Your cart is currently empty!
threats
-

The Akira Ransomware Gang
The Akira Ransomware Gang has quickly become a key player in the cybercriminal world since its first sighting in March 2023. Today we will unpack who they are, how they operate, their significant impact, particularly on healthcare, and their recent strategic shift towards Linux systems. Who is the Akira Ransomware Gang? Emerging from the shadows…
-
Cl0p Ransomware Gang: The Unseen Cyber Menace
The Cl0p Ransomware Gang, emerging in 2019, stands out as a notorious cyber threat. This group, primarily Russian-speaking, has become synonymous with major cybersecurity breaches worldwide. Their modus operandi involves exploiting vulnerabilities, stealing sensitive data, and demanding hefty ransoms. Who is Cl0p? Cl0p operates under the ransomware-as-a-service (RaaS) model, leveraging their sophisticated malware for widespread…
-

Alphv: A New Era of Cyber Threats
Alphv, also known as BlackCat, has become a significant cyber threat. Emerging in November 2021, it quickly made a name for itself. It uses the Rust language for better stealth and performance across Windows, Linux, and VMWare systems. BlackCat Ransomware Exit Scam The BlackCat ransomware gang, known for its notorious cyberattacks, is reportedly pulling an…
-
Lockbit Breakdown: Cyber operations, evolution, and impacts
Lockbit is a notorious ransomware group known for its aggressive and sophisticated attacks. Originating in 2019, this group has rapidly become a significant threat, targeting corporations and government entities worldwide. They organize their operations meticulously, establishing themselves as formidable threat actors in cyberspace. Who is Lockbit? Lockbit is a cybercriminal group engaged in deploying ransomware…
-

The Risks of Expired SSL Certificates
SSL certificates are crucial for authenticating websites and ensuring secure internet traffic. They verify a website’s identity and encrypt the data exchanged between a user’s browser and the website. However, their effectiveness is contingent on their validity, which now, due to changes in policy by major internet entities like Apple, Google, and Mozilla, is capped…
-
Why Data Breach Report Feeds Are Important
Data Breach Reports stand out for their direct impact on enhancing cybersecurity teams. These reports, which detail incidents of data compromise within organizations, are not merely records of failure. Instead, they serve as vital notifications that can help prevent future breaches by informing us about the types of data targeted and the methods used by…
-

Top Malware Analysis Platforms & Tools (2024)
From an email attachment masquerading as benign to an application downloaded off the internet or even a snippet of malicious code on a legitimate website, the avenues through which malware can infiltrate our digital lives are vast and varied. In response, the cybersecurity community has stepped up, developing a variety of malware analysis tools designed…
-
Combatting Malware through Windows Scheduled Task Monitoring
Windows Scheduled Tasks are not merely background processes; they are keystones of system integrity and security. Today, I’ll dissect the critical importance of specific Windows event IDs—4698, 4699, 4701, and 4702. These IDs are far from being mundane logs. Instead, they represent a rich vein of information for incident responders keen on detecting and mitigating…
-

Detecting Abnormal Usage of Commonly Abused RMM Tools
In my years of experience in cybersecurity and threat intelligence, I’ve observed a worrying trend: the increasing abuse of Remote Monitoring and Management (RMM) tools by cybercriminals. These tools, designed to facilitate IT support and management tasks, have unfortunately become weapons in the arsenals of ransomware operators and hackers. Beyond the commonly known RMM tools…
-
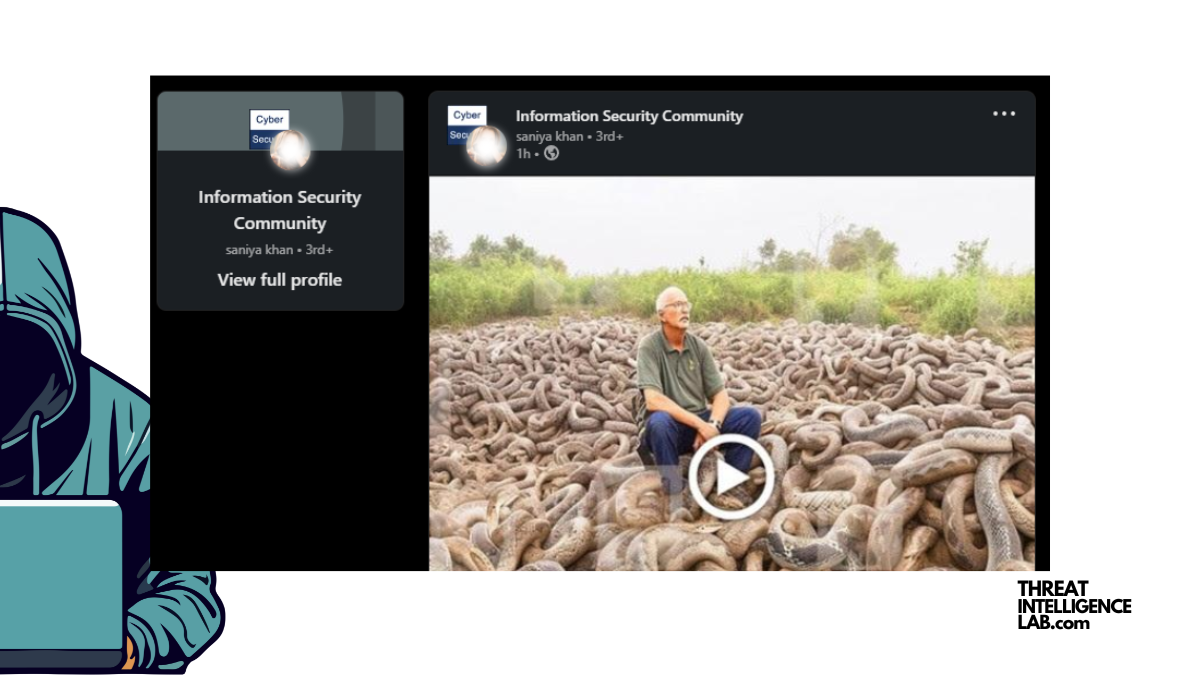
Be cautious of these Shocking LinkedIn posts
Don’t waste your time. Be aware. These types of post are here with only 1 reason. To make you click. What happens when you click such posts? Are they bad? Will you get ransomware? Will you lose your Crypto stash? — Post continues below. History These type of posts are not new to the cybersecurity…
