Your cart is currently empty!
Tools
Try out our home made threat intelligence tools. Elevate your cyber capabilities with a single click on a button.
-

Certiscope – Simplifying SSL/TLS Certificate Monitoring
Certiscope is your go-to solution for real-time insights into SSL/TLS certificates. Built in the Netherlands by Threat Intelligence Lab, Certiscope empowers organizations to track domain activity, spot malicious patterns, and protect their digital presence effortlessly. API powered Just connect with our API. Done correct We gladly explain how we do it. Fast It is super…
-

The Cyber Threat Intelligence Capability Maturity Model (CTI-CMM)
In the ever-evolving landscape of cyber threats, organizations need a solid framework to assess and enhance their cyber threat intelligence (CTI) capabilities. Enter the Cyber Threat Intelligence Capability Maturity Model (CTI-CMM), a powerful tool designed to help organizations evaluate their current CTI practices, set ambitious goals for improvement, and benchmark their performance against industry standards.…
-

Using YARA for Malware Analysis
I’ve used this tool in various scenarios, and its utility cannot be overstated. So, what exactly is YARA, and how is it utilized in cybersecurity? What is YARA? YARA, which stands for “Yet Another Recursive Acronym” is an open-source tool designed to help researchers identify and classify malware. Victor Alvarez of VirusTotal created YARA in…
-

