Your cart is currently empty!

Becoming a Cyber Threat Intelligence Analyst (2024)
Cyber Threat Intelligence Analysts earn an impressive salary of $140,000 USD annually. Explore the role, duties, and promising career outlook.
Their role is pivotal in the cybersecurity landscape, acting as the frontline defenders against cyber threats and attacks.
Today, I’ll share insights into what exactly a threat intelligence analyst does, why their role is crucial, and how they contribute to safeguarding organizations’ digital assets.
The CTI Analyst Role
A threat intelligence analyst is someone who collects, analyzes, and interprets data on potential threats to an organization’s cybersecurity1.
Their primary goal is to understand the threats that an organization faces and to develop strategies to prevent or mitigate these threats.
This involves staying ahead of the curve, constantly researching and analyzing trends in cyber threats, and understanding the tactics, techniques, and procedures (TTPs) of cyber adversaries.
Key Responsibilities
Data Collection: The Starting Line
The journey of a threat intelligence analyst begins with the comprehensive collection of data.
This task extends beyond internal network surveillance, encompassing the vast expanses of the internet, including the dark web, social media, and other open web platforms.
The objective here is clear: amass a dataset that provides a complete overview of potential threats. This step is pivotal, as it lays the groundwork for all subsequent analysis and decision-making processes.
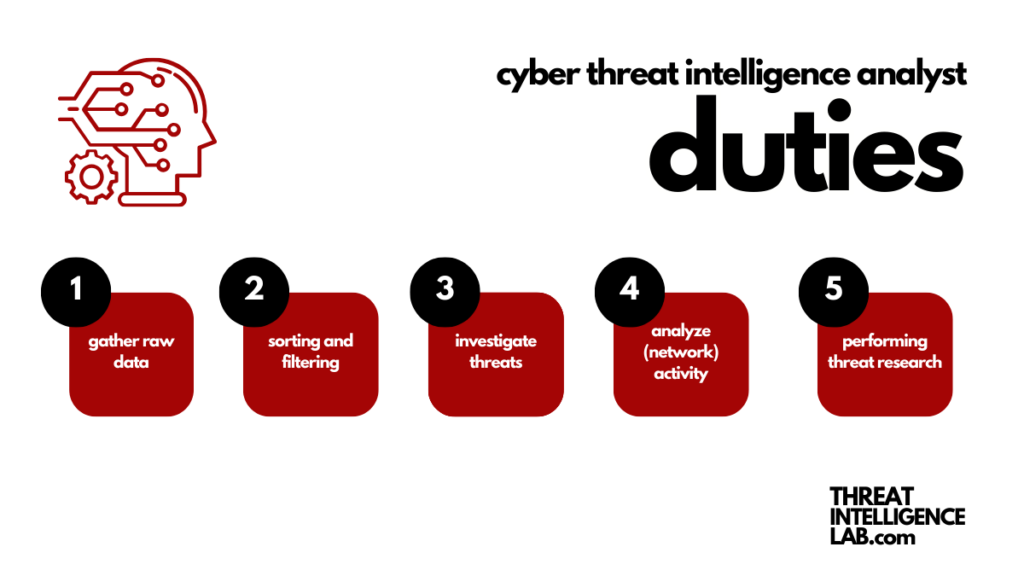
Data Analysis: The Heart of the Operation
Once the data is collected, the analyst’s focus shifts to organizing, sorting, and analyzing this information. In today’s digital age, this involves more than just manual review.
Tools that you should know
- Splunk: A platform for searching, monitoring, and analyzing machine-generated data, including logs and events.
- Elasticsearch: A distributed, RESTful search and analytics engine used for full-text search, structured search, and analytics.
- Wireshark: A network protocol analyzer that allows you to capture and interactively browse the traffic running on a computer network.
- Jupyter Notebook: An open-source web application that allows you to create and share documents containing live code, equations, visualizations, and narrative text.
Analysts now rely on sophisticated data analytics tools and machine learning algorithms to sift through the data efficiently.
This process helps identify potential threats and vulnerabilities within the network.
It’s a crucial step that enables analysts to distinguish between genuine threats and benign data, ensuring that resources are allocated effectively to counteract real cyber risks.
Investigating Cyber Threats & Attacks
Following the initial data analysis, analysts delve deeper to investigate the identified threats.
This involves pinpointing the origins of these threats, understanding how they infiltrate systems, and evaluating their potential impact.
The goal is to trace the network’s flow, identify vulnerable points, and develop a robust defensive strategy that can prevent future breaches.
- Why Data Breach Report Feeds Are Important
- The Top 10 Essential Log Sources for IT Monitoring
- Dark Web Cybercrime Forums You Should Monitor
- How to Parse and Use VirusTotal feeds
- Getting The Most Out Of URLscan.io
Anticipating Future Threats
A key responsibility of today’s threat intelligence analysts is to conduct predictive analyses of network activity.
By examining the tactics, techniques, and procedures (TTPs) of threat actors, analysts can forecast future cybercrime trends.
This predictive insight is invaluable, as it informs the organization’s incident response and digital forensic efforts, enabling a more prepared and resilient cybersecurity posture.
Cyber Threat Hunting Tasks
Threat intelligence analysts also take on the proactive task of threat hunting.
This involves forming hypotheses about potential attacks and understanding the attackers’ objectives.
By leveraging advanced analytics, analysts can uncover new and emerging threats, ensuring that the organization stays ahead of potential attacks.
Prioritizing Defense
Understanding the broader context, including the impact of political and current affairs on security risks, is crucial for threat intelligence analysts.
This knowledge allows them to prioritize cyber defenses effectively, focusing on the most pressing threats and developing targeted action plans.
Bridging the Gap
A vital part of the role involves generating intelligence reports and communicating findings to various stakeholders, including the security operations center (SOC), executives, and management.
This ensures that everyone is informed and aligned on the cybersecurity strategy.
Staying Ahead with Continuous Research
Regular research on threats is imperative for a threat intelligence analyst. This ongoing effort enriches the organization’s understanding of the cyber threat landscape, enabling a more effective defense against attacks.
Skills You Need
To thrive as a cyber threat intelligence analyst, your arsenal must be well-equipped with both hard and soft skills. Here’s what you need:
- Technical Mastery: A profound understanding of cybersecurity trends, threats, and concepts. You must navigate the digital terrain with expertise.
- Strategic Communication: Your insights are invaluable; conveying them effectively is crucial. Whether to technical teams or non-tech stakeholders, clarity is key.
- Creative Problem-Solving: The cyber realm is unpredictable. Your ability to devise innovative solutions will set you apart.
- Adversary Mindset: Understanding how cyber adversaries think enables you to predict and mitigate threats effectively.
- Eagerness to Learn: The cyber world evolves daily. A relentless desire to learn keeps you ahead of the curve.

