Black Basta emerges as a formidable force in the global ransomware landscape. Originating in early 2022, this group swiftly ascended in the cybercrime hierarchy, notorious for its Ransomware-as-a-Service (RaaS) model.
They primarily targets organizations across the US, Japan, Canada, the UK, Australia, and New Zealand. They don’t scatter their attacks; they pinpoint their targets with precision1.
Their strategy? A menacing blend of data encryption and double extortion, threatening to release sensitive information unless a ransom is paid2.

Who Is Black Basta?
Black Basta, or BlackBasta, isn’t just any ransomware operator. They are a criminal enterprise, born possibly from the remnants of the Conti threat group.
The similarities in malware development, negotiation tactics, and leak site operations hint at a lineage tied to seasoned cybercriminals3.
Additionally, there’s evidence suggesting a connection4 between Black Basta and the notorious FIN7 (also known as Carbanak5) group, particularly in their use of unique evasion modules and overlapping IP addresses for command and control operations.
- BianLian Ransomware Group: A Rising Threat in Cybercrime
- The Black Basta Cyber Threat
- Rhysida Ransomware Group
- The Akira Ransomware Gang
- Cl0p Ransomware Gang: The Unseen Cyber Menace
How Does Black Basta Operate?
Their modus operandi begins with precision: targeted spear-phishing campaigns or the purchase of corporate network access.
Once inside, they don’t pause; they escalate their privileges6, steal data, and lay the groundwork for the ransomware deployment.
Tools like QakBot, MimiKatz, and PowerShell become their weapons of choice for stealing credentials and infiltrating further into the network.
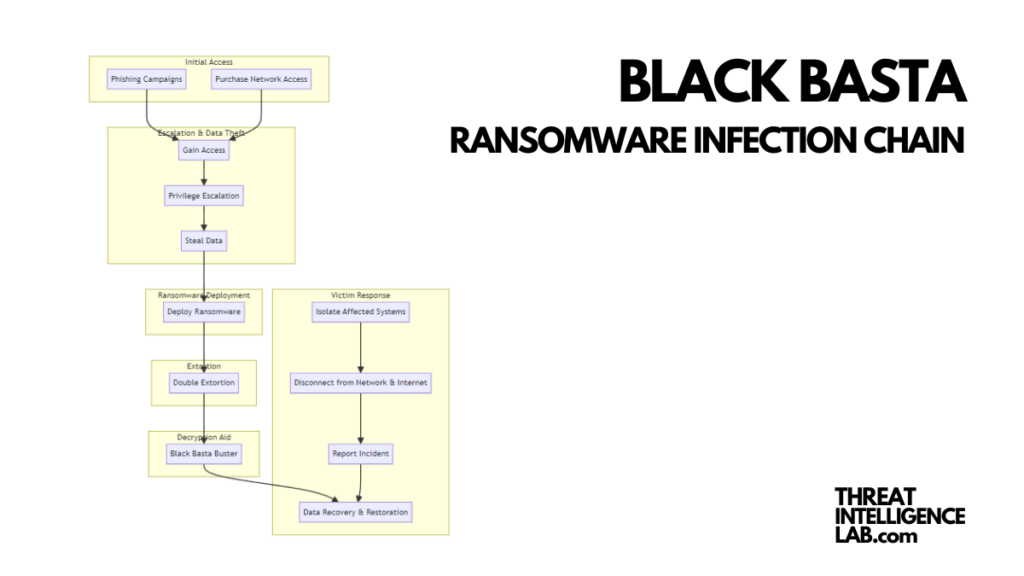
They exploit vulnerabilities like ZeroLogon7, NoPac, and PrintNightmare to extend their control. When the time is right, they unleash their ransomware, paralyzing systems and beginning their extortion.
Black Basta Buster: Decryption Tool
Black Basta Buster is a tool developed to counteract the encryption used by the Black Basta ransomware group.
This suite capitalizes on a specific weakness found in the ransomware’s encryption algorithm as of April 20238.
It offers potential data recovery options based on the file’s size and the presence of 64 known plaintext bytes.
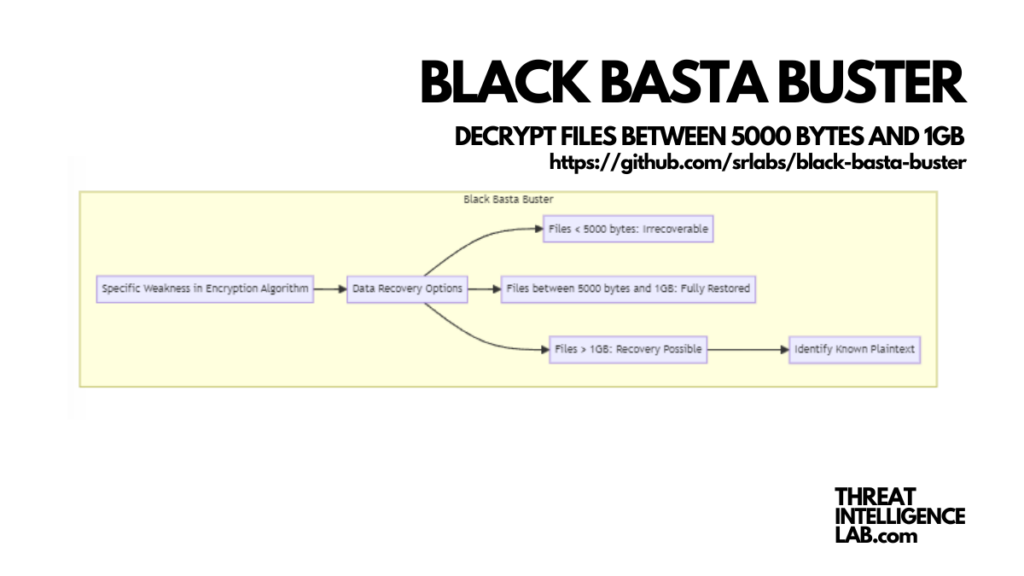
Files under 5000 bytes are irrecoverable, but those between 5000 bytes and 1GB could be fully restored.
For files larger than 1GB, recovery is possible minus the first 5000 bytes. Success depends on correctly identifying the known plaintext in the encrypted file, particularly for virtual machine disk images.
A Timeline of Disruption
The impact of Black Basta is widespread and devastating. From disabling DNS services to hinder recovery processes to targeting Linux-based VMware ESXi virtual machines, their tactics are diverse and damaging.
They’ve made headlines for causing significant disruptions, like the Toronto Public Library outages and the costly breach at Capita.
The group’s aggressive approach and sophisticated techniques place them among the threats in the cybersecurity world.
FAQs
- https://therecord.media/chile-black-basta-ransomware-attack-customs-department ↩︎
- https://www.hhs.gov/sites/default/files/black-basta-threat-profile.pdf ↩︎
- https://quadrantsec.com/sites/default/files/2023-01/Black-Basta_Technical-Analysis_2023.pdf ↩︎
- https://www.computerweekly.com/news/366547512/Black-Basta-Hive-and-Royal-ransomware-gangs-may-share-real-world-connection ↩︎
- https://attack.mitre.org/groups/G0008/ ↩︎
- https://securityscorecard.com/wp-content/uploads/2024/01/Report-A-Deep-Dive-Into-Black-Basta-Ransomware.pdf ↩︎
- https://www.secura.com/uploads/whitepapers/Zerologon.pdf ↩︎
- https://www.quorumcyber.com/wp-content/uploads/2023/04/QC-BlackBasta-Ransomware-Report-TI.pdf ↩︎
- https://github.com/srlabs/black-basta-buster ↩︎

