In the ever-evolving landscape of cyber threats, organizations need a solid framework to assess and enhance their cyber threat intelligence (CTI) capabilities. Enter the Cyber Threat Intelligence Capability Maturity Model (CTI-CMM), a powerful tool designed to help organizations evaluate their current CTI practices, set ambitious goals for improvement, and benchmark their performance against industry standards.
This article dives into the details of the CTI-CMM, covering its purpose, key components, and strategies for implementation.
Let’s explore how this model can elevate your organization’s CTI efforts and improve your ability to tackle cyber threats head-on.
What is the CTI-CMM?
The CTI-CMM provides a structured framework to elevate an organization’s cyber threat intelligence maturity. As cyber threats become more sophisticated and frequent, having a robust CTI program is no longer optional; it’s a necessity. This model offers a clear pathway for organizations to build and refine their CTI capabilities, ensuring they align with industry best practices and strategic goals.
Developed by a diverse group of 27 industry professionals with extensive experience in cybersecurity, the CTI-CMM provides a standardized approach to enhancing CTI maturity.
Whether you’re looking to build a CTI program from scratch or improve existing practices, the CTI-CMM offers valuable insights and guidance.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
Why Do We Need Another Model?
You might wonder why we need another model when there are already so many frameworks available. The answer is simple: the cyber threat landscape is constantly changing, and traditional models often fail to address the unique challenges of CTI programs. The CTI-CMM takes a stakeholder-first approach, focusing on aligning intelligence capabilities with organizational goals and directly supporting business objectives.
Unlike other models, the CTI-CMM emphasizes collaboration with stakeholders, ensuring that intelligence efforts are relevant and actionable. This approach empowers organizations to make informed decisions and effectively manage cyber threats, reducing risks and safeguarding critical assets.
Key Concepts of the CTI-CMM
The CTI-CMM rests on several core concepts that form the foundation of effective cyber threat intelligence practices. Let’s break down these concepts and understand how they contribute to the overall success of a CTI program.
1. Stakeholder Engagement
Engaging stakeholders is the cornerstone of a successful CTI program. The CTI-CMM stresses the importance of understanding stakeholders’ needs, concerns, and requirements to tailor intelligence efforts accordingly. To achieve this, organizations must establish clear lines of communication and collaboration with key individuals and teams across the organization.
By focusing on stakeholder engagement, organizations can ensure their CTI programs deliver actionable intelligence that meets the needs of decision-makers and enhances overall security posture.
2. Strategic, Operational, and Tactical Intelligence
CTI operates at different levels within an organization, each serving a distinct purpose. Understanding these levels is essential for effectively managing cyber threats and aligning CTI efforts with organizational objectives.
- Strategic Intelligence: At the strategic level, CTI provides insights for long-term planning and policy development. It informs senior leadership, guides strategic initiatives, and aligns cybersecurity efforts with organizational goals.
- Operational Intelligence: Operational CTI supports specific campaigns and security operations, offering actionable intelligence for immediate threats. It provides relevant insights for infrastructure protection, incident response, and threat intelligence sharing.
- Tactical Intelligence: Tactical CTI focuses on real-time threat detection and response. It monitors and analyzes threat data, shares indicators of compromise (IoCs), and supports security operations to prevent and respond to attacks.
By aligning CTI efforts across these three levels, organizations can manage and respond to cyber threats more effectively, ensuring a comprehensive defense strategy.
3. Maturity Levels
The CTI-CMM uses a maturity level structure to assess an organization’s CTI capabilities. This structure helps organizations evaluate their current practices, set realistic goals for improvement, and track their progress over time. The model defines four maturity levels:
- CTI0 (Pre-Foundational): At this level, no practices are performed, indicating a lack of CTI capabilities.
- CTI1 (Foundational): Basic practices are performed, often in an ad hoc manner. The focus is on reactive intelligence that delivers short-term results.
- CTI2 (Advanced): Advanced practices are implemented at a higher level. The focus is on proactive and predictive intelligence that delivers short- and intermediate-term results.
- CTI3 (Leading): Leading practices are performed at the highest level. The focus is on prescriptive intelligence and recommendations that deliver long-term strategic results. Practices are measurable and aligned with business outcomes.
By assessing their maturity level, organizations can identify areas for improvement and develop a roadmap for achieving higher levels of CTI maturity.
How to Implement the CTI-CMM
Implementing the CTI-CMM involves a five-step process that integrates the model into existing CTI programs effectively. Let’s walk through each step and explore how organizations can use the CTI-CMM to elevate their CTI capabilities.
Step 0: Prepare
Before diving into the model, it’s crucial to understand that the CTI-CMM is a tool for evaluating and improving your CTI program.
Begin by identifying key stakeholders and understanding their definitions of success. Engage in discussions to set clear ambitions for your CTI program, considering the organization’s strategic projects and initiatives.
Key Questions to Consider:
- Who are the key stakeholders we need to engage with?
