The BianLian ransomware group is a burgeoning cybercrime syndicate noted for its intricate data extortion operations.
Originating around June 20221, this group has been relentlessly targeting crucial infrastructure sectors, predominantly in the United States2 and Australia, spanning professional services to property development.
With at least twenty organizations fallen victim across various industries by September 2022, BianLian’s menacing footprint is expanding.
Who is BianLian?
BianLian, initially identified as an Android banking trojan in 2019, has transformed3 into a formidable ransomware entity.
Their tactics have significantly impacted sectors like insurance, healthcare, legal, and engineering.
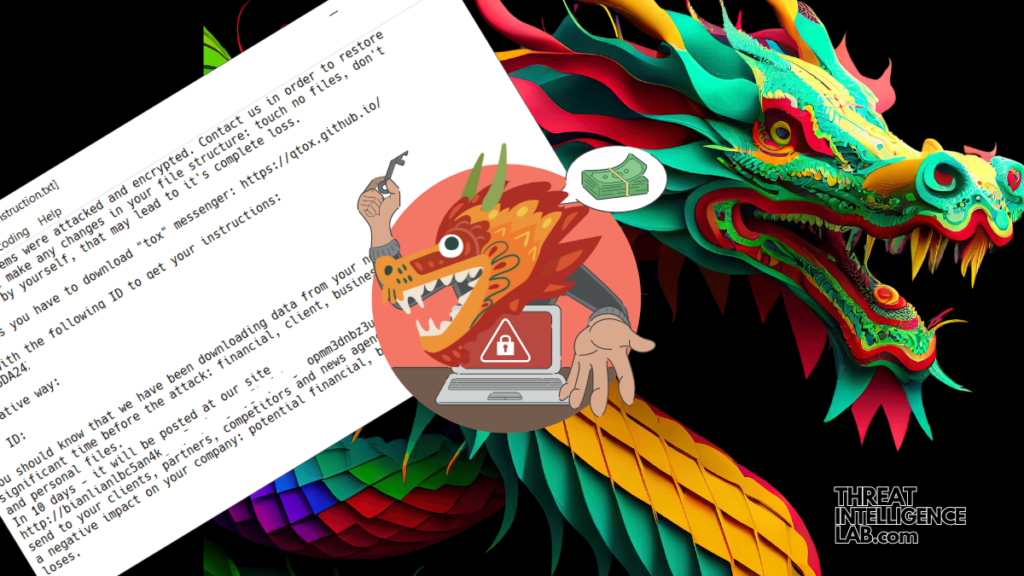
Their mode of operation? They infiltrate systems, encrypt data rapidly using malware written in the Go programming language technology. They then demand ransom while threatening to leak stolen information on their dark web portal.
- BianLian Ransomware Group: A Rising Threat in Cybercrime
- The Black Basta Cyber Threat
- Rhysida Ransomware Group
- The Akira Ransomware Gang
- Cl0p Ransomware Gang: The Unseen Cyber Menace
How Does BianLian Operate?
BianLian distinguishes itself through exceptionally swift encryption processes, a feat attributed to the Go programming language’s efficiency.
The group doesn’t just stop at encryption; they engage in data theft, uploading proofs of their heists on their Tor-based leak site.
This dual-threat approach intensifies their extortion efforts, placing immense pressure on their victims to comply.
Recently, BianLian caught attention for exploiting vulnerabilities in the JetBrains TeamCity software, showcasing their adaptive strategies in pursuing ransomware campaigns.
Such tactics allow them to implant their Go-based backdoor systems through compromised servers, signifying a persistent, evolving threat landscape.
More on this ransomware gang (external resources)
- Decrypted: BianLian Ransomware
- BianLian Ransomware Gang Gives It a Go!
- BianLian: New Ransomware variant on the rise
- BianLian – from rags to riches, the malware dropper that had a dream
BianLian’s Cyberattacks
A standout incident in BianLian’s campaign involved a significant breach at Air Canada, where they extracted 210 GB of sensitive data.
This attack underscores the group’s capability to inflict severe damage by obtaining critical operational data.
Moreover, the recent attack on Lindsay Municipal Hospital highlights their ongoing agenda to target US institutions, further emphasizing the pervasive risk they pose to public and private sectors alike.
FAQs
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-136a ↩︎
- https://www.cisa.gov/news-events/alerts/2023/05/16/cisa-and-partners-release-bianlian-ransomware-cybersecurity-advisory ↩︎
- https://www.bleepingcomputer.com/news/security/fbi-confirms-bianlian-ransomware-switch-to-extortion-only-attacks/ ↩︎