The Cyber Attack Cycle
Understanding the cyber attack cycle is crucial for anyone tasked with defending their organization’s digital assets.
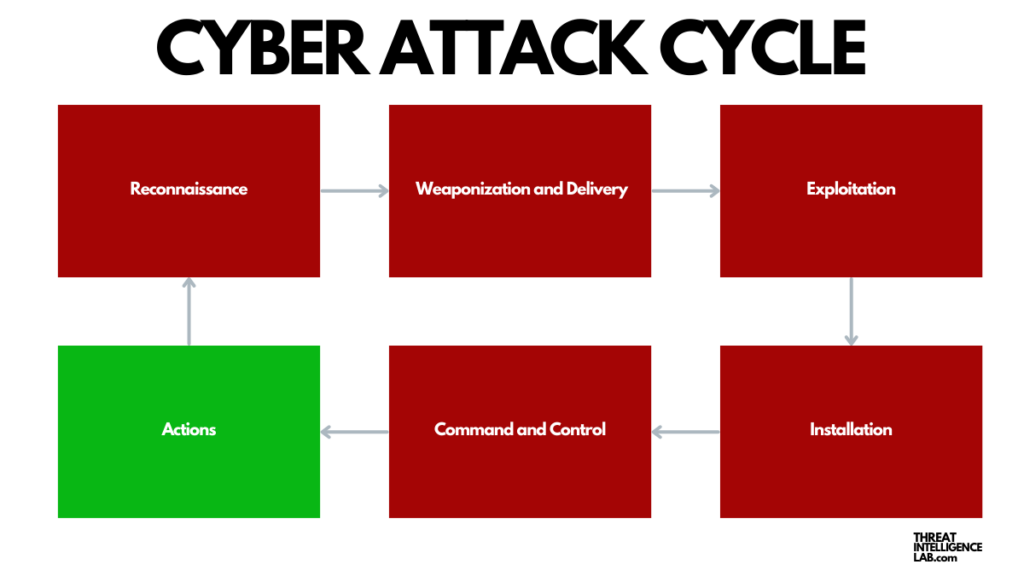
The cycle, often referred to as the “cyber kill chain,” consists of several distinct phases that cybercriminals pass through to complete their objectives.
Knowing these stages arms us with the foresight to preempt potential threats, transforming our approach from reactive to proactive.
This shift is vital in today’s digital landscape where attackers continually refine their strategies.
Below, we delve into each phase of the cycle, emphasizing proactive defenses that can effectively thwart these threats.
The Cyber Attack Cycle
Reconnaissance: Scouting the Target
The cyber attack cycle begins with reconnaissance. In this initial phase, attackers identify and research their targets. They use various methods such as social engineering, accessing public databases, and direct probing of networks to gather crucial information about potential vulnerabilities. This foundational information-gathering sets the stage for all subsequent phases, helping attackers pinpoint where and how they can most effectively strike.
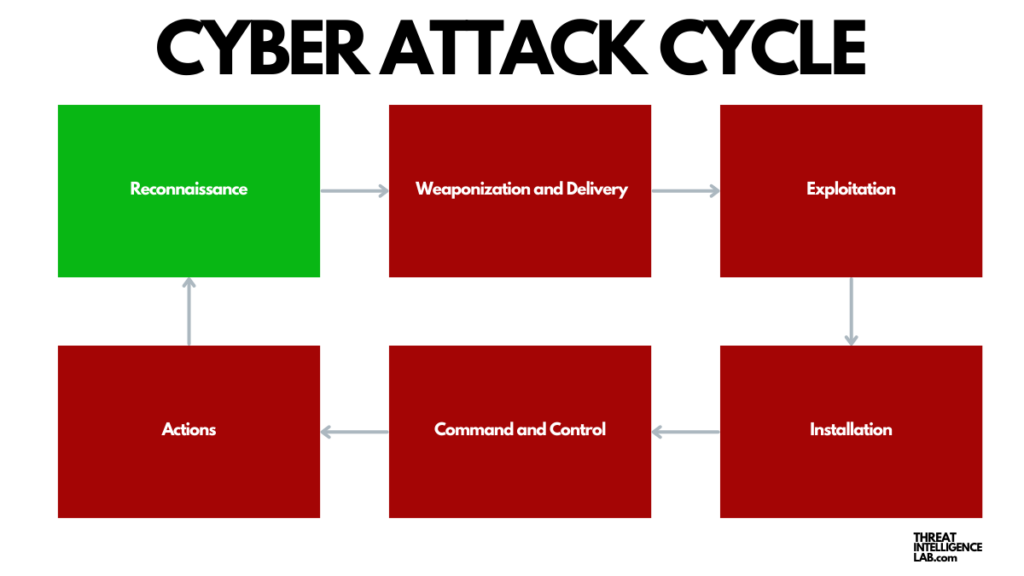
Weaponization: Crafting the Threat
After collecting enough information, attackers move to the weaponization phase. Here, they develop malware or create specific exploits tailored to the vulnerabilities they’ve uncovered during reconnaissance. They conduct this phase in secrecy, preparing the tools needed to execute their breach. The crafted payload is designed to exploit weaknesses in software or systems, facilitating unauthorized access or damage.
