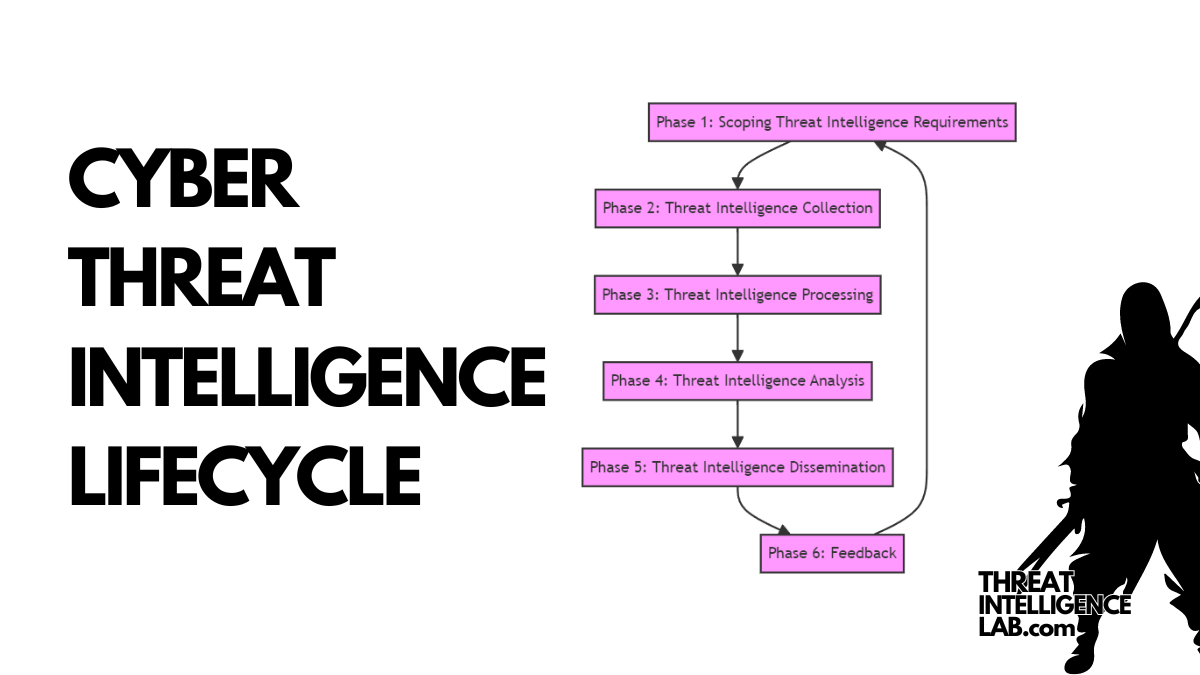
As someone entrenched in the world of cybersecurity and threat intelligence, I’ve seen firsthand the critical role that a structured Threat Intelligence Lifecycle plays in safeguarding organizations.
From identifying what information is necessary, to collecting, processing, and analyzing data, each phase is pivotal.
Let’s dissect this lifecycle to understand how it can be a game-changer for your cybersecurity posture.
