Your cart is currently empty!

How to Parse and Use VirusTotal feeds
The next one, is one we love – it is Virustotal.
This platform provides a malware gold mine and is filled with information that you can use to enhance your cybersecurity teams and services.

Let’s take a look at the services we are interested in. These are:
- Intelligence
- Hunting
- API
VirusTotal Intelligence: What can you expect
If you don’t have an account, you are allowed to upload any type of file to the platform.
Once it is uploaded, the file will be stored and analyzed within the Virustotal framework that is supported by 70+ antivirus companies.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- The Cyber Threat Intelligence Capability Maturity Model (CTI-CMM)
- Using YARA for Malware Analysis
- Incident Response Information Sharing with IRIS
- Introduction to Disk Analysis Using Autopsy
When the analysis of the file is finished, a report will be generated on the platform.
In this report, you can find all of the details and behavior of the uploaded file.
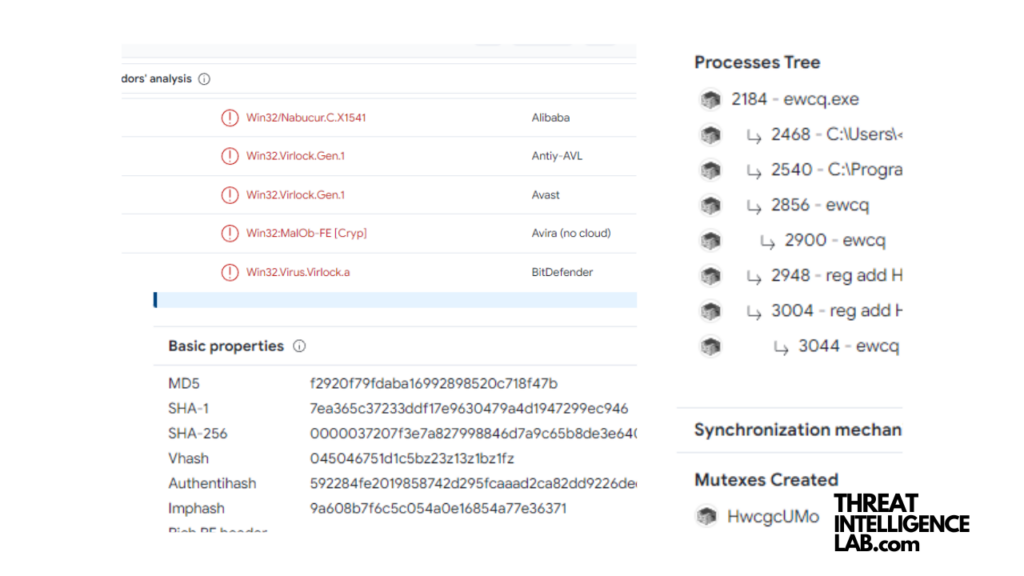
Now here comes the nice part, all of this information is stored within the Virustotal platform so it can be shared with cybersecurity professionals like yourself.
This brings us to the hunting capabilities of the platform.
Hunting with Livehunt
The hunting service allows anyone with a paid account to hunt down suspicious files with YARA rules. If YARA is new to you, do make sure to read the official YARA documentation here.
import "vt"
rule infected_pe {
condition:
vt.metadata.analysis_stats.malicious > 1 and vt.metadata.file_type == vt.FileType.PE_EXE
}Virustotal YARA rules enable you to dive into the big heap of data the platform has stored.
Collect files, malware reports and indicators of compromise (IOC) and feed them to your cybersecurity team. So they can learn from them and implement the needed changes that foster your cybersecurity posture.
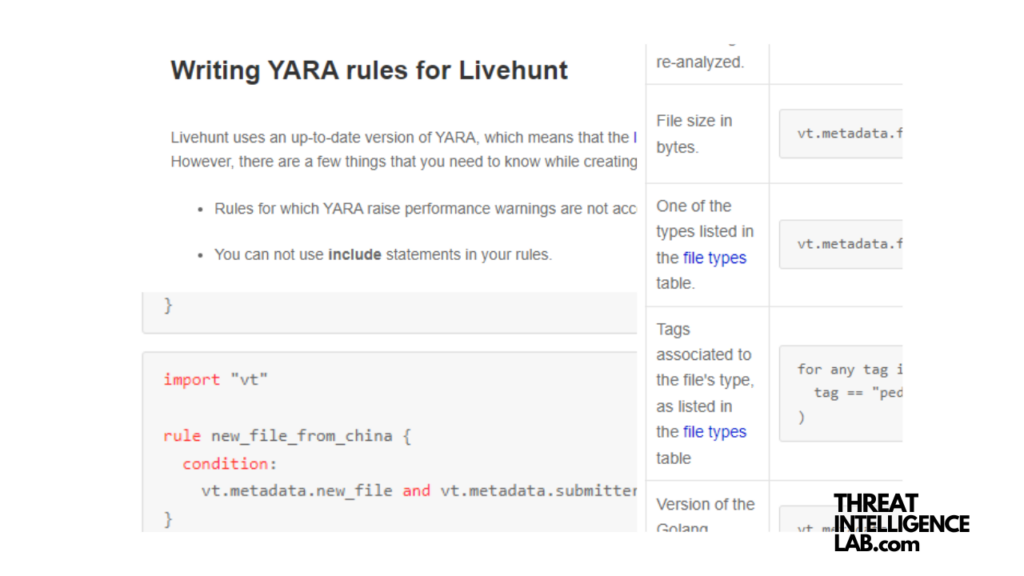
They provide this package in 3 different components:
Now that we know how to hunt and collect on the platform, it is time to take a look at the VirusTotal API.
Mastering the Virustotal API
The REST API by Virustotal has options that directly benefit cybersecurity teams.
Let’s take a look at their most used API endpoints:
- Upload a file for scanning
- Get a file report by hash
- Scan URL
- Get a URL analysis report
- Get a domain report
- Get an IP address report
Now with the strength of these API endpoints, you can quickly imagine the possibilities it provides to DFIR and SOC analysts.
They can parse IP, Domain, Hash or URL from a .CSV file and quickly get reports that shed light on possible TTPs.
Now let’s continue to the heavy threat intelligence feeds.
Threat Intelligence feeds
Aside of the mentioned feeds for analysts, Virustotal also provides these top tier intelligence feeds:
All of the feeds above provide fresh data in batches. These batches are provided per-minute or as a hourly feed.
Are these Feeds Paid?
Yes, all of the feeds provided by Virustotal require you to have a paid license key. The paid license packages lie in the range of $10K USD to a couple of $100K USD.
If you are interested in their services, take a look at their contact page for details.
Are there false positives?
Yes, there are false positives on Virustotal. Therefore it is an additional reason to grow experience and capabilities to filter data and translate it such so it eventually becomes actionable threat intelligence.
In other words, don’t expose RAW data to your end-customers or 3rd-parties outside your organization.
Do we Recommend it?
Yes. Get in touch with them, and see which packages works best for you. Ask them for use-cases and get experts to advice you on how to setup your framework before you start using the service.
As a good threat intelligence framework will help you to safe money.