Incident Response Information Sharing with IRIS
IRIS stands for Incident Response Information Sharing. It’s a collaborative platform specifically designed for incident response analysts. The platform facilitates the sharing of technical investigations efficiently and effectively. Whether you’re stationed in a secure operations center or conducting field investigations, IRIS adapts to your needs. How IRIS Enhances Incident Response IRIS significantly streamlines the incident…
-
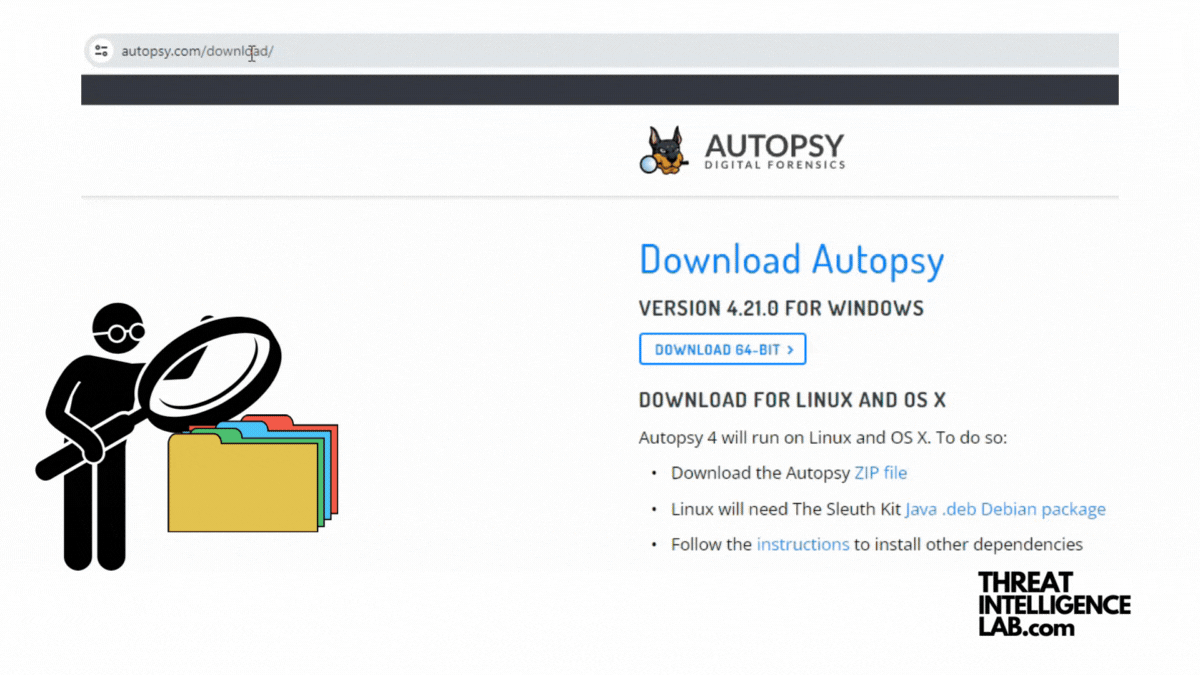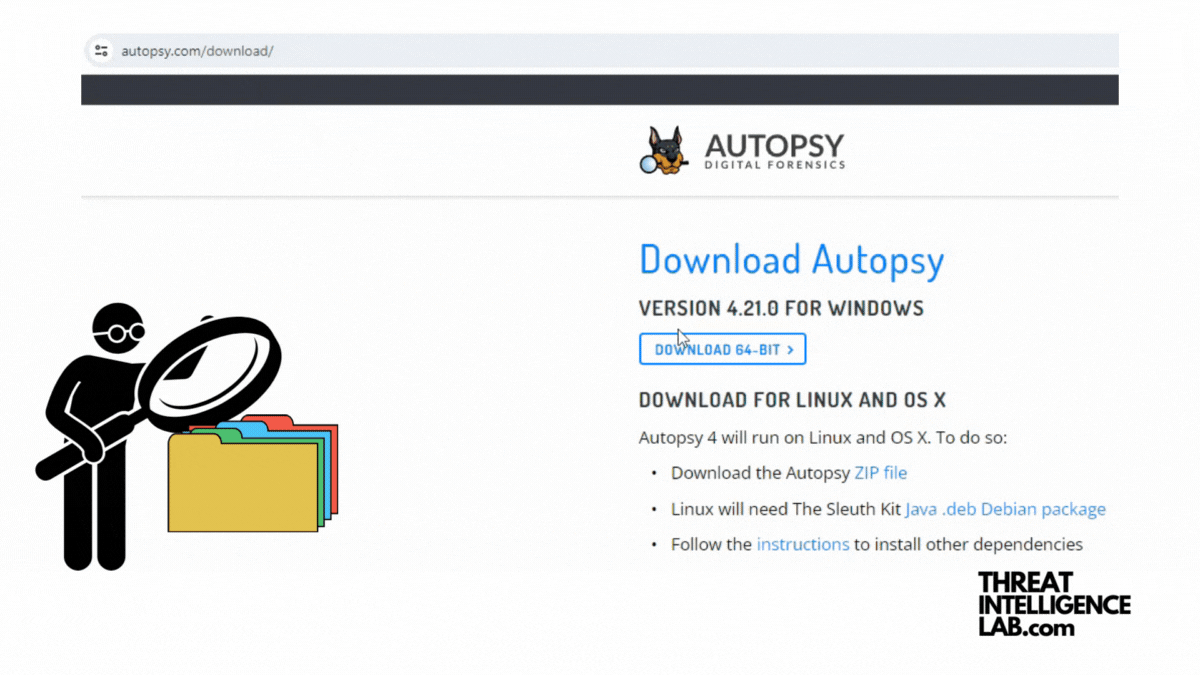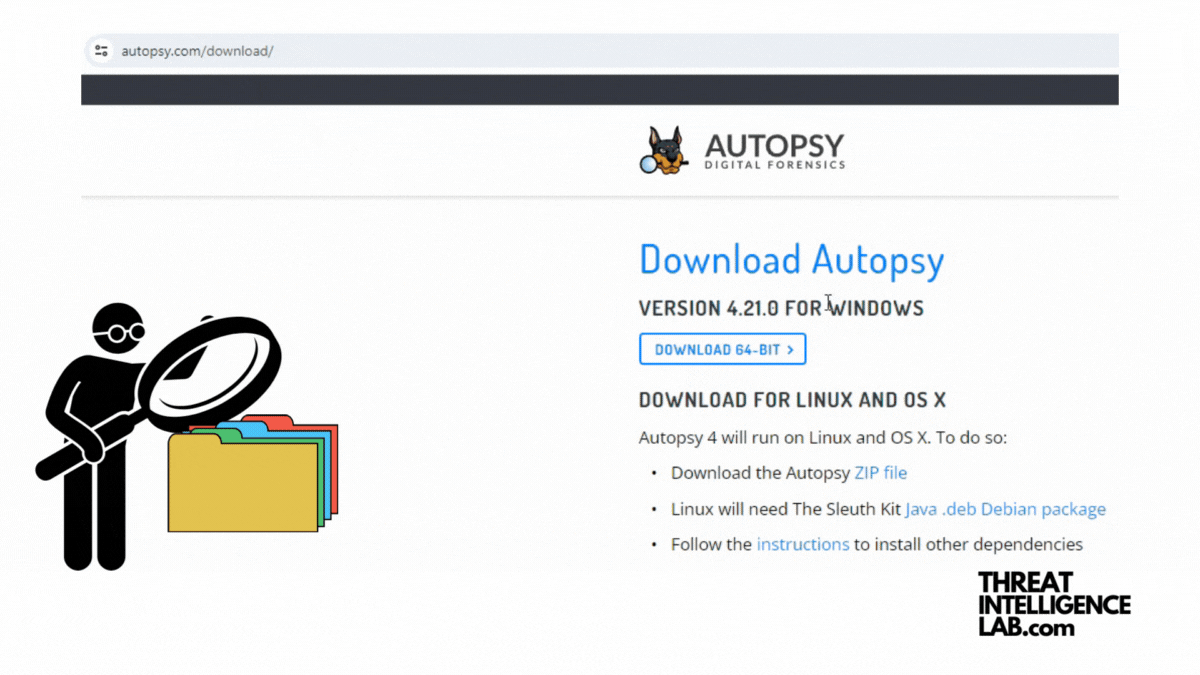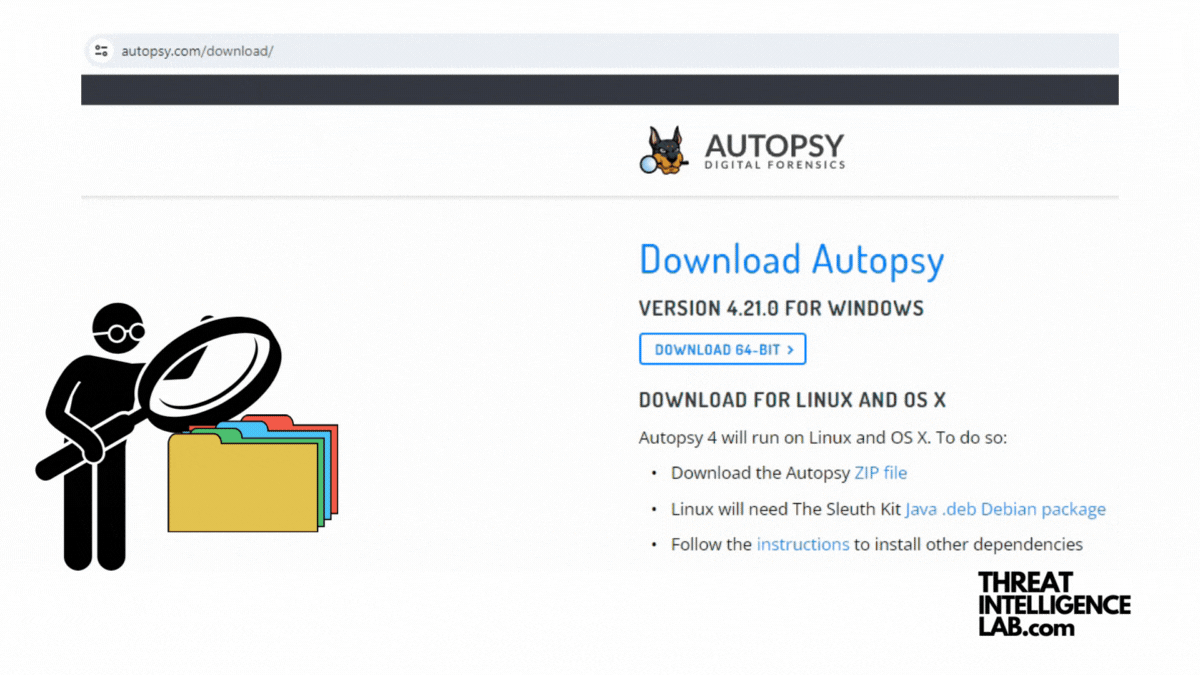
Introduction to Disk Analysis Using Autopsy
Today, I’ll take you through Autopsy, a comprehensive digital forensics platform. Autopsy is made for analyzing disk images, recovering deleted files, and uncovering user activities. Installing Autopsy on Windows Prerequisites Step-by-Step Installation Installing Autopsy on Linux Prerequisites Step-by-Step Installation Installing Older Versions You can find other versions of Autopsy at: Starting up 1. Setting Up…
-

Step-by-Step Guide to Forensically Acquiring Logs with KAPE
Forensic log acquisition is a crucial step in digital forensics and incident response. KAPE, developed by Kroll, is a powerful, lightweight tool designed for this purpose. Let’s break down the process of using KAPE to acquire logs from laptops, desktops, and remote systems in a detailed, step-by-step manner. Step 1: Preparing for KAPE Deployment Step…
-
Phishing Checklist
Here are 25 key warning signs to be on the lookout for when you encounter a potentially malicious email. Master the art of phishing detection and make sure to have this essential checklist readily available at your workspace. How to use the Phishing Checklist Phishing Checklist Tool I’m excited to introduce you to the free…
-

Try Out This CTI powered AI
We have been playing with ChatGPT and we decided to create our own GPT dubbed ‘Cyber Threat Intelligence AI‘. This awesome AI will search the web and gather actionable cyber threat intelligence for you. Help us, we have been hit by Lockbit We asked it to help, as we told it we had been hit…
