Your cart is currently empty!
Cyber Attack Cycle: Weaponization and Delivery
Today, let’s delve into the second step: Weaponization and Delivery. Here, attackers prepare and send their malicious payload to the target.
Understanding this phase is crucial because it’s where the groundwork is laid for the impending attack. By dissecting this process, we can better prepare and defend against these tactics.
What is Weaponization in Cyber Attacks?
Weaponization involves crafting the attack tools that will eventually infiltrate the target’s system. Typically, this includes coupling malware with non-malicious files to dupe unsuspecting users into downloading a Trojan horse, or preparing scripts for exploitation.
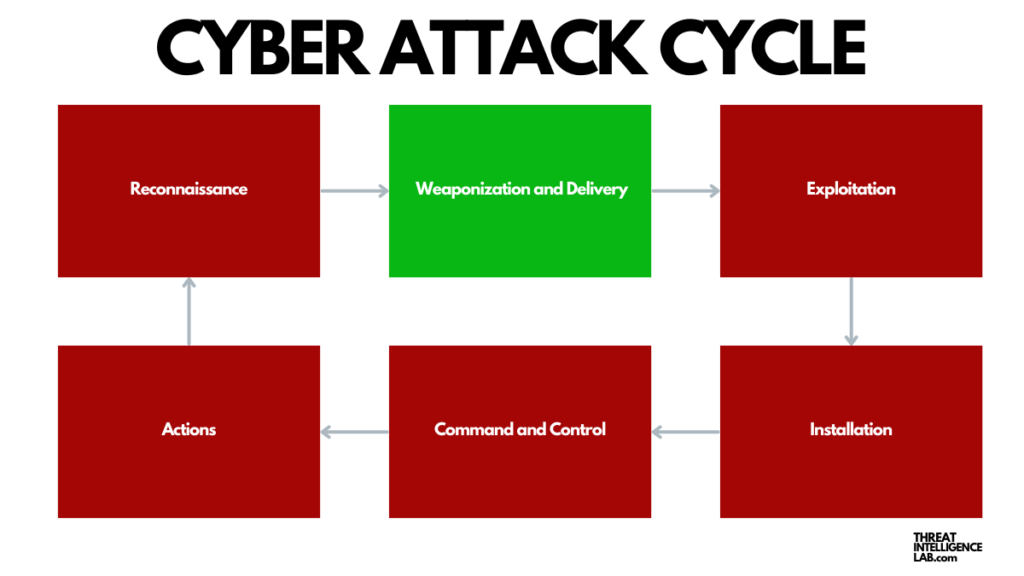
Here’s what happens: an attacker selects or develops malware tailored to their target’s vulnerabilities.
This could be a ransomware, a remote access Trojan, or any other form of malicious software. The malware is then embedded into seemingly benign carriers like PDFs, Word documents, or software updates.
- Cyber Attack Cycle: Actions Phase
- Cyber Attack Cycle: Command & Control (C2)
- Cyber Attack Cycle: Installation Phase
- Cyber Attack Cycle: Exploitation Phase
- Cyber Attack Cycle: Weaponization and Delivery
The Role of Delivery in the Attack Cycle
Following weaponization, the delivery phase kicks in. This is when the weaponized content is dispatched to the target via various channels. Common methods include phishing emails, malicious links, or even physical means such as USB drives.
Essentially, delivery is all about how the payload reaches the target environment without raising alarms.
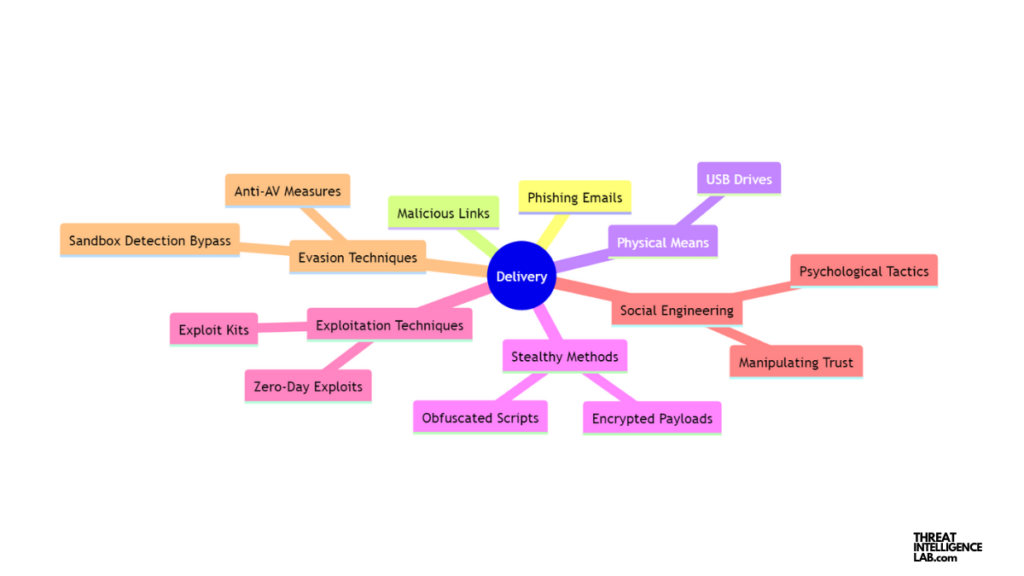
The MITRE ATT&CK Framework: Weaponization and Delivery Tactics
The MITRE ATT&CK framework is a gold mine for anyone in cybersecurity. It categorizes and describes various tactics and techniques used by threat actors.
Under the categories related to weaponization and delivery, you’ll find detailed tactics including:
- Spearphishing: This involves sending emails to targeted individuals that appear to come from a trusted sender to induce them to reveal confidential information.
- Exploitation of Public-Facing Applications: Attackers exploit vulnerabilities in software that is accessible from the Internet to deliver a payload.
- Drive-by Compromise: This technique involves compromising a website so that it attempts to exploit vulnerabilities in a visitor’s browser to download and execute a payload secretly.

Best Practices for Defending Against Weaponization and Delivery
To defend against the weaponization and delivery phases of a cyber attack, I recommend the following strategies:
- Educate Your Team: Regular training on the latest phishing and social engineering tactics will harden your first line of defense—your employees.
- Implement Strict Email Filters: This reduces the chances of phishing emails reaching your employees.
- Keep Systems Updated: Ensure that all software is up-to-date to minimize vulnerabilities that can be exploited.
Deploying Detection Mechanisms
Moreover, deploying advanced detection mechanisms can help identify and neutralize threats before they activate.
Solutions like endpoint detection and response (EDR) and network detection and response (NDR) are critical. They monitor for suspicious activities related to the delivery and execution of malicious payloads.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
Continuous Learning and Adaptation
Lastly, the best way to stay ahead is by continuously adapting your security posture. Engage with communities, participate in security forums, and keep abreast of the latest in threat intelligence.
Regularly revisiting your security strategies based on new information and evolving threats ensures that your defenses remain robust.
Conclusion
Weaponization and Delivery are pivotal stages in the cyber attack cycle. They represent the preparation and actual movement of the threat into the target’s environment.
By understanding and implementing strong defensive measures against these phases, you can significantly reduce your vulnerability to cyber attacks. Stay vigilant, stay informed, and most importantly, stay proactive in your cybersecurity practices. Remember, the best defense is a good offense.
Continue with the cyber attack cylcle