The Threat Intelligence Lifecycle
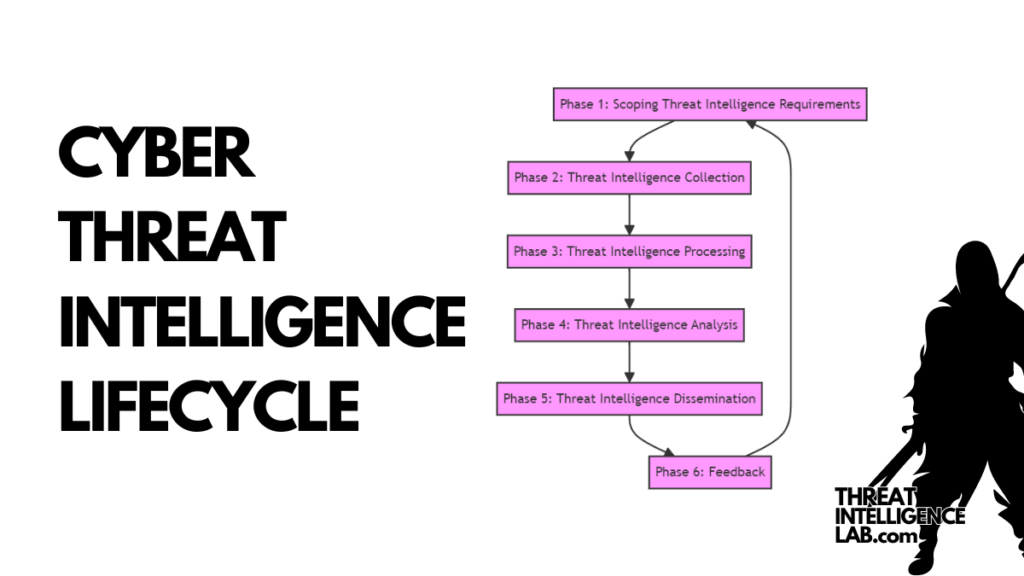
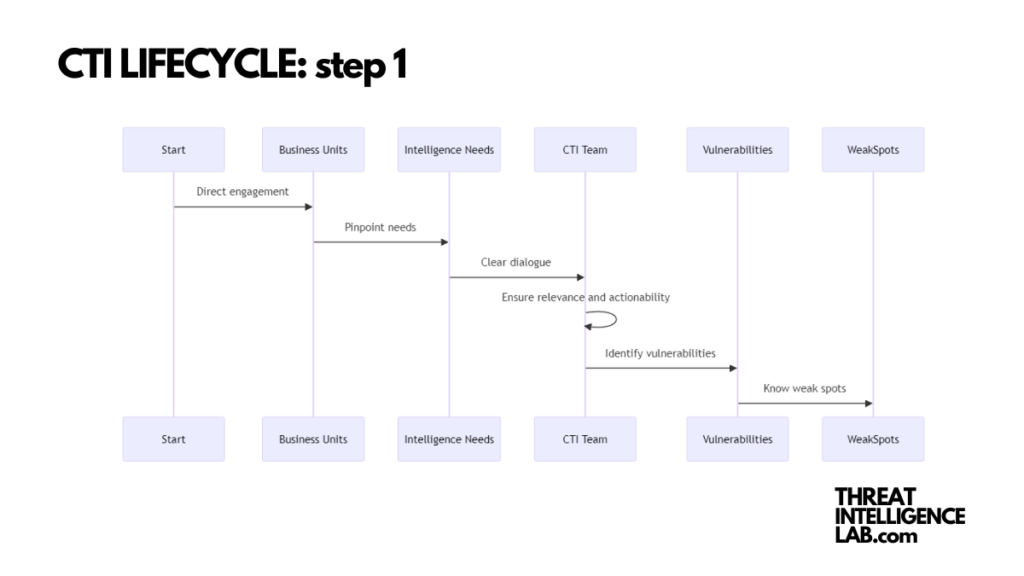
Phase 1: Scoping Threat Intelligence Requirements
In my experience, effective threat intelligence always starts with clear requirements. Imagine we’re focusing on safeguarding healthcare organizations from initial access brokers in the dark web.
The first step? Direct engagement with various business units to pinpoint intelligence needs.
This initial scoping is not about diving straight into the data but understanding what you’re looking for and why. It’s about setting the stage for targeted, meaningful intelligence gathering that aligns with your organization’s risk management goals.
I recommend starting with a clear dialogue between your CTI team and other departments to ensure the intelligence collected is both relevant and actionable.
Identifying threats like initial access brokers requires an in-depth understanding of your company’s vulnerabilities – know your weak spots to know what to look for.
