Your cart is currently empty!
Malware analysis is all about understanding how malware works, the different types it comes in, how it’s used in real situations, and the tools needed to investigate and analyze it thoroughly.
It helps uncover the behavior, purpose, and potential impact of malicious software.
This guide will walk you through the key aspects of malware analysis, its benefits, stages, types, and the tools used in the process.
Malware Analysis Definition
Malware analysis is the diligent study of malicious software to understand its unique features, objectives, origins, and potential effects. This involves examining harmful code like spyware, viruses, malvertising, and ransomware.
By analyzing malware, security professionals can determine how it operates, identify its source, and mitigate its effects on systems.
To put it simply, think of malware analysis as a detective process. Just as a detective examines evidence to solve a crime, cybersecurity experts examine malware to understand how it works and how to stop it.
This process involves looking at the code of the malware, seeing what it does without running it, and even running it in a controlled environment to observe its behavior. All these steps help in creating defenses against such attacks and preventing future incidents.
Benefits of Malware Analysis
Malware analysis offers several significant advantages, including:
- Damage Assessment: It helps quantify the damage caused by malware intrusions.
- Attacker Identification: Pinpoints who might have installed the malware.
- Sophistication Level: Determines the complexity of the attack.
- Vulnerability Identification: Reveals the exact vulnerabilities exploited by the malware.
These insights are critical for strengthening an organization’s cybersecurity posture and preparing for future threats.
Understanding these benefits is crucial for anyone new to cybersecurity. Imagine your computer gets infected by a virus.
Without analyzing the malware, you wouldn’t know how much damage it has done or who might have sent it. By identifying the vulnerability, you can fix the weak spot in your defenses.
This is like fortifying a breached wall to ensure no future invasions. Identifying the attack’s sophistication helps in gauging the skill level of the attacker, allowing you to tailor your defenses accordingly.