Honing Your Weapons: Certification
Certifications are your badges of honor, showcasing your skills and dedication. Consider obtaining credentials such as CISSP, Security+, ISSEP, or GIAC. These certifications will sharpen your cybersecurity capabilities.
The Reward: Salary
Your dedication and skills are highly valued2, with salaries reflecting the importance of your role. Ranging from $61,000 to over $200,0003 annually, the compensation mirrors the impact and expertise you bring to the table.

Companies Hiring
The demand for Intelligence Analysts spans across industries. Giants like ABN AMRO Bank, Citi, and Tesla, alongside innovators like Deloitte and Microsoft, are on the lookout for talents like you.
This widespread demand underscores the critical role you’ll play in the digital age.
Strategic Importance
The strategic importance of a Cyber Threat Intelligence Analyst cannot be overstated. They enable organizations to adopt a proactive rather than reactive approach to cybersecurity.
By understanding the potential threats, organizations can implement targeted defenses before an attack occurs. This significantly reduces the risk of a successful cyber attack and its potential impact on the organization.
Additionally, threat intelligence analysts play a vital role in incident response.
In the event of a security breach, they provide critical insights that help to quickly identify and mitigate the attack. This reduces the time attackers are in the system and limits the damage they can cause.
How they help teams
Best Practices for Success
I recommend that organizations invest in training and resources for their threat intelligence analysts. Keeping up-to-date with the latest cybersecurity trends and technologies is essential for effective threat analysis.
Additionally, leveraging threat intelligence platforms can enhance an analyst’s ability to collect and analyze data, making their job more efficient4.
The best way to get results from threat intelligence is by integrating it into all aspects of cybersecurity.

This means not only using it to inform defensive measures but also incorporating it into strategic planning and decision-making processes5. By doing so, organizations can ensure they are well-prepared to face the ever-evolving landscape of cyber threats.
Conclusion
The role of a threat intelligence analyst is critical in today’s digital world. Their work in identifying, analyzing, and mitigating cyber threats is essential for protecting an organization’s information assets.
With the right tools and strategies, they can provide the intelligence needed to stay one step ahead of cyber adversaries6.
- How to Conduct an Effective Cyber Threat Intelligence Stand-Up Meeting
- Avoiding Pitfalls: Top 10 Rookie Cybersecurity Career Mistakes
- Land Your First Junior Security Engineer Position
- How to Land Your First Job as a Junior Malware Analyst
- Landing a Junior Penetration Tester Position
As we continue to navigate through the complexities of the cyber world, the role of threat intelligence analysts will only grow in importance, making their contribution indispensable to the cybersecurity field.
- https://www.researchgate.net/publication/377264827_Cyber_Threat_Intelligence_Analyst_Analyzing_and_Neutralizing_Digital_Threats/link/659d7f410bb2c7472b3f062e/download?_tp=eyJjb250ZXh0Ijp7ImZpcnN0UGFnZSI6InB1YmxpY2F0aW9uIiwicGFnZSI6InB1YmxpY2F0aW9uIn19 ↩︎
- https://www.glassdoor.com/Salaries/threat-intelligence-analyst-salary-SRCH_KO0,27.htm ↩︎
- https://www.theladders.com/salary/cyber-threat-intelligence-analyst-salary ↩︎
- https://go.iproov.com/rs/891-TPZ-847/images/iProov_Threat_Intelligence_Report_2024.pdf ↩︎
- https://www.crest-approved.org/wp-content/uploads/2022/04/CREST-Cyber-Threat-Intelligence.pdf ↩︎
- https://hodigital.blog.gov.uk/wp-content/uploads/sites/161/2020/03/Cyber-Threat-Intelligence-A-Guide-For-Decision-Makers-and-Analysts-v2.0.pdf ↩︎