Delivery: Launching the Attack
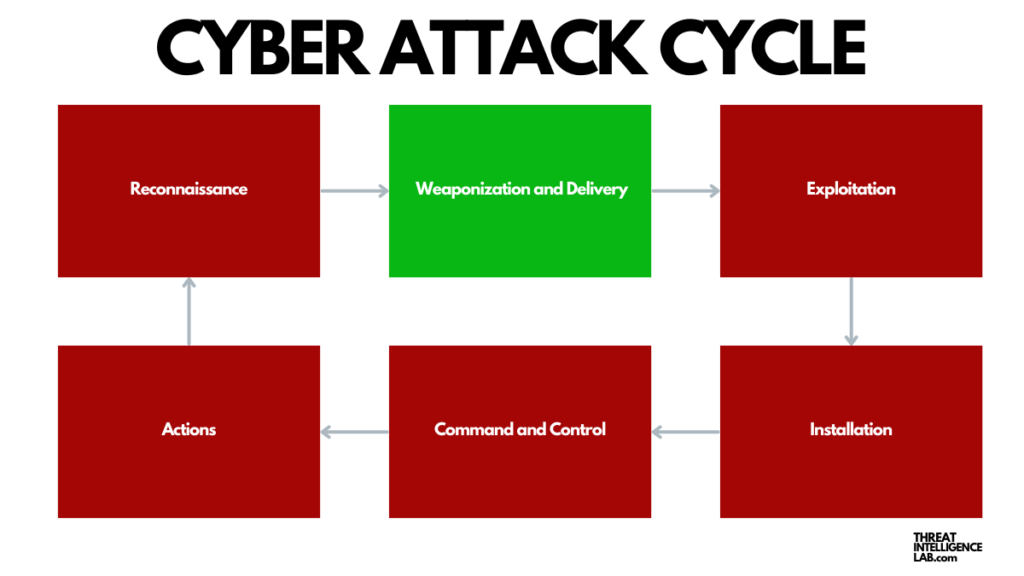
Next, in the delivery phase, attackers transmit the weaponized payload to the target. They may use various channels such as phishing emails, malicious attachments, compromised websites, or even direct network intrusion. The objective here is to insert the crafted malicious tool into the target’s environment without detection, setting the stage for the next critical step of the attack.
Exploitation: Gaining Entry
Following delivery, the exploitation phase begins. It is the actual act of breaching the target’s defenses using the delivered payload. The exploit activates upon delivery, exploiting the identified vulnerabilities to execute unauthorized commands, typically resulting in an initial compromise of the system. This phase is usually swift and tests the effectiveness of the weaponized payload.
Dive deeper into each phase
- Cyber Attack Cycle: Actions Phase
- Cyber Attack Cycle: Command & Control (C2)
- Cyber Attack Cycle: Installation Phase
- Cyber Attack Cycle: Exploitation Phase
- Cyber Attack Cycle: Weaponization and Delivery
- Cyber Attack Cycle: Reconnaissance Attacks
Installation: Securing Presence
Once the system has been breached, the installation phase starts. During this phase, the attacker installs additional malicious software to establish a persistent presence within the victim’s system.