Stages of Malware Analysis
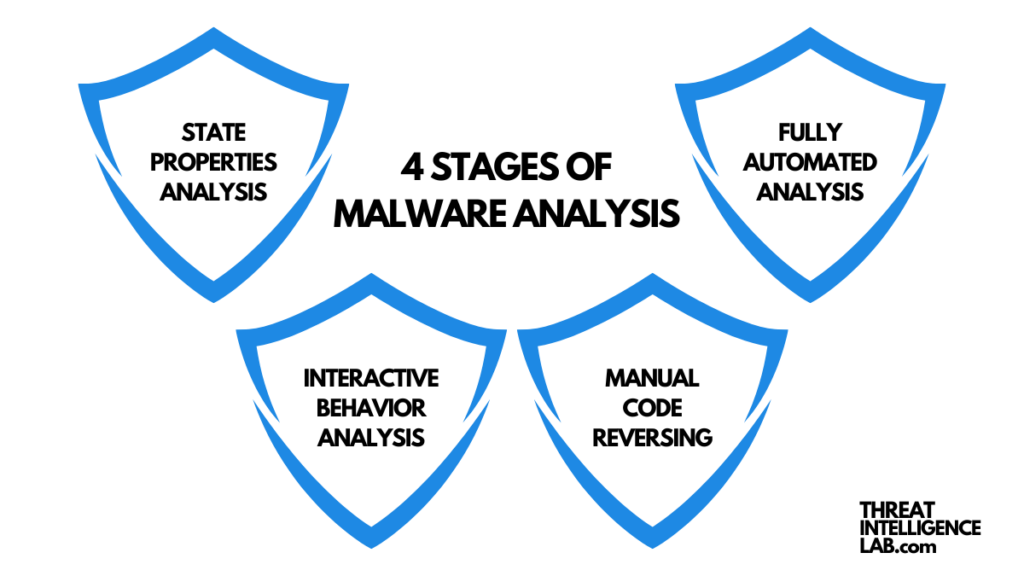
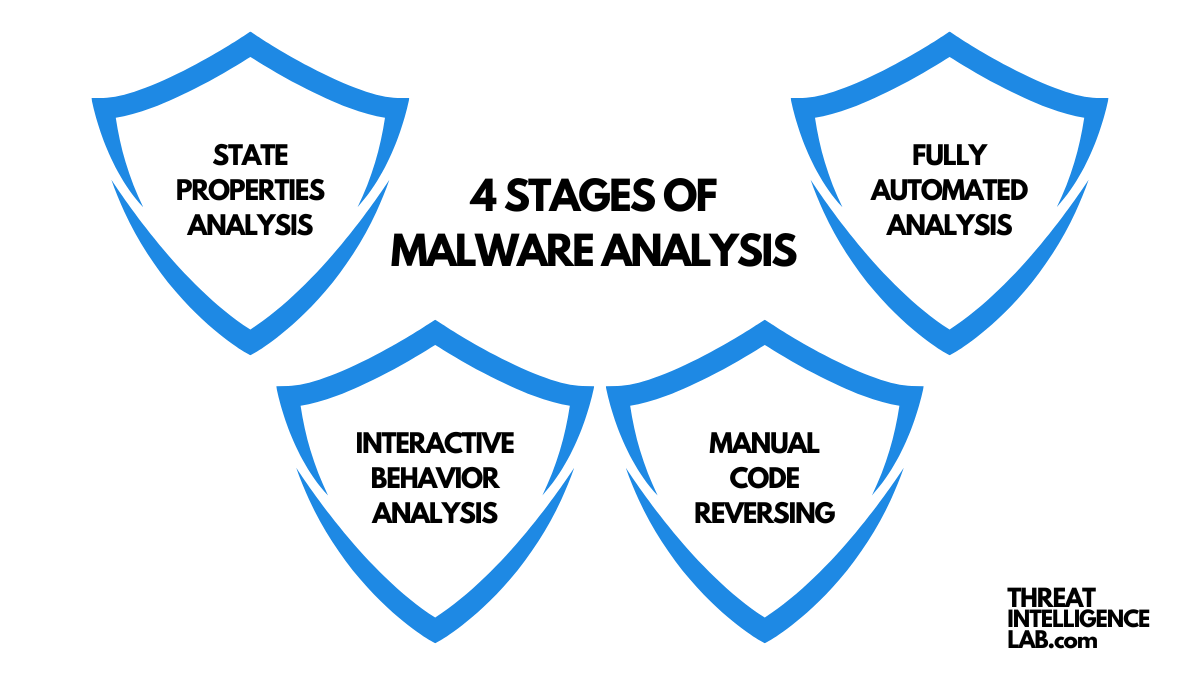
The process of malware analysis can be broken down into four key stages:
Static Properties Analysis
This initial stage involves examining the malware file’s static properties without executing it. Analysts look at embedded strings of code, hashes, header details, and metadata. This quick and safe method provides valuable information about the malware’s nature.
In static analysis, experts read the code without running it. They check for known patterns and clues that indicate if the code is malicious. This helps in quickly identifying threats without risking the system’s safety.
Interactive Behavior Analysis
In this stage, a security analyst interacts with the malware running in a controlled environment, observing its behavior. This helps in understanding how the malware manipulates system resources like memory and files.
By observing the malware’s actions in a controlled setting, analysts can see what files it tries to access or change and how it affects the system’s memory. This interaction gives a clearer picture of the malware’s capabilities and intentions.
Fully Automated Analysis
Automated tools scan the malware to assess what it can do once inside a system. This approach generates a comprehensive report, detailing the potential impact and assisting in the rapid identification of threats.
Automated analysis is akin to using a high-tech security scanner that quickly checks for harmful items. These tools are programmed to look for specific behaviors and generate reports that outline the malware’s potential damage.
This method is fast and efficient, making it ideal for processing large volumes of potential threats.
Manual Code Reversing
This advanced stage involves dissecting the malware’s code to understand its construction and capabilities. Though time-consuming and requiring high expertise, manual code reversing can uncover deep insights into the malware’s functions.
Manual code reversing is like solving a complex puzzle. Experts take apart the malware’s code piece by piece to understand how it was built and what it does. This process is detailed and intricate, requiring significant skill.
However, it provides the deepest insights into the malware, revealing hidden functions and potential vulnerabilities it might exploit.