- What is their definition of success and value concerning the CTI program?
- What would be the ideal end state of our CTI program?
By answering these questions, organizations can lay the groundwork for a successful CTI program that aligns with stakeholder needs and organizational goals.
Step 1: Assess
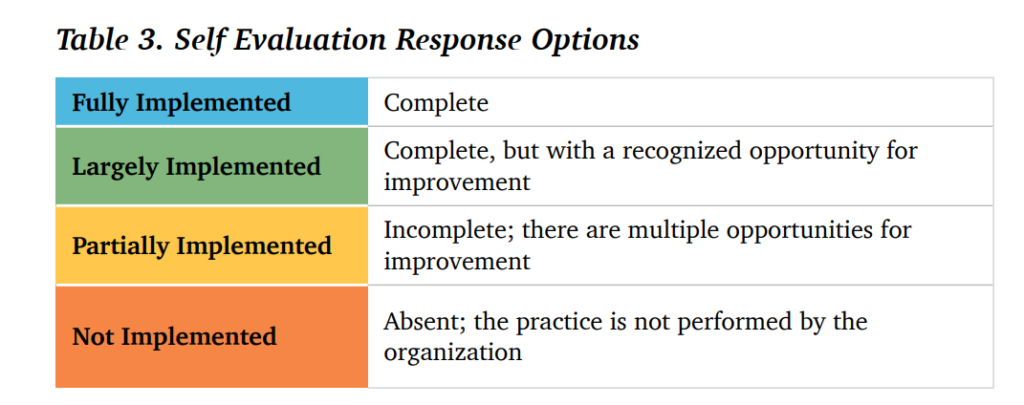
Conduct a self-evaluation of your CTI program’s current practices and maturity level. Use a four-point scale to assess the implementation of CTI practices across various domains.
Be critical and honest in your evaluation, identifying areas for improvement and setting realistic goals for advancement.
Evaluation Criteria:
- Fully Implemented: Practices are complete and effectively implemented.
- Largely Implemented: Practices are complete but have recognized opportunities for improvement.
- Partially Implemented: Practices are incomplete and have multiple areas for enhancement.
- Not Implemented: Practices are absent and not performed by the organization.
By assessing their current state, organizations can gain valuable insights into their CTI capabilities and identify areas for growth.
Step 2: Plan
Develop a strategic plan to improve CTI capabilities, focusing on areas that align with organizational priorities. Identify domains that require attention and set clear objectives for growth. Ensure that your plan is structured and aligned with existing organizational goals, considering time, resources, and cost.
Planning Considerations:
- Which domains are of high priority or strong for the organization?
- How can activities be correlated with strategic information from the organization?
- How will success be measured in both the short and long term?
By creating a comprehensive plan, organizations can establish a roadmap for achieving higher levels of CTI maturity and enhancing their overall security posture.
Step 3: Deploy
Execute your plan by deploying resources, such as vendor solutions, data feeds, and staffing, to enhance CTI capabilities. Prioritize actions based on the maturity growth goals set in your plan. Engage stakeholders and document decisions to ensure clarity and accountability throughout the execution phase.
Deployment Focus:
- Make conscious decisions in plan execution to ensure alignment with organizational goals.
- Document priority decisions and outcomes to create a clear record of progress.
- Be flexible and adjust the plan as needed for effective implementation.
By actively deploying resources and working collaboratively with stakeholders, organizations can achieve significant progress in their CTI capabilities.
Step 4: Measure
Regularly monitor and assess the CTI program’s maturity level, ensuring it aligns with organizational goals and stakeholder needs. Evaluate the effectiveness of CTI practices, identifying areas for adjustment and improvement. Use feedback and insights to refine strategies and demonstrate the value of the CTI program to the organization.
Key Measurement Questions:
- Is the CTI program providing measurable value?
- Are prioritized areas being addressed effectively?
- How can the demonstration of value be enhanced?
By continuously measuring their CTI capabilities, organizations can ensure their programs remain effective and aligned with strategic objectives.
Conclusion
The CTI-CMM offers a powerful framework for organizations seeking to build or enhance their cyber threat intelligence capabilities.
By aligning CTI practices with stakeholder needs and organizational goals, the CTI-CMM provides a structured approach to achieving maturity in threat intelligence. Implementing the model requires commitment, collaboration, and continuous evaluation, but the benefits of a mature CTI program are invaluable in today’s complex cyber landscape.
I recommend that organizations leverage the CTI-CMM to assess their current CTI practices, identify areas for improvement, and develop a strategic roadmap for growth.
The best way to stay ahead of evolving threats is to embrace continuous improvement and collaboration, ensuring your CTI program is robust, responsive, and aligned with the organization’s overarching objectives.
Download the paper
The paper has been published by the team behind cti-cmm.org. The paper is available on their website.
TIL did not write the paper, but we are very happy with it. Thats why we are also hosting it on our platform.


Leave a Reply
You must be logged in to post a comment.