Your cart is currently empty!
threats
-

Key Cybersecurity Regulations and Standards Supporting the Financial Sector
In the financial sector, security and compliance are paramount. Here’s a comprehensive list of key cybersecurity regulations and standards that support the financial industry, ensuring protection against cyber threats and maintaining legal compliance. Payment Card Industry Data Security Standard (PCI DSS) Overview: PCI DSS is a set of security standards designed to ensure that companies…
-

How to Conduct an Effective Cyber Threat Intelligence Stand-Up Meeting
One way to ensure a team stays informed and coordinated is through a Cyber Threat Intelligence (CTI) stand-up meeting. These meetings, often brief and to the point, are essential for maintaining situational awareness and fostering collaboration among team members. In this article, I’ll walk you through what a CTI stand-up meeting should look like, how…
-

The Critical Importance of Taking Down Fake Social Media Accounts
In today’s digital age, social media platforms are not just spaces for networking and entertainment but are crucial for the dissemination of information. Consequently, the presence of fake social media accounts can distort these spaces, spreading misinformation and causing untold harm. Understanding why the takedown of these false accounts is essential offers a clearer perspective…
-

How FastFlux Networks Complicate Cyber Takedowns
In today’s evolving cyber landscape, FastFlux networks represent a significant challenge for cybersecurity authorities. Essentially, FastFlux is a DNS technique used by cybercriminals to hide phishing and malware delivery sites behind an ever-changing network of compromised hosts acting as proxies. It complicates the process of tracking and dismantling malicious websites and botnets, ensuring these malicious…
-

Understanding Phishing Takedowns: A Guide to Safeguarding Digital Assets
Phishing takedowns play a critical role in the battle against cyber threats. Essentially, these operations are vital in disrupting the activity of cybercriminals who deceive individuals into providing sensitive data. This article delves deep into the mechanisms of phishing takedowns, illustrating their importance and effectiveness. The Concept of Phishing Takedowns Phishing takedowns involve identifying and…
-

NetFlow-Based Monitoring
We all recognize the critical role that network traffic monitoring plays in safeguarding organizational security. This technology not only streamlines the process of recording and analyzing network flows but also empowers security teams to detect anomalies, enhance network performance, and thwart potential threats efficiently. Understanding NetFlow NetFlow stands out as a network protocol designed to…
-
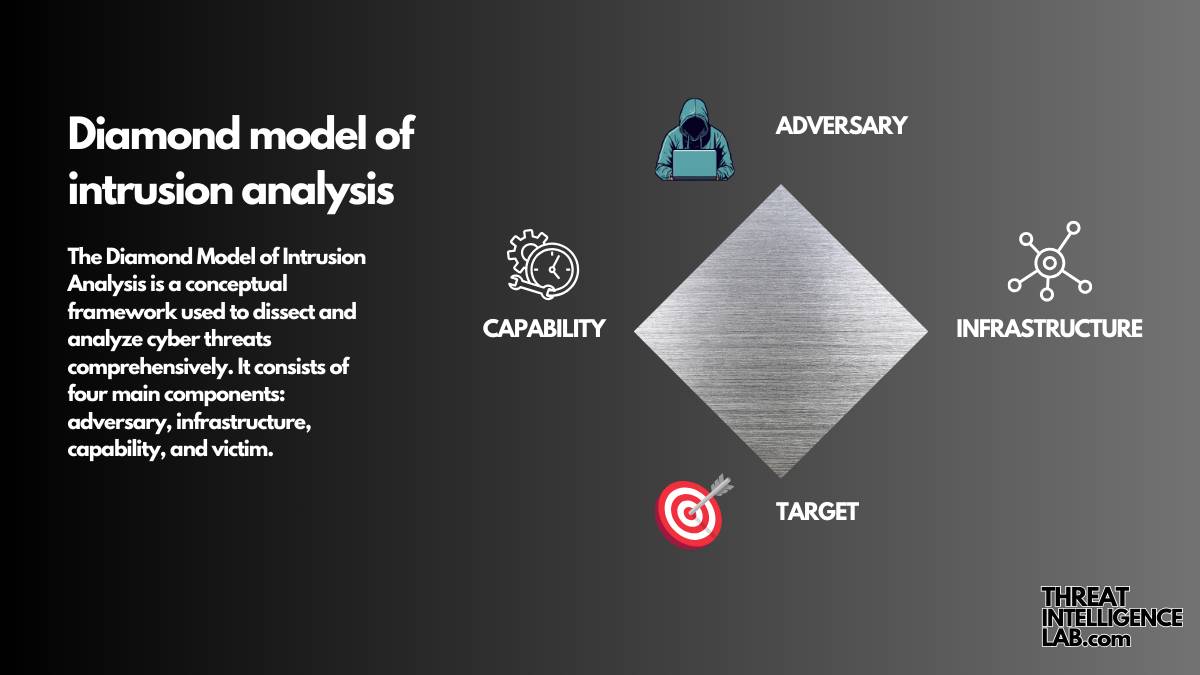
Understanding the Diamond Model of Intrusion Analysis
The Diamond Model of Intrusion Analysis framework stands out for its clarity and effectiveness. Today, I’m going to share why this model is pivotal in understanding cyber attacks and how it can significantly enhance your security posture. What is the Diamond Model of Intrusion Analysis? The Diamond Model was developed to provide a more structured…
-
Responding to a Potentially Compromised Firewall
When you suspect that your firewall has been compromised, it’s crucial to act swiftly and effectively to secure your network. This guide outlines the steps network engineers should take to respond to such a security incident. Why Didn’t My EDR Protect My Firewall? Some people think EDR includes firewalls. But firewalls don’t have EDR software,…
-
The difference between cybersecurity and cyber intelligence
In my experience working in threat intelligence, I’ve come to understand the critical distinctions between cybersecurity and cyber intelligence. These two fields, though often intertwined, address different aspects of information security. Let’s break down the differences. The Realm of Cybersecurity Cybersecurity focuses on the protection of IT infrastructure, networks, and data from cyber threats and…
-
The MongoDB Ransomware Experiment
Imagine setting up a honeypot, a decoy system, to mimic a vulnerable MongoDB database, just to see what might happen. That’s exactly what we did. Within an hour, our honeypot was not only discovered but also compromised, with all its data encrypted and replaced by a ransom note. Our MongoDB Honeypot Experiment Our honeypot was…
