Your cart is currently empty!
threats
-

Mastering Threat Intelligence Dissemination
Let me walk you through the nuances of threat intelligence dissemination, highlighting its importance and offering strategies to enhance its impact. In my journey through the cybersecurity landscape, I’ve come to understand the critical role of threat intelligence. It’s not just about gathering data; it’s about effectively disseminating that intelligence to ensure it reaches the…
-

The Hidden Dangers of Using GitHub Tools Unchecked
In the realm of cybersecurity and threat intelligence, the allure of GitHub’s treasure trove of PoC tools can be irresistible. I’ve been there, sifting through repositories for that perfect piece of code that might just be the silver bullet for my latest challenge. However, the convenience of ready-to-use tools, especially Proof of Concept (PoC) tools…
-

Steps to Address CVE-2024-3094
CVE-2024-3094 has been identified as a severe vulnerability within XZ Utils. The widely used XZ format compression utilities is found in most Linux distributions. This loophole could enable malicious actors to bypass SSHD authentication, paving the way for unauthorized remote system access. What Happened? The heart of the issue lies in versions 5.6.0 and 5.6.1…
-

Ransomware as a Service (RaaS): An Overview
In my years immersed in the world of cybersecurity, I’ve come to understand that Ransomware as a Service (RaaS) is not just a problem; it’s a full-blown business model, a sinister innovation in the world of cybercrime. Essentially, RaaS is a subscription-based model that enables affiliates to use existing ransomware tools to execute cyberattacks. The…
-

How to limit the use of RDP and other remote desktop services
We know that the misuse of Remote Desktop Protocol (RDP) and similar services can open the door to a plethora of cyber threats. Let’s discuss how strictly limiting the use of RDP can significantly enhance your organization’s cybersecurity posture. 1. The Crucial Step: Disabling RDP The first and most fundamental step is to disable RDP…
-
BianLian Ransomware Group: A Rising Threat in Cybercrime
The BianLian ransomware group is a burgeoning cybercrime syndicate noted for its intricate data extortion operations. Originating around June 2022, this group has been relentlessly targeting crucial infrastructure sectors, predominantly in the United States and Australia, spanning professional services to property development. With at least twenty organizations fallen victim across various industries by September 2022,…
-

The Black Basta Cyber Threat
Black Basta emerges as a formidable force in the global ransomware landscape. Originating in early 2022, this group swiftly ascended in the cybercrime hierarchy, notorious for its Ransomware-as-a-Service (RaaS) model. They primarily targets organizations across the US, Japan, Canada, the UK, Australia, and New Zealand. They don’t scatter their attacks; they pinpoint their targets with…
-

The Power of Scenario-Based IR Training
As a cybersecurity and threat intelligence expert, you want to have a well-prepared incident response team. One effective way to enhance this preparedness is through scenario-based training. Let’s delve into this method and understand its significance, design, evaluation, and additional considerations for your team’s development. Scenario-Based Training for Incident Response Teams Scenario-based training is a…
-

Rhysida Ransomware Group
The advent of the Rhysida Ransomware Group, a malicious collective making headlines for its targeted cyberattacks, has rattled the cybersecurity landscape. Emerging initially in May 2023, Rhysida has swiftly ascended to prominence within the cybercriminal community, particularly menacing sectors like education, healthcare, manufacturing, IT, and government. Lets dive into the origins, operations, and preventive measures…
-
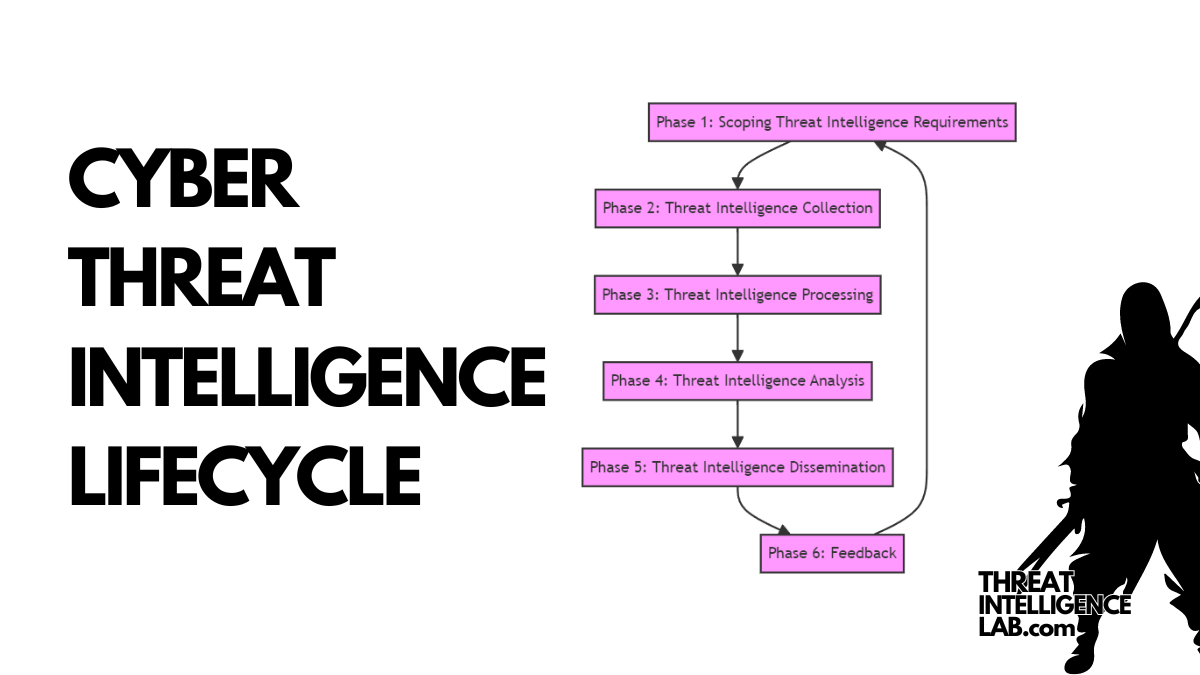
The Threat Intelligence Lifecycle: An Insider’s Guide
As someone entrenched in the world of cybersecurity and threat intelligence, I’ve seen firsthand the critical role that a structured Threat Intelligence Lifecycle plays in safeguarding organizations. From identifying what information is necessary, to collecting, processing, and analyzing data, each phase is pivotal. Let’s dissect this lifecycle to understand how it can be a game-changer…
