As a cybersecurity and threat intelligence expert, you want to have a well-prepared incident response team.
One effective way to enhance this preparedness is through scenario-based training.
Let’s delve into this method and understand its significance, design, evaluation, and additional considerations for your team’s development.
Scenario-Based Training for Incident Response Teams
Scenario-based training is a form of experiential learning where your team engages in simulations that mirror real-world cyber incidents1.
These scenarios, crafted from actual or hypothetical cases, aim to test and enhance your team’s skills in incident response.
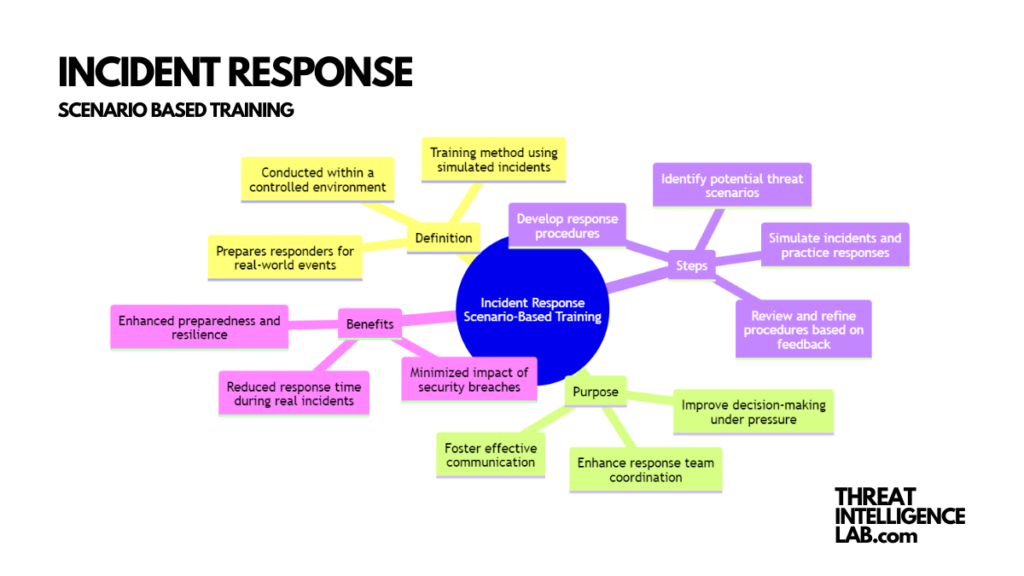
They focus on aspects such as knowledge application, communication, decision-making, and collaboration.
This type of training, adaptable to live, virtual, or hybrid environments, provides a hands-on approach to learning, significantly different from traditional, theory-based education methods2.
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
- The Cyber Threat Intelligence Capability Maturity Model (CTI-CMM)
Why is Scenario-Based Training Beneficial?
I recommend scenario-based training for numerous reasons.
Firstly, it increases engagement and motivation by immersing team members in realistic situations.
This approach not only enhances performance and confidence but also leads to better retention and transfer of knowledge.
By preparing your team for unexpected situations, scenario-based training bolsters their ability to adapt to different scenarios, enhancing their situational awareness and critical thinking skills. Importantly, it also teaches them to manage stress and ambiguity effectively.
How to Design Scenario-Based Training?
Designing impactful scenario-based training starts with defining clear learning objectives tailored to your team’s needs and the specific cyber threats your organization faces.
These objectives should guide the development of realistic and relevant scenarios. Diversity in these scenarios ensures comprehensive exposure to various potential incidents3.
Moreover, incorporating interactive elements and technology, such as simulation tools and logs, enhances the realism and engagement of the training.
How to Evaluate Scenario-Based Training?
Evaluating the effectiveness of scenario-based training is essential.
This involves assessing your team’s performance against predefined criteria and gathering their feedback on the training experience.
Performance metrics should include response time, decision-making accuracy, and scenario resolution effectiveness.
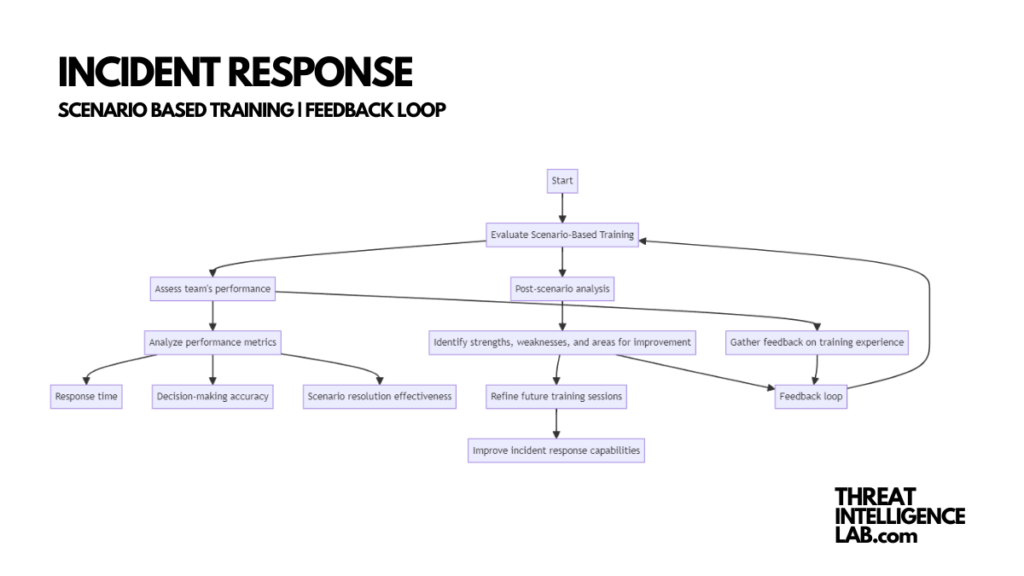
Additionally, post-scenario analysis is crucial for identifying strengths, weaknesses, and areas for improvement.
Using this feedback, you can refine future training sessions to better meet your team’s needs and improve their incident response capabilities.
Here’s What Else to Consider
While scenario-based training significantly benefits incident response teams, remember that cybersecurity threats continuously evolve.
Therefore, it’s crucial to update and tailor training scenarios4 regularly to reflect the latest threats and real-world events.
Moreover, cross-training across different departments can enhance the overall cybersecurity culture within your organization.
Everyone, from IT to accounting5, should be aware of and prepared for potential cyber incidents.
- How to Conduct an Effective Cyber Threat Intelligence Stand-Up Meeting
- Avoiding Pitfalls: Top 10 Rookie Cybersecurity Career Mistakes
- Land Your First Junior Security Engineer Position
- How to Land Your First Job as a Junior Malware Analyst
- Landing a Junior Penetration Tester Position
FAQs
- https://www.emerald.com/insight/content/doi/10.1108/ICS-05-2022-0085/full/html?skipTracking=true ↩︎
- https://www.cisa.gov/sites/default/files/publications/Cybersecurity-Tabletop-Exercise-Tips_508c.pdf ↩︎
- https://assets.ey.com/content/dam/ey-sites/ey-com/en_gl/topics/advisory/ey-cybersecurity-incident-simulation-exercises-scored.pdf?download ↩︎
- https://www.first.org/resources/papers/amsterdam23/Democratizing-Incident-Response-Tabletop-Exercises.pdf ↩︎
- https://www.mitre.org/sites/default/files/2022-09/pr_14-3929-cyber-exercise-playbook%20.pdf ↩︎

