We know that the misuse of Remote Desktop Protocol (RDP) and similar services can open the door to a plethora of cyber threats.
Let’s discuss how strictly limiting the use of RDP can significantly enhance your organization’s cybersecurity posture.
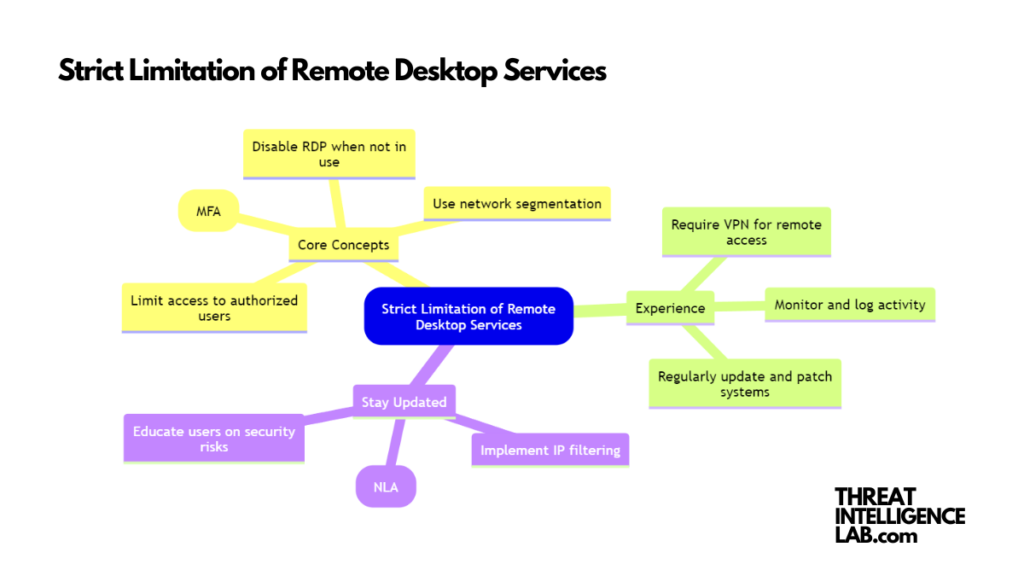
1. The Crucial Step: Disabling RDP
The first and most fundamental step is to disable RDP when it’s not in use.
Keeping RDP or other remote desktop services inactive by default minimizes the chances of unauthorized access. Activate these services only when absolutely necessary for business functions. Remember, every service that’s not in use but left running is a potential gateway for attackers.
2. Segment Your Network Wisely
Network segmentation is a game-changer. By isolating systems that require remote access from the rest of your network, you can contain breaches more effectively.
This strategy ensures that even if attackers compromise one segment, they can’t easily traverse to other parts of your network. I recommend considering this as a critical part of your defense strategy.
3. Enforce Strong Authentication
It’s time to move beyond just usernames and passwords. Implement multi-factor authentication (MFA) for anyone accessing remote desktop services. MFA acts as a robust barrier, adding an extra verification step. This significantly reduces the likelihood of unauthorized access, as attackers would need more than just stolen credentials.
4. Limit Access with Precision
Not everyone needs access to everything. Restrict remote desktop services to users who genuinely need it for their specific job tasks. Implementing role-based access controls (RBAC) helps ensure that individuals have access only to the resources essential for their roles. This not only tightens security but also simplifies management.
5. Incorporate VPNs into Your Security Stack
Before allowing access to remote desktop services, require users to connect through a virtual private network (VPN). VPNs encrypt data transmission, creating a secure tunnel between the user’s device and your network. This extra layer of encryption greatly enhances security, particularly for remote connections.
6. Stay Vigilant: Monitor and Log Activity
Monitoring and logging remote desktop sessions is non-negotiable. Implement mechanisms to track activity and flag any unusual behavior.
Regularly reviewing logs allows you to spot anomalies and respond swiftly. It’s crucial to establish a baseline of normal activity so that deviations can be detected promptly.
7. Regular Updates: A Necessity, Not an Option
Cybercriminals exploit vulnerabilities in outdated systems. Therefore, ensure all devices using remote desktop services are updated with the latest security patches.
This is a continuous process, as new vulnerabilities are discovered regularly.
Keeping your systems updated closes these gaps and fortifies your defenses.
- BianLian Ransomware Group: A Rising Threat in Cybercrime
- The Black Basta Cyber Threat
- Rhysida Ransomware Group
- The Akira Ransomware Gang
- Cl0p Ransomware Gang: The Unseen Cyber Menace
8. Leverage Network Level Authentication (NLA)
NLA is your first line of defense for RDP servers.
By requiring users to authenticate before establishing a full remote desktop session, NLA significantly reduces the risk of unauthorized access.
This pre-connection authentication ensures that only authorized users can make remote desktop connections.
9. Implement IP Filtering
IP filtering allows you to specify which IP addresses or ranges can access remote desktop services.
By restricting access to known, trusted IPs, you can significantly reduce the risk of attacks from external sources. While not infallible, IP filtering adds another layer of security to your remote access strategies.
10. User Education
Lastly, user education is paramount. Conduct regular training sessions to inform your staff about the risks associated with remote desktop services and how to use them securely.
Empower your users to recognize and report suspicious activities. A well-informed user is often the best defense against cyber threats.
- Why Data Breach Report Feeds Are Important
- The Top 10 Essential Log Sources for IT Monitoring
- Dark Web Cybercrime Forums You Should Monitor
- How to Parse and Use VirusTotal feeds
- Getting The Most Out Of URLscan.io
To conclude
By implementing these measures, you can significantly reduce the vulnerabilities associated with RDP and other remote desktop services.
Each step is a building block towards a more secure and resilient cybersecurity framework. Remember, in the realm of cybersecurity, being proactive is always better than being reactive.