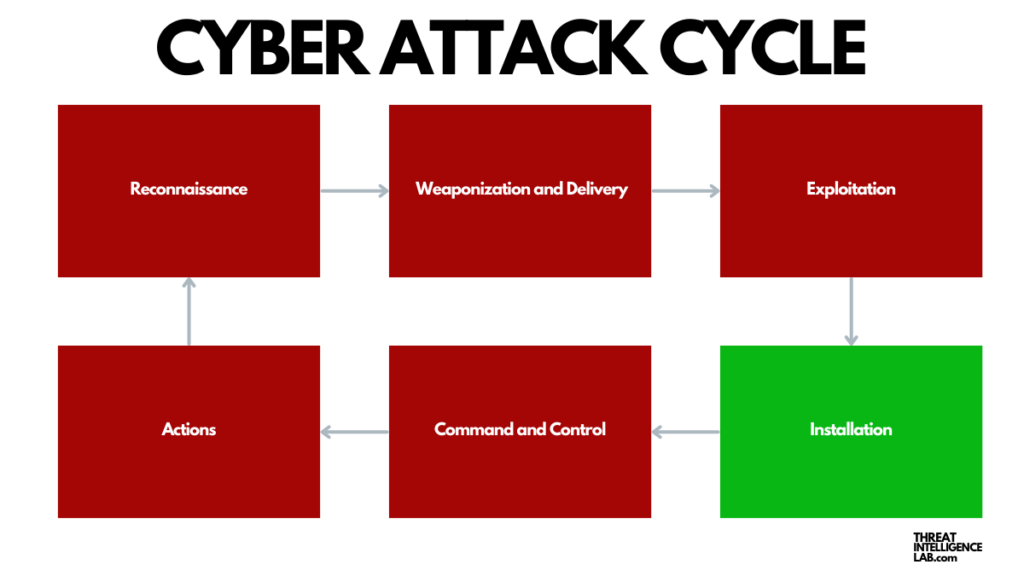
This allows the attacker continued access and control, even in the event of system reboots or updates. The installed software also helps conceal the attacker’s activities from detection systems and administrators.
Command and Control (C2)
After installing the malicious software, the malware attempts to establish a command and control (C2) channel.
This channel connects the compromised system back to the attacker’s server.
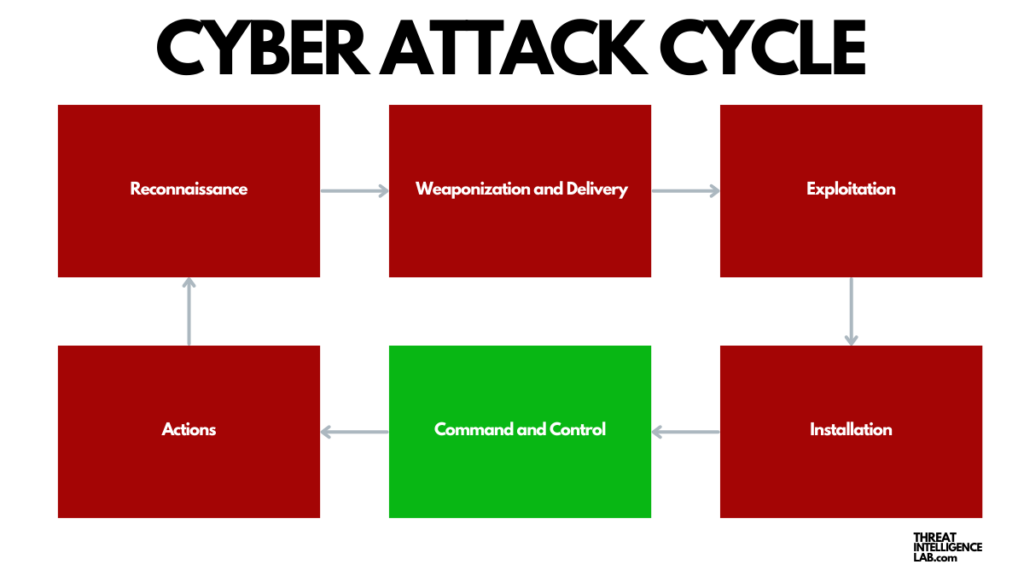
Through this connection, the attacker can command the malware, receive data from it, send further instructions, and effectively control the compromised system.
This phase is crucial for maintaining influence over the breach and coordinating subsequent actions.
Actions on Objectives: Achieving the Endgame
Finally, the attacker executes their intended actions in the actions on objectives phase. At this point, they use the access and control gained from previous phases to carry out their goals.
These objectives can vary widely, from data theft and espionage to ransomware deployment and sabotage. This phase realizes the attacker’s initial goals, culminating the attack cycle.