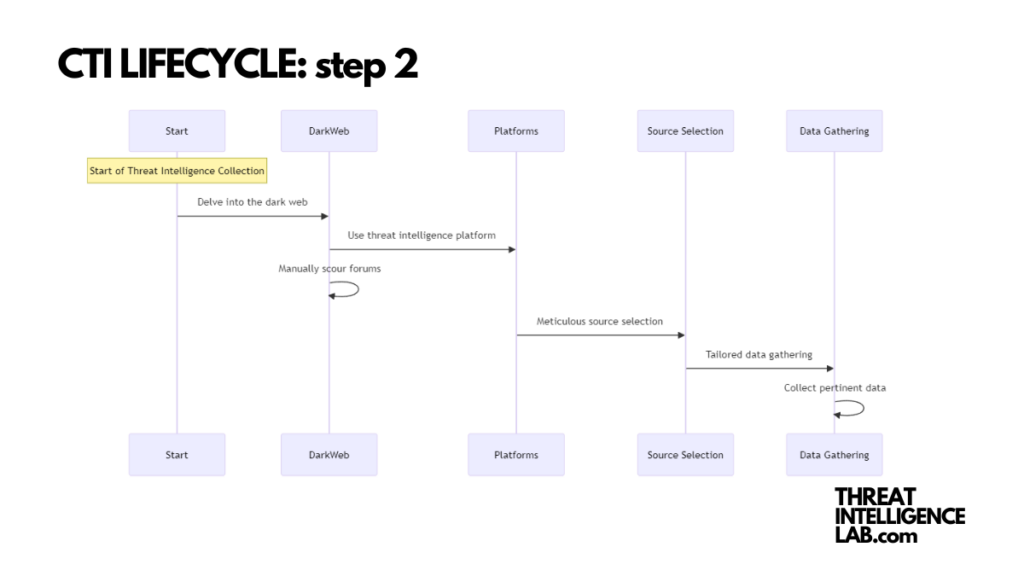
Phase 2: Threat Intelligence Collection
Here’s where the rubber meets the road. For our hypothetical healthcare company, this means delving into the murky waters of the dark web to track down those initial access brokers.
Whether you’re using a sophisticated threat intelligence platform or manually scouring through forums, the goal remains the same: collect pertinent data without getting bogged down by the noise.
- Why Data Breach Report Feeds Are Important
- The Top 10 Essential Log Sources for IT Monitoring
- Dark Web Cybercrime Forums You Should Monitor
- How to Parse and Use VirusTotal feeds
- Getting The Most Out Of URLscan.io
The best way to achieve results here is through meticulous source selection and data gathering, tailored to the specifics identified in Phase 1. It’s a challenging journey through a sea of information, but with the right tools and focus, you can navigate it effectively.
Phase 3: Threat Intelligence Processing
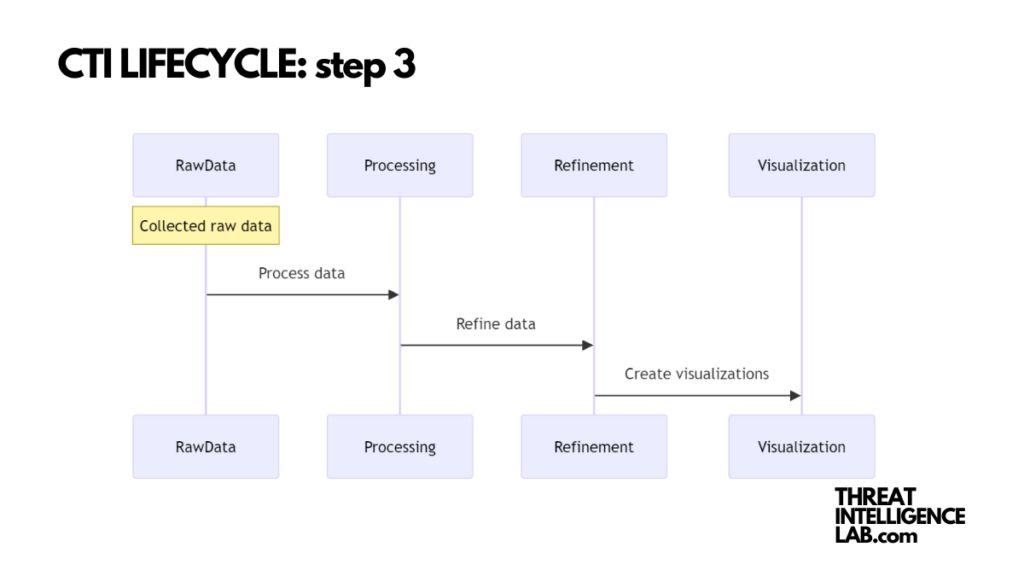
Having collected raw data, the next step is to make sense of it. This is where processing comes in, transforming chaotic information into structured, analyzable chunks.
