One critical but often underestimated stage in the cyber attack cycle is the installation phase. This is the moment when the attacker secures their presence on the victim’s system, setting the stage for ongoing control or damage.
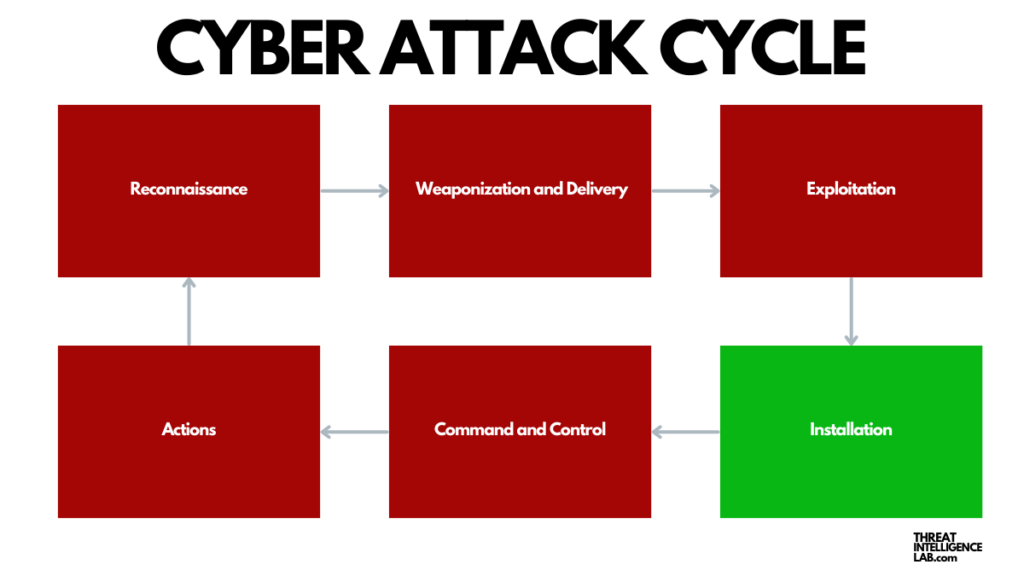
Understanding this phase is crucial for effectively defending against and responding to cyber threats.
The Significance of the Installation Phase
In the cyber attack lifecycle, the installation phase follows initial access, where the attacker uses various methods to gain entry into the network or system.
Once inside, the installation phase begins. Here, attackers deploy their malicious software (malware) to establish a foothold. This software can range from ransomware and viruses to spyware and backdoors.

Why is this phase so pivotal? Because it marks the transition from a breach to an ongoing intrusion. It’s where the attacker shifts from breaking in to setting up shop, so to speak. The installed malware allows attackers to maintain persistence within the host environment, making it challenging to detect and remove them.
- Cyber Attack Cycle: Actions Phase
- Cyber Attack Cycle: Command & Control (C2)
- Cyber Attack Cycle: Installation Phase
- Cyber Attack Cycle: Exploitation Phase
- Cyber Attack Cycle: Weaponization and Delivery
Common Techniques Used in the Installation Phase
Attackers use a variety of techniques to ensure their malicious software remains on the system undetected:
- Rootkits: These are tools that help an attacker maintain access to a system without being detected. Rootkits can manipulate operating systems to hide the presence of malware or other malicious activities.
- Trojans: Often disguised as legitimate software, Trojans provide a backdoor for malicious activities while appearing harmless.
- Fileless Malware: This type of malware resides in the memory and does not write any files to the disk, making it difficult for traditional antivirus solutions to detect.
- Polymorphic Malware: This malware changes its code or signature pattern automatically to evade detection by signature-based security tools.
Defense Strategies Against Installation Attacks
The best way to mitigate the risk of the installation phase is through proactive and robust cybersecurity measures:
- Regular Software Updates: I recommend that you keep all software updated. Attackers often exploit vulnerabilities in outdated software to install malware.
- Advanced Threat Detection Tools: Utilize tools that can detect anomalies in system behavior, including the use of fileless and polymorphic malware.
- Application Whitelisting: Only allow approved programs to run on critical systems, reducing the chance of malicious software installations.
- User Training and Awareness: Educate users on the risks of installing unverified software and the importance of following organizational security policies.
Real-World Examples of Installation Attacks
To illustrate the significance of the installation phase, let’s consider some real-world incidents. Major breaches often involve the use of (sophisticated) malware installed during this phase.
For instance, the notorious Stuxnet worm used in cyber attacks on industrial control systems was installed on the target network where it remained undetected for a considerable time, manipulating real-world equipment.
Another example is the Dyre banking Trojan, which, once installed, allowed attackers to steal login credentials and intercept financial transactions. These cases underscore the critical nature of early detection and robust defense strategies.

