IRIS stands for Incident Response Information Sharing. It’s a collaborative platform specifically designed for incident response analysts.
The platform facilitates the sharing of technical investigations efficiently and effectively.
Whether you’re stationed in a secure operations center or conducting field investigations, IRIS adapts to your needs.
How IRIS Enhances Incident Response
IRIS significantly streamlines the incident response process by enabling analysts to:
- Share detailed investigations quickly and securely.
- Access critical data in both connected and disconnected environments.
- Collaborate in real-time, enhancing decision-making and response times.
What Makes DFIR-IRIS Stand Out?
1. Incident Management Capability: DFIR-IRIS allows incident responders to effectively manage the entire lifecycle of an incident. This includes everything from initial detection to the final resolution, ensuring that no detail is overlooked and every threat is addressed promptly.
2. Robust Evidence Management: Handling digital evidence is a core function of DFIR-IRIS. Whether it’s system images, network traffic, or log files, the platform enables a thorough collection, preservation, and analysis, bolstering the integrity of your investigations.
3. Comprehensive Reporting and Compliance: IRIS shines in its ability to generate detailed documentation for compliance and reporting. This not only helps in meeting regulatory requirements but also in maintaining a clear record of incident response activities.
4. Integration and Collaboration Tools: Integration with other cybersecurity tools is seamless with DFIR-IRIS, enhancing its utility. The platform also promotes collaboration among different teams – be it incident response, forensic units, or even law enforcement.
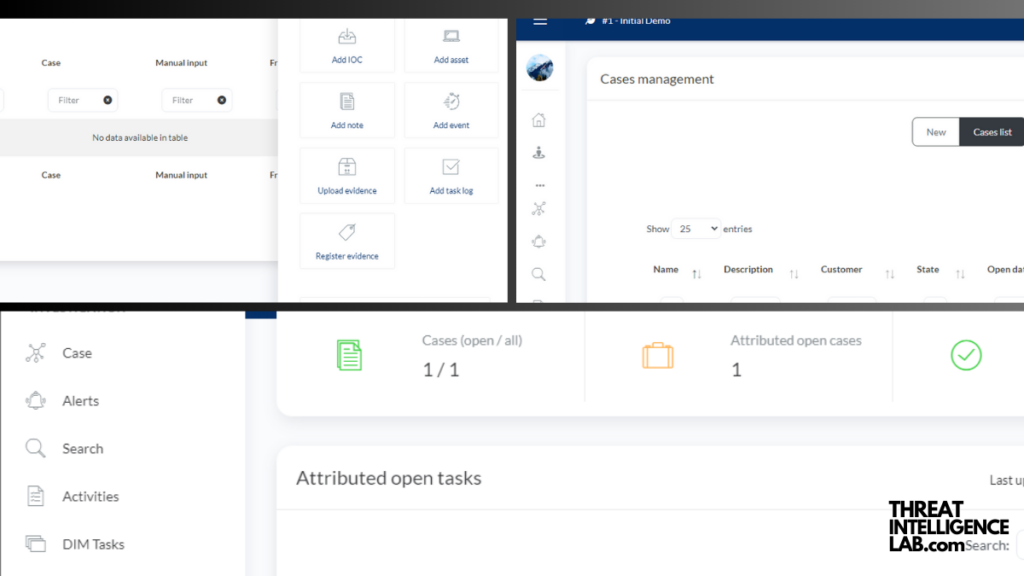
The Practicality of DFIR-IRIS Modules
One of the standout features of IRIS is its modular approach, similar to TheHIVE’s Cortex’s Analyzers and Responders.
IRIS modules come in two types:
- Pipeline Modules: These handle evidence upload and processing, such as parsing and injecting data into databases or visualizers.
- Processor Modules: These are triggered by predefined actions, providing real-time insights and notifications, for instance, when a new Indicator of Compromise (IOC) is detected.
Try out a demo (free)
If you’re considering DFIR-IRIS for your incident response needs, you can explore its capabilities firsthand through a demo version.
Simply visit https://v200.beta.dfir-iris.org/welcome to access the demo. This is an excellent opportunity to see how DFIR-IRIS operates in real-world scenarios before fully integrating it into your cybersecurity infrastructure.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- The Cyber Threat Intelligence Capability Maturity Model (CTI-CMM)
- Using YARA for Malware Analysis
- Incident Response Information Sharing with IRIS
- Introduction to Disk Analysis Using Autopsy
Installing DFIR-IRIS
Here’s how you can get IRIS up and running:
- Clone the iris-web repository.
- Check out the latest stable version.
- Configure the environment settings.
- Build and run the Docker containers.
The origins
IRIS emerged from the innovative minds at the French CSIRT of Airbus Cybersecurity. A small group of dedicated and friendly incident response analysts initially developed it.
Since its introduction in 2020, IRIS has played a crucial role in more than a hundred investigations, including responses to complex cyberattacks.
Now, the project operates autonomously, continually evolving and expanding its reach within the cybersecurity community.