Think of it like refining ore into gold; you’re filtering out the irrelevant to spotlight the valuable.
In practice, this could mean creating spreadsheets, databases, or visualizations that link different pieces of data.
For instance, mapping out the connections between various initial access brokers and their methods can provide clear, actionable insights. Remember, the aim is to prepare the data for in-depth analysis, so accuracy and clarity are key.
Phase 4: Threat Intelligence Analysis
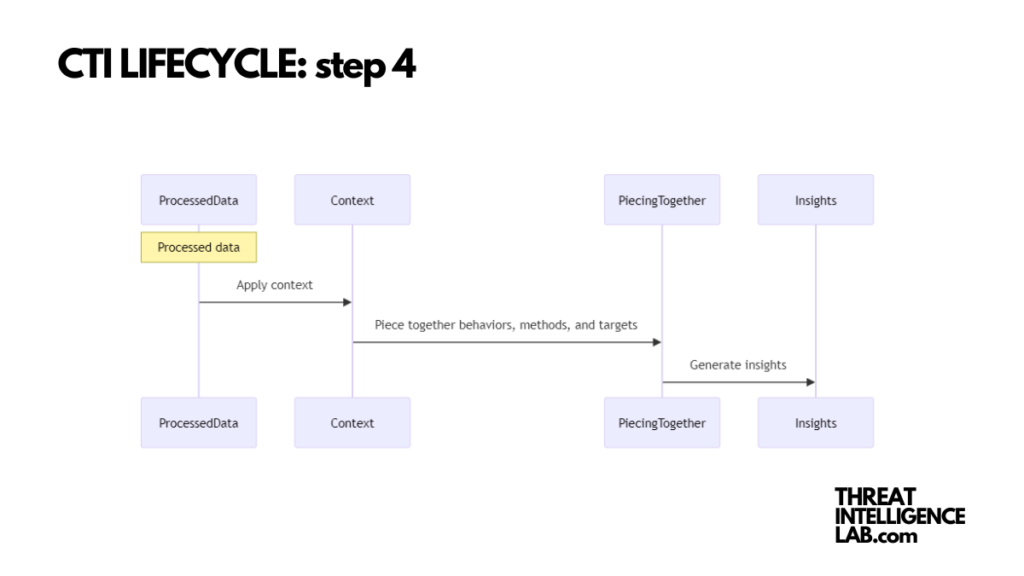
Now, we dive deeper. Analysis is about turning processed data into intelligence that can drive decisions.
It’s the phase where context is king. For our healthcare scenario, this would involve piecing together the behaviors, methods, and targets of initial access brokers to understand the threat landscape fully.
Effective analysis speaks directly to the needs identified earlier. It’s not just about presenting data; it’s about delivering insights that can inform real-world decisions. Always aim to provide clear, actionable recommendations tailored to the specific audience within your organization.
