Your cart is currently empty!
Cyber Attack Cycle: Reconnaissance Attacks
The reconnaissance stage, the initial step in the widely recognized Cyber Attack Cycle or “Cyber Kill Chain” developed by Lockheed Martin, focuses on actively gathering information.
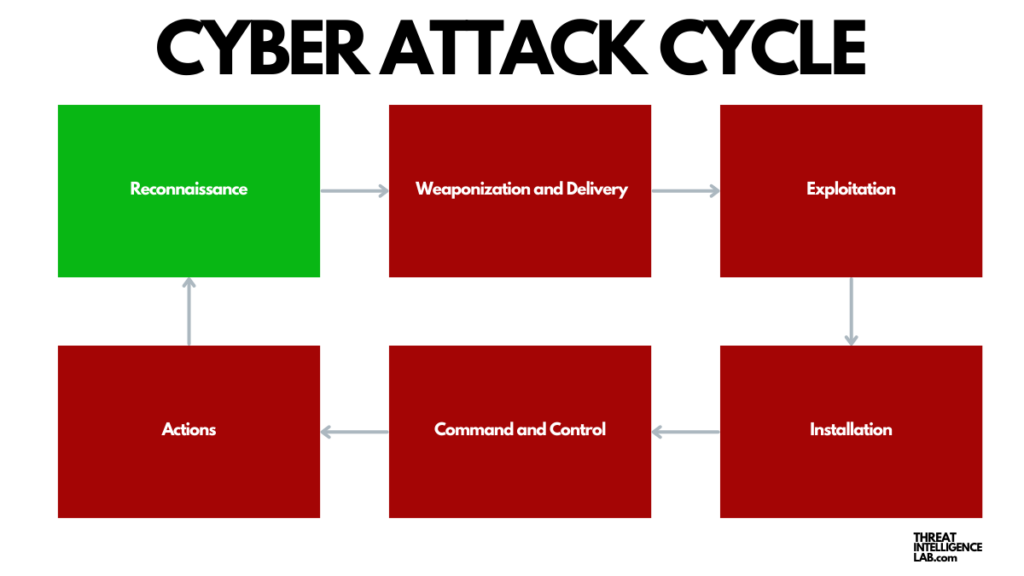
In this detailed exploration, I will try to explain the reconnaissance phase.
The Anatomy of Cyber Reconnaissance
Reconnaissance1 fundamentally serves as an intelligence-gathering mission.
Cyber attackers use this phase to build a comprehensive profile2 of their target, whether an individual, a corporation, or a government entity.
The goal here is to collect enough data to facilitate subsequent attacks, making this phase both stealthy and critical for the attackers’ success.

Types of Data Gathered
During reconnaissance, attackers hunt for a variety of data:
- Technical Information: They gather details on network infrastructures, such as IP addresses, domain details, server locations, and security frameworks.
- Personal Data: They collect information about key personnel, including job roles, contact information, and social media activities.
- Operational Insights: They look for internal communication methods, company routines, and any upcoming events that might be exploited.
To give you a simple view, the data gathered might look like this.
| Types of Data Gathered | Example Data |
|---|---|
| Technical Information | IP addresses: external_ip_list, Domain details: example.com, Server locations: Data center A, Security frameworks: Firewall: Cisco ASA |
| Personal Data | Key personnel: John Doe (CEO), Job roles: System Administrator, Contact information: johndoe@example.com, Social media activities: LinkedIn: JohnDoe123 |
| Operational Insights | Internal communication methods: Slack channels #engineering, Company routines: Weekly meetings every Monday at 9:00 AM, Upcoming events: Product launch on May 15th |
Methods of Information Gathering
Attackers deploy various techniques3 to gather this data, typically categorizing them into passive and active reconnaissance:
- Passive Reconnaissance: Here, attackers collect information without directly interacting with the target’s systems. They might:
- Purchase Data: Buy information from dark web sources or through legal means like marketing databases.
- Exploit Public Databases and Websites: Access publicly available resources where sensitive information might inadvertently be exposed.
- Analyze Social Media: Scrutinize profiles and posts to gather personal and professional information about employees and company operations.
- Active Reconnaissance: This technique involves more direct interaction with the target’s systems but still aims to avoid detection. Methods include:
- Use Scanning Tools: Employ tools to scan for open ports and vulnerabilities in the network infrastructure.
- Conduct Phishing Attempts: Send emails or messages to elicit additional information or to map out organizational structures.
Strategies to Counter Cyber Reconnaissance
To defend against the reconnaissance phase of a cyber attack, organizations must implement4 comprehensive and proactive measures:
1. Conduct Regular Security Audits
Scheduling regular audits is essential. These audits help you:
- Identify and rectify vulnerabilities in your network that could be exploited during reconnaissance.
- Understand what data is publicly accessible.
- Evaluate the security of your web presence and other digital assets.
- Adjust policies to limit data exposure.
2. Enhance Data Management and Sharing Policies
Controlling what information you share publicly and how you share it can significantly reduce the risk of it being used against your organization. You should implement strict data management policies that:
- Limit the exposure of sensitive operational and personal information on social media and corporate websites.
- Ensure that employees understand the implications of sharing too much information (online).

3. Deploy Advanced Monitoring and Detection Systems
You should also deploy cybersecurity tools to continuously monitor your digital footprint. These tools can:
- Detect unusual activities that may indicate an ongoing reconnaissance effort.
- Alert you when sensitive information is accessed or when abnormal data scraping activities are detected.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
Challenges and Strategies in Monitoring External Reconnaissance Activities
Most reconnaissance activities conducted by cyber attackers occur outside the secure confines of a company’s network and infrastructure.

