Your cart is currently empty!

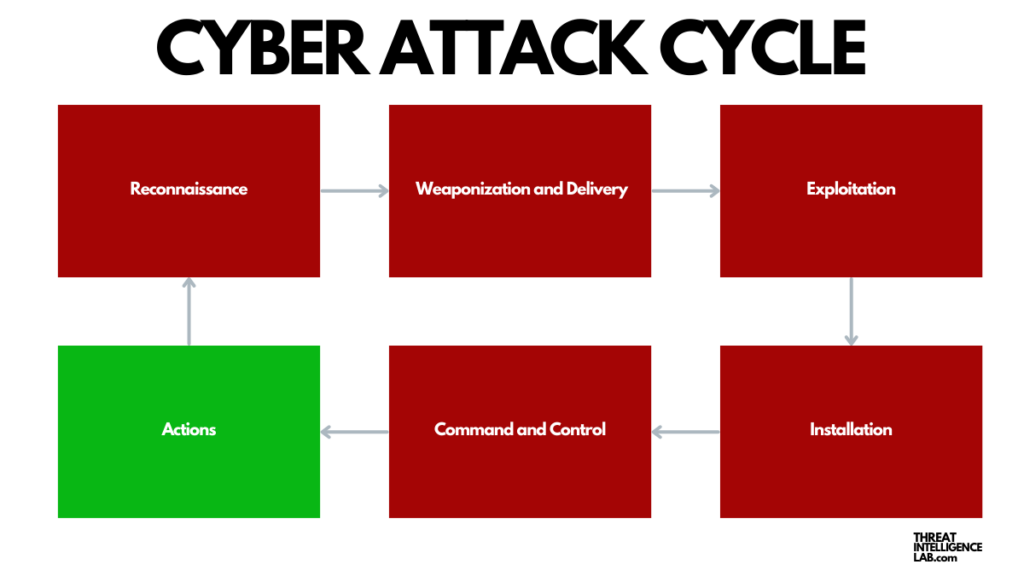
Cyber Attack Cycle: Actions Phase
This phase, also known as the “actions on objectives” stage, is where the intruder’s plans culminate, whether stealing data, deploying ransomware, or causing operational disruption.
Importance of the Actions Phase
Following the command and control phase, attackers are poised to carry out their intended actions.
They might extract valuable data, execute destructive commands, or leverage access for financial gain.
This phase reveals the real intent of the attackers, making it a crucial point for defense teams to intervene and prevent significant damage.
The danger lies not just in the immediate impact but also in the potential long-term repercussions, such as loss of customer trust, legal consequences, and financial setbacks.
- Cyber Attack Cycle: Actions Phase
- Cyber Attack Cycle: Command & Control (C2)
- Cyber Attack Cycle: Installation Phase
- Cyber Attack Cycle: Exploitation Phase
- Cyber Attack Cycle: Weaponization and Delivery
Tactics and Tools Used During the Actions Phase
Attackers deploy a range of tactics and tools to achieve their goals during this phase:
- Data Exfiltration: Attackers stealthily transfer data from the victim’s network to their own systems. They may use encrypted channels or stagger the transfers to avoid detection.
- Ransomware: By encrypting vital data and systems, attackers hold an organization hostage, demanding payment for the decryption keys.
- Destructive Attacks: These include deleting critical data or disabling networks and systems to disrupt operations, often as a smokescreen for other malicious activities.
- Persistence Mechanisms: Attackers establish ways to maintain access to the network for future attacks and continuous exploitation.
Defending Against the Actions Phase
Effective defense against the actions phase requires a proactive and layered security approach:
- Implement Robust Data Loss Prevention (DLP) Systems: These systems monitor and control data endpoints, ensuring sensitive information does not leave the network without authorization.
- Utilize Behavior Analytics: By analyzing normal user behaviors, these tools can detect anomalies that may indicate unauthorized actions, such as unusual access patterns or large data transfers.
- Conduct Regular Backups: Maintain frequent and secure backups of critical data. In the event of ransomware or destructive attacks, you can restore systems with minimal downtime.
- Employ Incident Response Teams: Have a skilled team ready to respond immediately to signs of a breach. Quick action can mitigate the damage by isolating affected systems and halting ongoing attacks.
Real-World Examples Demonstrating the Actions Phase
Consider the impact of the NotPetya attack, where malicious software not only encrypted data but also rendered systems inoperable, causing billions in damages across multiple global corporations.
Another example is the Sony Pictures hack, where attackers not only stole and released sensitive data but also wiped computers and servers, compounding the disruption and losses.
Concluding Thoughts on Actions Phase Defense
In conclusion, the actions phase is where cyber attacks have the most visible and potentially devastating effects.
By understanding the tactics used and implementing strong, proactive defenses, organizations can protect themselves from significant harm.
Remember, the best defense strategies are those that are not only reactive but also predictive, helping to spot and stop attacks before they reach their objectives.