Phase 5: Threat Intelligence Dissemination
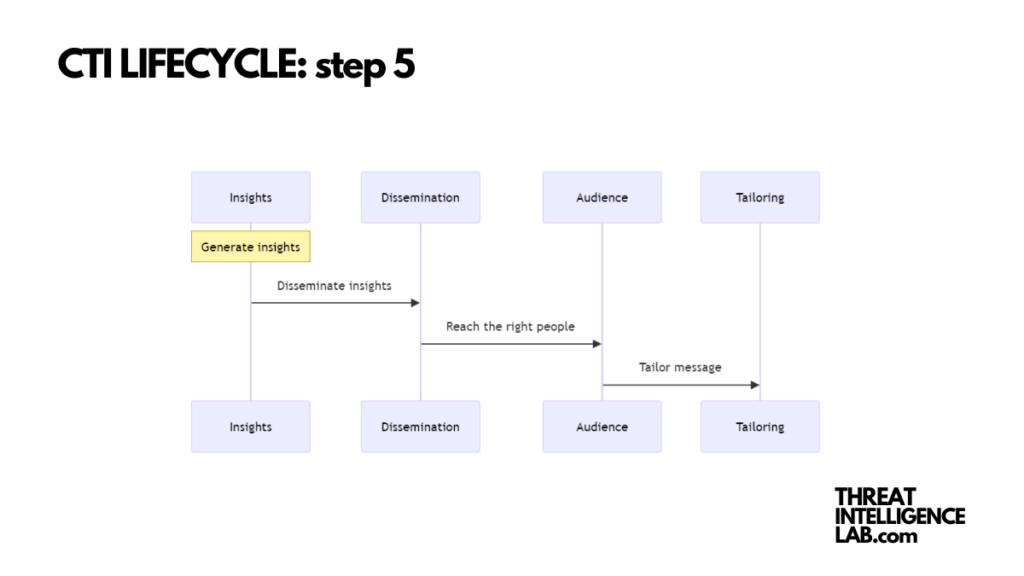
What good is intelligence if it doesn’t reach the right people? Dissemination is about ensuring that the insights you’ve worked hard to uncover are delivered to those who can act on them.
This might mean creating different versions of your findings to cater to technical teams, executives, or risk management.
The best dissemination practices involve knowing your audience and tailoring the message accordingly. Make sure that the intelligence you provide is actionable and understandable, regardless of the technical expertise of the end-user.
Phase 6: Feedback
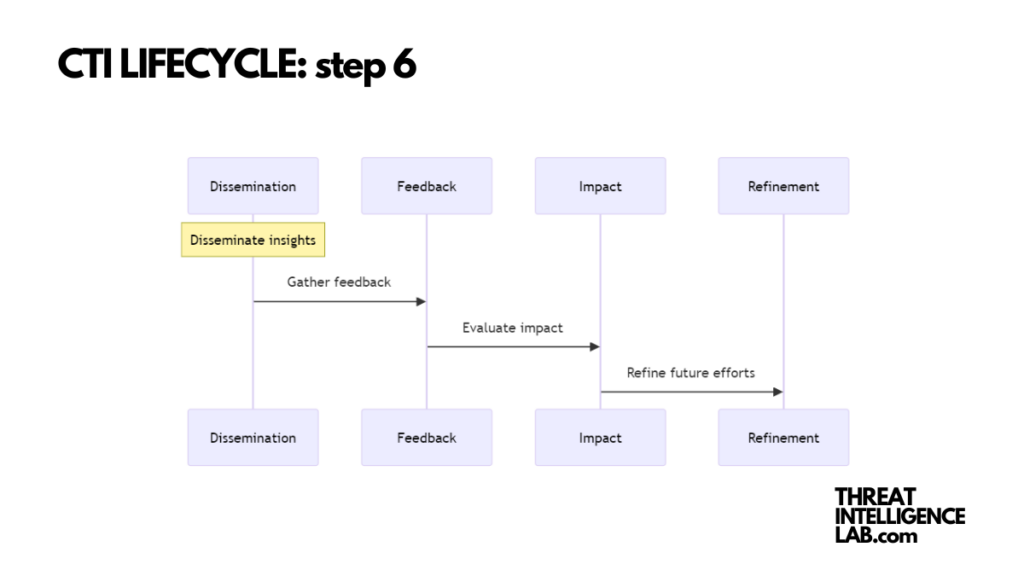
Finally, the lifecycle doesn’t end with dissemination; feedback is essential.
This is where you learn whether the intelligence provided has made a real impact.
Did it help reduce risks? Was it actionable? Gathering feedback helps refine future intelligence efforts, ensuring they are as effective and relevant as possible.
I recommend establishing clear channels for feedback and encouraging a culture of open communication. Only by understanding the effectiveness of your efforts can you truly enhance your organization’s cybersecurity posture.
To conclude
In conclusion, navigating through the Threat Intelligence Lifecycle is no small feat, but it’s essential for modern cybersecurity defenses.
By understanding and implementing each phase effectively, you can provide your organization with the insights needed to stay one step ahead of cyber threats.
Remember, threat intelligence is a continuous journey, one that requires diligence, precision, and constant evolution.