Types of Malware Analysis
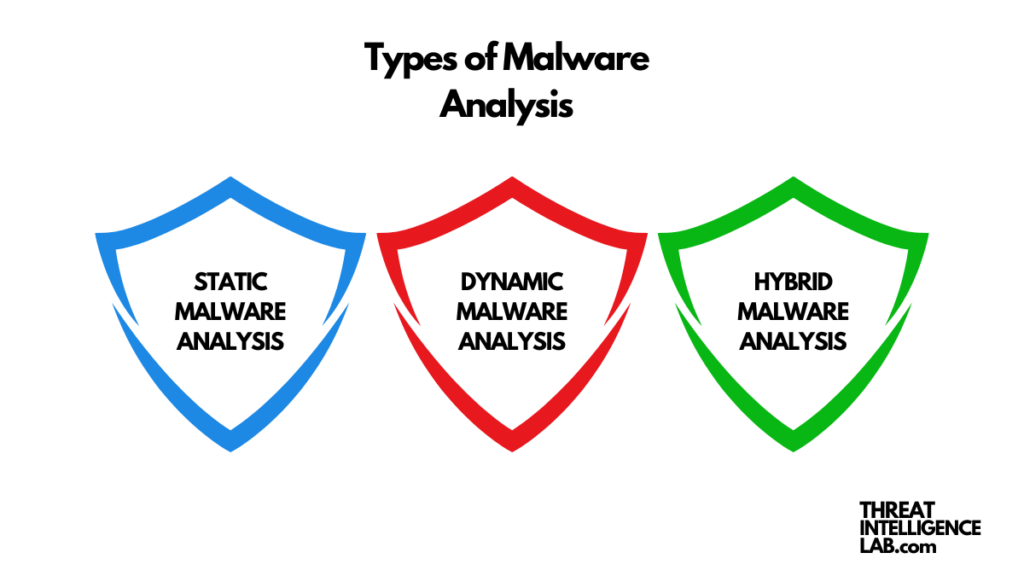
Depending on the situation, different types of malware analysis can be employed:
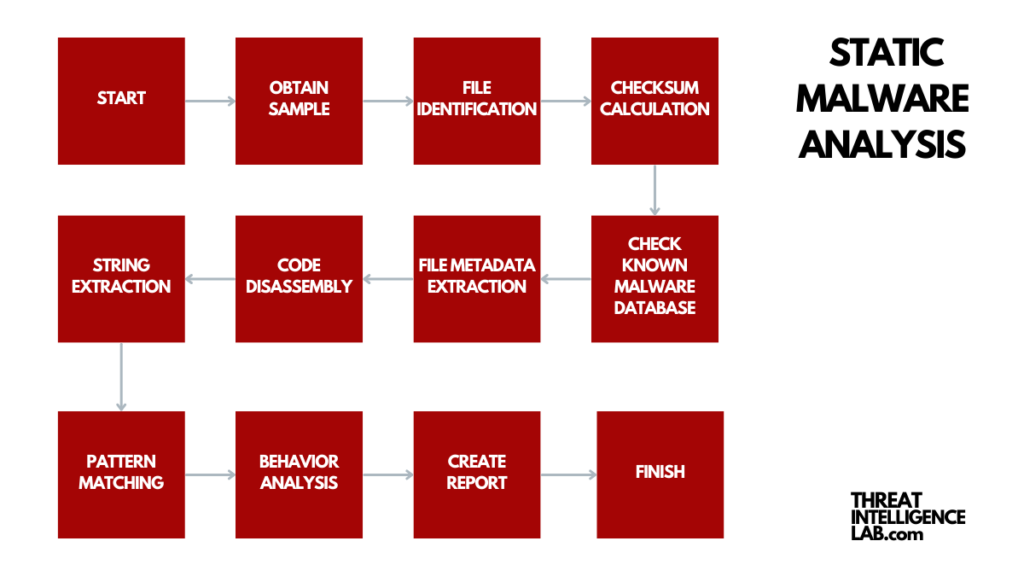
Static Malware Analysis
Static analysis examines malware files without executing the code, making it a safe method for identifying malicious components.
It reveals clues like filenames, hashes, IP addresses, domains, and file header data, providing a foundational understanding of the malware.
Static analysis is like a detective gathering clues from a crime scene without disturbing anything.
By examining these clues, experts can piece together the nature of the threat. This method is non-intrusive and safe, making it a crucial first step in malware analysis.
Dynamic Malware Analysis
Dynamic analysis runs the suspected malware in a secure, isolated environment known as a sandbox. This allows security professionals to observe the malware’s behavior in real-time without risking the actual system.
Dynamic analysis is akin to watching a criminal in action through a one-way mirror. The sandbox environment ensures that the malware can’t escape or cause harm, while experts monitor its actions. This real-time observation provides valuable insights into how the malware operates and what damage it might cause.
Hybrid Malware Analysis
Hybrid analysis combines static and dynamic techniques. This method is particularly effective because it can detect hidden malicious activities and provide a comprehensive view of the malware’s behavior.
Hybrid analysis is like combining the detective’s careful examination of a crime scene with the real-time observation of a criminal’s actions.
By using both methods, experts get a complete picture of the malware. This approach helps in identifying sophisticated threats that might hide their malicious activities in one type of analysis but reveal them in another.
Tools for Malware Analysis
Several tools are available to aid in malware analysis:
Process Hacker
This tool allows analysts to monitor processes running on a networked device, providing insights into how malware affects different systems.
Process Hacker is like a high-tech surveillance system. It watches all the processes on a device, helping experts see which ones are behaving suspiciously. This detailed monitoring helps in identifying and understanding malware activity.
Fiddler
Fiddler serves as a proxy to observe and analyze network traffic, helping identify hardcoded malicious sites used by malware.
It inspects all incoming and outgoing data, identifying anything suspicious. This helps in catching malware trying to communicate with its control servers or download additional malicious components.
Limon
Limon is a sandbox environment tailored for studying malware that targets Linux systems, offering detailed behavior monitoring.
PeStudio
PeStudio analyzes potentially suspicious files, quarantining them and providing a hash for further safe analysis.
