Your cart is currently empty!

The Akira Ransomware Gang
The Akira Ransomware Gang has quickly become a key player in the cybercriminal world since its first sighting in March 2023.
Today we will unpack who they are, how they operate, their significant impact, particularly on healthcare, and their recent strategic shift towards Linux systems.
Who is the Akira Ransomware Gang?
Emerging from the shadows of the defunct Conti group, the Akira Ransomware Gang has carved a niche in the cyber underworld1.
They have targeted a wide range of organizations, primarily in the US and Canada2, using a notorious double-extortion tactic and leveraging a ransomware-as-a-service (RaaS) model.
These cybercriminals have become known for their relentless pursuit of financial gain through cyber extortion.
- BianLian Ransomware Group: A Rising Threat in Cybercrime
- The Black Basta Cyber Threat
- Rhysida Ransomware Group
- The Akira Ransomware Gang
- Cl0p Ransomware Gang: The Unseen Cyber Menace
How Does the Akira Ransomware Gang Operate?
The Akira gang exploits system vulnerabilities3, particularly unpatched VPNs4 and VMware ESXi vulnerabilities. Initially, they gain access through compromised credentials, a method accentuated by the absence of multi-factor authentication.
Subsequently, they engage in lateral movement within networks using tools like RDP and SMB.
Their approach is strategic and methodical, focusing on extracting the maximum financial impact5.
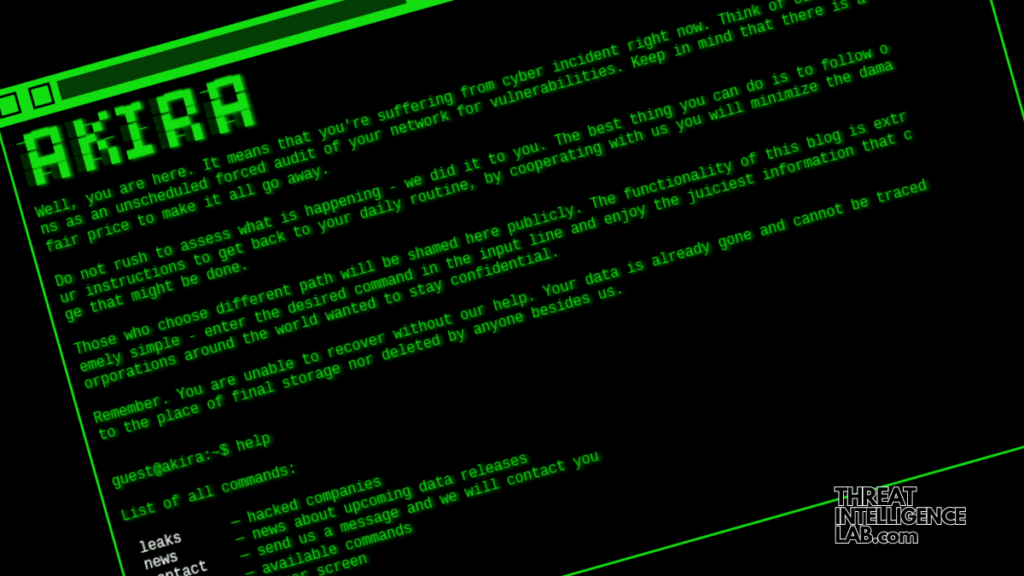
Akira Ransomware Gang’s Cyberattacks
Interestingly, their attacks are meticulously planned. The gang employs advanced techniques for privilege escalation and maintaining network access, showcasing their deep understanding of network architectures.
Notably, they have removed security solutions to evade detection6, displaying their technical prowess and persistence.
Impact on the Healthcare Sector
Alarmingly, Akira has targeted the healthcare sector aggressively. HC37 has highlighted their focus on healthcare and critical infrastructure, issuing multiple warnings.
With over 81 cyberattacks reported, including on healthcare institutions, the threat they pose is substantial8.
Healthcare organizations are urged to implement stringent security measures9, like network segmentation and multi-factor authentication, to fend off such threats.
The Evolution: Targeting Linux Systems
Akira has expanded its horizons by targeting Linux systems10. This move signifies a strategic shift and reflects a broader trend among cybercriminals targeting open-source platforms11.
FAQs
- https://www.hhs.gov/sites/default/files/akira-ransomware-sector-alert-tlpclear.pdf ↩︎
- https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-akira ↩︎
- https://www.logpoint.com/wp-content/uploads/2023/09/emerging-threats-akira.pdf ↩︎
- https://www.criticalstart.com/wp-content/uploads/2024/02/Akira-Ransomware-Exploits-Cisco-ASAFTD-Vulnerability.pdf ↩︎
- https://www.securityweek.com/dozens-of-organizations-targeted-by-akira-ransomware/ ↩︎
- https://news.sophos.com/en-us/2023/12/21/akira-again-the-ransomware-that-keeps-on-taking/ ↩︎
- https://healthitsecurity.com/news/akira-ransomware-aggressively-targets-healthcare-hc3-warns ↩︎
- https://www.nomoreransom.org/uploads/User%20Manual%20-%20Akira_Decryptor.pdf ↩︎
- https://www.truesec.com/hub/blog/akira-ransomware-victim ↩︎
- https://techmonitor.ai/technology/cybersecurity/akira-ransomware-adds-malware-targeting-linux-to-its-arsenal ↩︎
- https://e.cyberint.com/hubfs/Ransomware%20Recap%202023.pdf ↩︎
