Your cart is currently empty!

Rhysida Ransomware Group
The advent of the Rhysida Ransomware Group, a malicious collective making headlines for its targeted cyberattacks, has rattled the cybersecurity landscape.
Emerging initially in May 2023, Rhysida has swiftly ascended to prominence within the cybercriminal community, particularly menacing sectors like education, healthcare, manufacturing, IT, and government.
Lets dive into the origins, operations, and preventive measures concerning this looming threat.

Who is the Rhysida Ransomware Group?
The Rhysida Ransomware Group operates under a ransomware-as-a-service (RaaS) framework, notoriously targeting various sectors to instill chaos and extort money.
Despite their quite recent emergence, their cyberattacks have already caused significant disruptions.
The group’s modus operandi revolves around exploiting vulnerabilities, conducting phishing campaigns, and leveraging external-facing remote services to infiltrate networks.
- BianLian Ransomware Group: A Rising Threat in Cybercrime
- The Black Basta Cyber Threat
- Rhysida Ransomware Group
- The Akira Ransomware Gang
- Cl0p Ransomware Gang: The Unseen Cyber Menace
How Does Rhysida Operate?
Upon breaching a system, Rhysida deploys a range of tools and scripts1, to extract credentials, and clearing event logs to conceal their activities.
The ransomware itself, marked by its intricate encryption methodologies, utilizes a combination of a 4096-bit RSA key and the ChaCha20 algorithm to lock down victims’ data2.
Post-encryption, they demand ransoms paid exclusively in Bitcoin.
Rhysida’s Distinct Tactics
Interestingly, while Rhysida exhibits a level of sophistication, it also displays certain operational inadequacies when compared to other ransomware factions.
Mitigating Rhysida Attacks
To combat Rhysida, cybersecurity experts, including those from CISA, FBI, and MS-ISAC, recommend a series of defensive measures3.
Key strategies encompass implementing phishing-resistant multifactor authentication, disabling unnecessary command-line and scripting activities, and enhancing system logging.
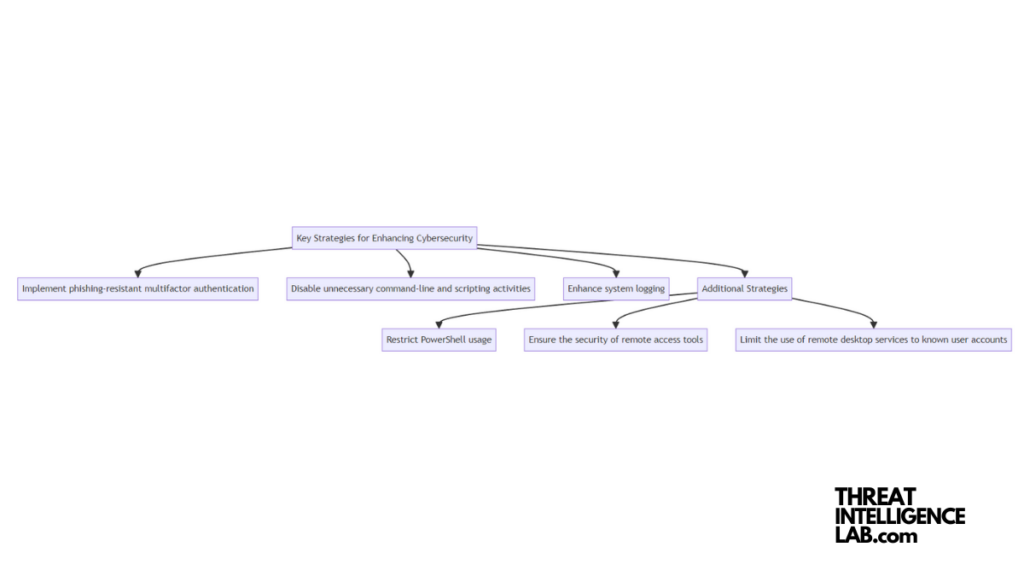
Additionally, organizations should restrict PowerShell usage4, ensure the security of remote access tools, and limit the use of remote desktop services to known user accounts.
Adopting these practices can significantly reduce the risk of infiltration and mitigate potential damage.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
FAQs
- https://www.mycert.org.my/portal/advisory?id=MA-989.112023 ↩︎
- https://www.hhs.gov/sites/default/files/rhysida-ransomware-sector-alert-tlpclear.pdf ↩︎
- https://www.cisa.gov/news-events/alerts/2023/11/15/cisa-fbi-and-ms-isac-release-advisory-rhysida-ransomware ↩︎
- https://www.aha.org/news/headline/2023-11-15-fbi-cisa-ms-isac-warn-rhysida-ransomware-threat-hospitals ↩︎
