, assessing existing protocols, and identifying areas for improvement. I’d also like to establish strong relationships with the IT and security teams and begin contributing to ongoing projects. My goal is to quickly become a productive and proactive member of your security team, bringing fresh insights and strategies to enhance our defense mechanisms.”
50. What are your salary expectations?
Do your research on typical salary ranges for the position and location, and provide a range based on your experience and the market. Be open to negotiation based on the total compensation package.
Possible answer: “Based on my research and my experience in the field, I’m looking for a salary in the range of 52000 to 59000 EUR. However, I am flexible and open to discussing the entire compensation package, including benefits and growth opportunities.”
- How to Conduct an Effective Cyber Threat Intelligence Stand-Up Meeting
- Avoiding Pitfalls: Top 10 Rookie Cybersecurity Career Mistakes
- Land Your First Junior Security Engineer Position
- How to Land Your First Job as a Junior Malware Analyst
- Landing a Junior Penetration Tester Position
51. What do you think we could do better or differently?
Answer this question carefully, framing any criticisms constructively and balancing them with positive observations. Offer suggestions that demonstrate your understanding of cybersecurity best practices and how they might apply to the company.
Possible answer: “From what I’ve seen, your company has a strong commitment to cybersecurity. One area for potential enhancement could be in user education and awareness. A more comprehensive, engaging training program could further strengthen your security posture by empowering employees to recognize and respond to threats more effectively.”
52. When can you start?
Be honest about any existing commitments but show your enthusiasm and readiness to begin contributing to the company. If possible, provide a specific start date.
Possible answer: “I am eager to start contributing to your team and can be available to begin within two weeks after receiving an offer, allowing time to responsibly conclude my current projects and transition from my current role.”
53. Are you willing to relocate?
Be clear about your willingness and any limitations regarding relocation, considering personal circumstances and the opportunity presented by the role.
Possible answer: “I am open to relocation for the right opportunity, especially one that aligns as closely with my career goals and interests in cybersecurity as this position does. I would be eager to discuss the details and support available for the relocation process.”
Watch on Youtube
- Job Interview: Incident Responder
- Job Interview: Security Consultant
- Job Interview: Cybersecurity Threat Intelligence Analyst Role
- Worst Cybersecurity Job Interview Ever – SOC Analyst
More Cyber
