Your cart is currently empty!

Cyber Attack Cycle: Exploitation Phase
This is the stage where attackers turn identified vulnerabilities into actual attacks, using known methods to breach security.
Today, I’ll explain why this phase is pivotal, outline common techniques attackers use, and show you how to defend your systems effectively.
Understanding the Exploitation Phase
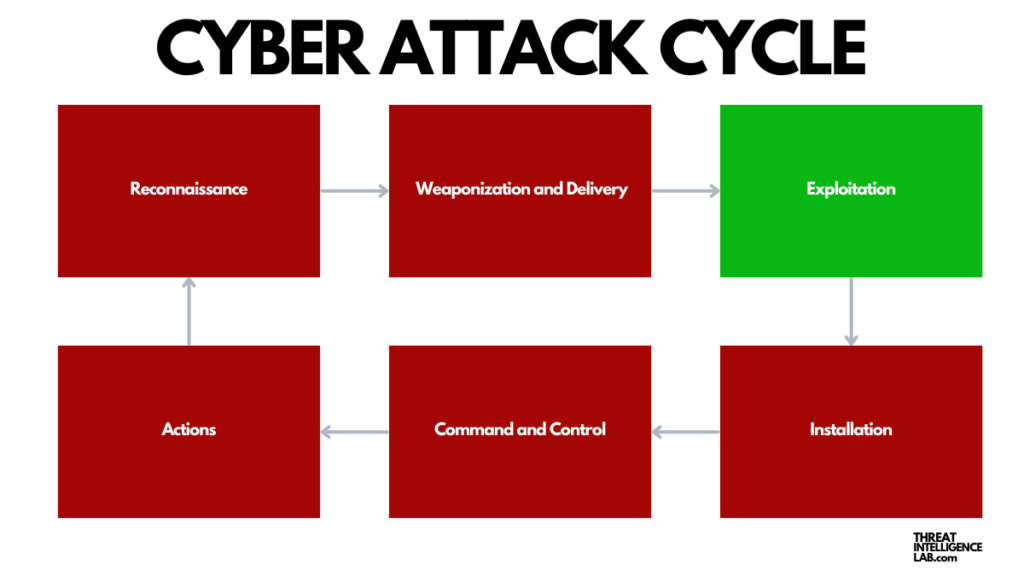
In the exploitation phase, the action heats up: attackers have already scoped out vulnerabilities and now they actively exploit them to insert malicious code or to hijack legitimate processes.
This phase is the bridge between planning and executing a cyber attack, making it a critical point for intervention.
Key Differences Between The Weaponization and Exploit phase
- Focus: The Weaponization and Delivery phases focus on preparation and transmission of the attack tools to the target, without any harm being done yet. These phases are about setting the stage for the attack. In contrast, the Exploitation Phase is about action—activating the attack to achieve the harmful outcomes.
- Sequence: In the cyber attack cycle, weaponization and delivery come before exploitation. The tools must be prepared and delivered before they can be used to exploit vulnerabilities.
- Outcome: The output of the weaponization and delivery phases is the placement of a malicious tool within reach of the target, set up for future activation. The exploitation phase’s output is the execution of that tool, resulting in a successful attack.
Techniques Attackers Use
- Exploit Kits: Cybercriminals use these pre-packaged tools to automate the exploitation of known software vulnerabilities. They are dangerous because they allow quick and broad attacks with minimal effort.
- Zero-Day Exploits: These are vulnerabilities unknown to software vendors and hence unpatched. Attackers using zero-day exploits can often evade detection by conventional security tools, making them particularly threatening.
- Phishing Attacks: Exploitation often involves tricking users into compromising their own security. Phishing is a common method, where attackers coax users into making harmful decisions, like divulging passwords or installing malware.
Defending Against Exploitation
Implement Rigorous Patch Management
To shield your systems from attacks, rigorously update and patch your software. Setting up automated patch updates can close vulnerabilities before attackers can exploit them. I advise you to prioritize this process to keep your defenses strong.

Deploy Advanced Threat Detection Systems
Invest in advanced threat detection technology that can spot exploitation attempts as they happen. These systems use behavioral analytics and machine learning to detect unusual patterns that might indicate an attack, providing real-time defense.
Conduct Continuous Security Training
Many exploits require user interaction, so training your staff to recognize and resist phishing and other tactics is crucial.
Opt for ongoing security awareness programs that adapt to new threats. The most effective defense involves informed users who can spot and stop attacks.
- Cyber Attack Cycle: Actions Phase
- Cyber Attack Cycle: Command & Control (C2)
- Cyber Attack Cycle: Installation Phase
- Cyber Attack Cycle: Exploitation Phase
- Cyber Attack Cycle: Weaponization and Delivery
Staying Proactive Against Threats
Understanding and defending against the exploitation phase is crucial. It’s where potential threats turn into actual attacks.
By learning about attacker techniques and bolstering your defenses, you can significantly reduce your vulnerability.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
Remember, proactive defense is your best strategy against cyber threats. Keep your technology and team ready and resilient against any cyber assault.
By fostering a culture of continuous improvement and vigilance, you empower your organization against the evolving landscape of cyber threats.
