I’ve used this tool in various scenarios, and its utility cannot be overstated. So, what exactly is YARA, and how is it utilized in cybersecurity?
What is YARA?
YARA, which stands for “Yet Another Recursive Acronym” is an open-source tool designed to help researchers identify and classify malware.
Victor Alvarez of VirusTotal created YARA in 2009. Since then, it has become a standard tool for cybersecurity professionals. With YARA, users can create descriptions of malware families based on textual or binary patterns.
How Does It Work?
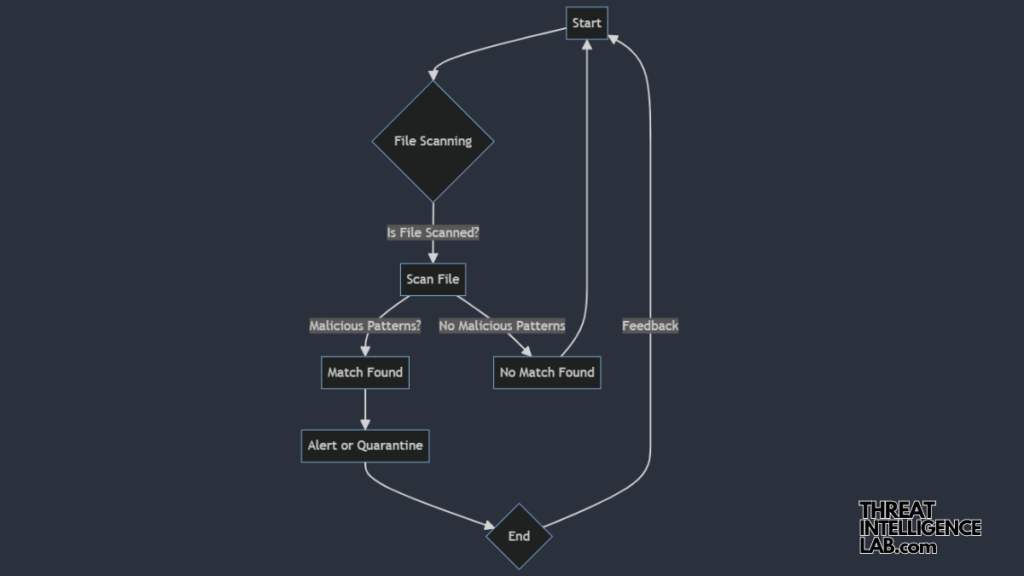
It operates using rules that describe patterns in file signatures, allowing you to identify malicious files based on specific characteristics.
These rules use a flexible, Python-like syntax, making them accessible even to those new to programming.
rule example_rule : TIL-banker
{
meta:
description = "This is just an example"
threat_level = 1
in_the_wild = true
strings:
$a = {somemalwarestring}
$b = {some-other-string}
$c = "ABCDEFGH_mutex"
condition:
$a or $b or $c
}Here’s a simple breakdown of how it works:
- Define Rules: You create detection rules to specify the characteristics of files you want to detect. These rules can include text strings, hexadecimal patterns, and file size constraints.
- Scan Files: YARA scans files or directories, looking for matches to the rules.
- Identify Threats: When a file matches a rule, YARA flags it for further analysis.
Usage in Cybersecurity
YARA’s versatility makes it useful in various cybersecurity tasks, from malware research to incident response.
Here are some practical applications:
Malware Detection and Classification
YARA excels at detecting and classifying malware. When you discover a new malware variant, you can write new rules based on its unique characteristics.
Once you apply these rules, you can quickly identify other instances of the same or similar malware. This helps you understand the spread and impact of the threat.
Incident Response
During an incident response, time is critical. One way to rapidly identify malicious files and understand the scope of an attack is by deploying YARA rules. This allows you to quickly find and isolate infected files, reducing potential damage to the organization.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- The Cyber Threat Intelligence Capability Maturity Model (CTI-CMM)
- Using YARA for Malware Analysis
- Incident Response Information Sharing with IRIS
- Introduction to Disk Analysis Using Autopsy
Research and Development
YARA is also valuable for malware researchers analyzing new threats. By writing and refining malware detection rules, researchers can better understand the behavior and characteristics of different malware families.
Sharing this knowledge with the broader cybersecurity community improves collective defenses.
Creating Effective YARA Rules
Creating effective rules is both an art and a science. Here are some tips to ensure your rules are robust and accurate:
- Use Descriptive Names: Give your rules clear and descriptive names that indicate their purpose.
- Leverage Strings: Include strings that are unique to the malware you are targeting. These could be text strings, hexadecimal patterns, or regular expressions.
- Optimize Performance: Write rules that are efficient to avoid performance issues during large scans. This includes using the
conditionsection to combine multiple criteria effectively. - Test Thoroughly: Always test your rules against a variety of samples to ensure they correctly identify the intended files without false positives.
Conclusion
YARA is a critical tool in the fight against cyber threats. It helps you identify, classify, and mitigate malware.
Whether used for malware detection, threat hunting, incident response, or research, it’s flexibility and power make it an essential component of any cybersecurity strategy.