This external reconnaissance poses significant challenges for organizations, as it limits their ability to monitor and understand the scope of information being gathered by adversaries.
Attackers often gather actionable intelligence from public sources, social media, forums, and other digital platforms where companies have little to no control.
Without robust external monitoring capabilities, it becomes difficult for organizations to gauge what is being said and done about them in these open environments.
Reza Rafati
The Role of Cyber Threat Intelligence (CTI) in External Monitoring
Cyber Threat Intelligence (CTI) plays a pivotal role in addressing the challenges of monitoring external activities.
CTI involves the collection and analysis of information about current and potential attacks that threaten the safety of an organization’s digital assets.
Here’s how CTI enhances the capability to monitor:
- Internet-Wide Scanning and Data Aggregation: CTI tools can scan and aggregate data from across the internet, including dark web sources where attackers often trade tools and stolen data. These tools can identify when information related to a company is being discussed or sold online.
- Domain Monitoring: CTI helps in monitoring domain registrations that mimic or closely resemble the company’s domain. This is often a precursor to phishing attacks or other forms of cyber deception aimed at customers or employees.
- Social Media and Forum Monitoring: Advanced CTI solutions scan social media platforms and forums for mentions of the company or its products. This monitoring helps in identifying campaigns that might be in the planning stages, providing early warnings about potential threats.
- Analyzing Trends and Tactics: CTI not only tracks specific threats but also analyzes broader trends and tactics used by cyber criminals. This analysis helps in understanding the evolving tactics that might be used in reconnaissance activities, allowing companies to adapt their security measures accordingly.
- Enhanced Situational Awareness: By providing actionable intelligence, CTI enhances situational awareness. This allows security teams to understand the context of the threats they face, prioritizing their responses and aligning their defense strategies more effectively with the actual risk landscape.
- Collaborative Threat Sharing Platforms: Participating in threat sharing platforms enables organizations to exchange information about threats, including those identified through external reconnaissance activities. This collaboration can lead to a more comprehensive defense strategy against common adversaries.
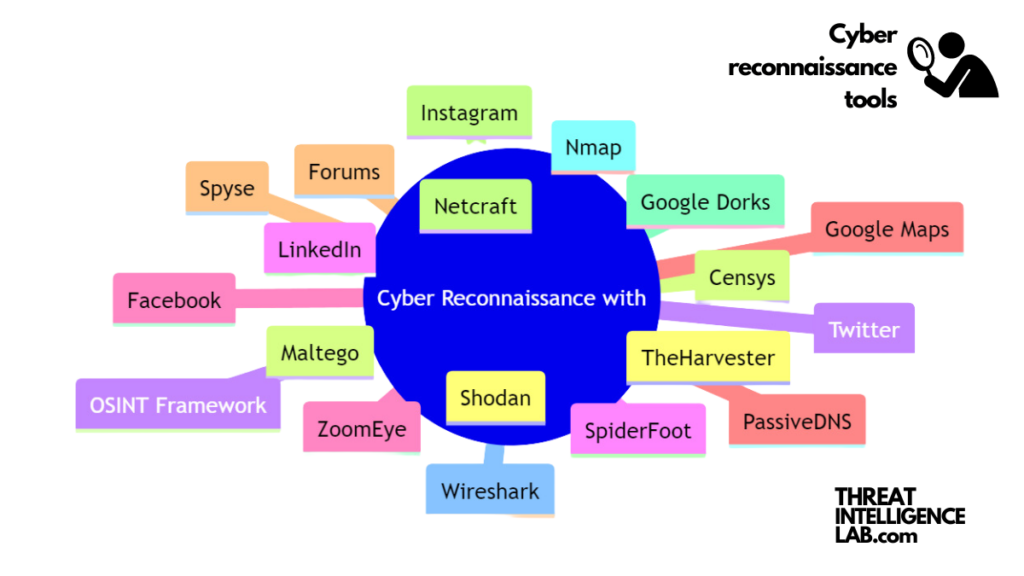
Tools for cyber reconnaissance
These tools actively probe networks, uncover vulnerabilities, and stealthily gather valuable data, all while avoiding triggering alarms.
Below, I’ll list some of the commonly used tools in cyber reconnaissance:
- Nmap (Network Mapper): A powerful and versatile tool used for network discovery and security auditing. Nmap allows attackers to identify what hosts are available on the network, what services those hosts are offering, and what operating systems and firewall types they are running.
- Shodan: Often referred to as the “search engine for hackers,” Shodan scans the entire internet and provides information about devices connected to it, including servers, webcams, printers, and routers. It is particularly useful for finding specific devices vulnerable to attacks.
- Wireshark: A network protocol analyzer that lets users capture and interactively browse the traffic running on a computer network.
- Maltego: An interactive data mining tool that renders directed graphs for link analysis. Maltego users actively gather information on relationships and real-world links between individuals, groups, websites, networks, domains, and Internet infrastructures.
- TheHarvester: A tool designed for gathering e-mail accounts, subdomain names, virtual hosts, and other related information from different public sources (search engines, social networks).
Wrapping it up
By understanding the nuances of the reconnaissance phase and adopting a layered defense strategy, organizations and you can significantly diminish the effectiveness of this initial cyber attack stage.
Implementing these defenses not only makes it harder for attackers to gather valuable information but also strengthens the overall resilience of your cybersecurity posture.
