Your cart is currently empty!
Combatting Malware through Windows Scheduled Task Monitoring
Windows Scheduled Tasks are not merely background processes; they are keystones of system integrity and security.
Today, I’ll dissect the critical importance of specific Windows event IDs—4698, 4699, 4701, and 4702.
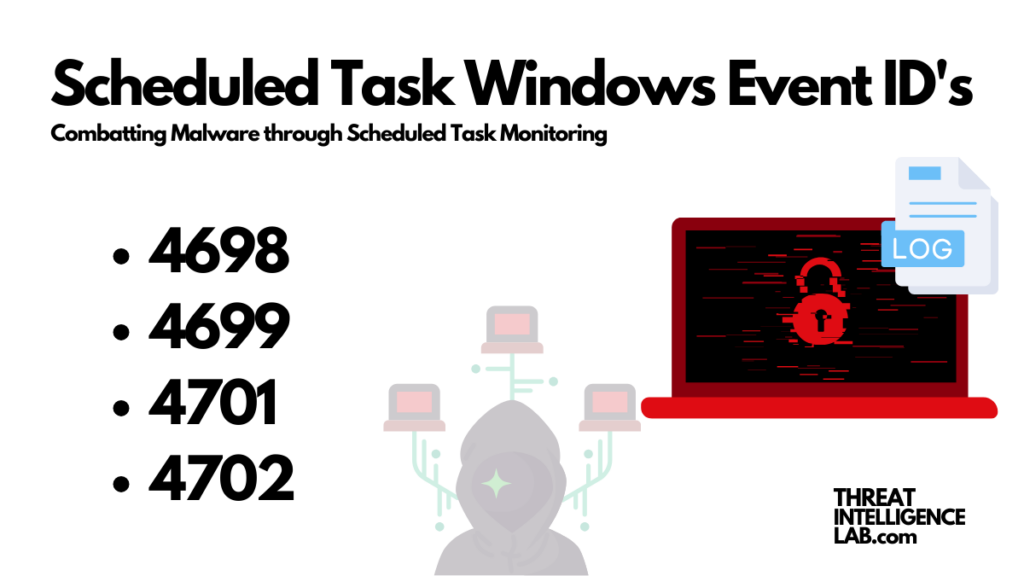
These IDs are far from being mundane logs. Instead, they represent a rich vein of information for incident responders keen on detecting and mitigating threats with efficiency.
Important Windows Scheduled Task Event ID’s
Adapt a monitoring strategy
To make the most of these event IDs, incorporating them into a comprehensive security monitoring strategy is advisable. I recommend setting up specific alerts for these events and crafting a detailed investigation protocol.
This proactive approach allows for the swift identification and mitigation of threats related to unauthorized or malicious changes in scheduled tasks.
How to enable logging with a maximum log size
In this part I will quickly guide you on how to enable native logging so you can keep track of the Event IDs like 4698 and 4701.

Enable Windows Scheduled Task logging
- Press the Windows key on your keyboard or click on the Start menu and type “
eventvwr.msc” into the search bar. - Press Enter or click on the “Event Viewer” result to open it.
- In the Event Viewer window, on the left-hand pane, navigate to “Windows Logs.”
- Right-click on “Security” log and select “Properties” from the context menu.
- In the “Security Properties” window:
- Make sure the “Enable logging” checkbox is checked.
- Adjust the “
Maximum log size” to at least 1GB. - Set the “Retention method for security log” to “Overwrite events as needed.”
- Click “OK” to save the changes.
- Close the Event Viewer window.
Search the logs
- Press the Windows key on your keyboard or click on the Start menu and type “
eventvwr.msc” into the search bar. - Press Enter or click on the “Event Viewer” result to open it.
- In the Event Viewer window, on the left-hand pane, navigate to “Windows Logs” again.
- Click on “Security” log to select it.
- In the Actions pane on the right-hand side, click on “Filter Current Log…”
- In the “Filter Current Log” window:
- Click on the “XML” tab.
- Check the “Edit query manually” checkbox.
- Paste the following XML query:
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[System[(EventID=4698 or EventID=4701)]]</Select>
</Query>
</QueryList>
- Click “OK” to apply the filter.
- You will now see a list of events with Event ID 4698 and 4701.
- Happy hunting!
Conclusion
Understanding the nuances of Windows Scheduled Tasks and the events associated with them is crucial for maintaining system security.
By paying close attention to these events and conducting thorough investigations, incident responders can gain valuable insights into system behavior. Consequently, they can identify threats early, enabling them to take decisive action to protect their networks.
Remember, the best way to ensure system security is by staying vigilant and proactive in monitoring and analyzing system events. Consequently, you can swiftly detect and mitigate potential threats, safeguarding your network effectively.