Ghidra
Ghidra disassembles malware code and translates it into readable format, offering deep insights into the malware’s design.
This tool takes apart the malware’s code and translates it into something that we can understand. This deep analysis reveals the malware’s inner workings and helps in designing effective countermeasures.
Cuckoo Sandbox
Cuckoo Sandbox runs malware in a controlled environment, recording its activity and generating detailed reports for further analysis. A valuable asset for anyone that is interested in automated malware analyis.
Hybrid Analysis
Hybrid analysis combines static and dynamic techniques, offering the best of both worlds. It can detect hidden malicious code and provide a comprehensive set of IOCs.
Hybrid analysis is like combining multiple investigative techniques to get a complete picture of the crime. By using both static and dynamic methods, experts can uncover hidden threats and gain a thorough understanding of the malware. This comprehensive approach helps in detecting and mitigating sophisticated attacks.
Common Malware Types and Their Impact

Understanding the different types of malware and their impacts can help in identifying and mitigating threats more effectively.
Some common types of malware include:
Viruses
Viruses attach themselves to clean files and spread throughout a system, damaging files and software.
Worms
Worms are similar to viruses but can spread independently, causing extensive damage by replicating rapidly across networks.
Trojans
Trojans disguise themselves as legitimate software but carry malicious payloads that can steal data or open backdoors for other malware.
Ransomware
Ransomware encrypts files and demands payment for the decryption key, causing significant financial and operational disruptions.
Spyware
Spyware secretly monitors user activity, collecting sensitive information like login credentials and personal data.
Each type of malware has a unique impact, and understanding these can help in tailoring defenses and response strategies.
Malware Analysis Use Cases
Malware analysis is essential in various cybersecurity scenarios:
Incident Response
Quick and accurate malware analysis is vital for incident response teams. It helps contain and mitigate ongoing attacks by providing actionable intelligence.
Incident response is like an emergency room for cybersecurity. When an attack occurs, time is of the essence. Malware analysis provides the necessary information to understand the attack, contain it, and prevent further damage. This quick response is crucial for minimizing the impact of an attack.
Malware Research and Detection
Understanding the differences between malicious and benign code is crucial for developing robust defenses. Malware analysis helps identify and blacklist sites that propagate threats.
Indicator of Compromise (IOC) Extraction
Malware analysis enables the extraction of IOCs, which are critical for detecting and preventing future attacks.
IOCs are like fingerprints left behind by a criminal. By identifying these indicators, experts can recognize signs of an attack and take preventive measures.
This helps in creating early warning systems that detect and stop threats before they cause significant harm.
Threat Hunting
They use malware analysis to identify previously unknown threats, enhancing the organization’s overall security posture.
By actively searching for threats, rather than waiting for an attack, experts can discover and neutralize potential risks. This proactive approach helps in staying ahead of cybercriminals.
Threat Alerts and Triage
Malware analysis helps prioritize threats based on severity, enabling security teams to focus on significant risks and reduce false positives.
Threat alerts and triage are like prioritizing patients in an emergency room. By focusing on the most severe threats first, security teams can address the most critical risks promptly. This efficient allocation of resources ensures that the most dangerous threats are dealt with quickly.
Challenges in Malware Analysis
Despite its importance, malware analysis presents several challenges that security professionals must overcome.
Evasion Techniques
Malware authors employ sophisticated evasion techniques to avoid detection.
These include encrypting or obfuscating code, using polymorphic malware that changes its code upon each infection, and employing anti-debugging techniques to hinder analysis.
Resource Intensive
Malware analysis, especially manual code reversing, requires significant time and expertise. It is resource-intensive, demanding skilled analysts and advanced tools to dissect and understand complex malware.
Constantly Evolving Threats
The malware landscape is continually evolving, with new threats emerging regularly. Keeping up with these changes requires continuous learning and adaptation, making it challenging for security teams to stay ahead.
Volume of Malware
The sheer volume of malware samples that organizations must analyze can be overwhelming. Automated tools help manage this load, but distinguishing false positives from real threats remains a significant task.
Future Trends in Malware Analysis
Looking ahead, several trends are expected to shape the future of malware analysis.
AI and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are set to play a crucial role in malware analysis. These technologies can enhance the detection and analysis process by identifying patterns and anomalies that might be missed by analysts.
Advanced Sandboxing Techniques
Next-generation sandboxing techniques will improve the ability to detect and analyze sophisticated malware. These will include enhanced behavioral analysis and the ability to simulate various environments more accurately.
Integration with Threat Intelligence
Integration with threat intelligence platforms will become more seamless, providing real-time data and insights that enhance malware analysis. This will enable faster identification of threats and more effective response strategies.
Training and Resources for Malware Analysts
To keep up with the evolving malware landscape, continuous training and access to resources are essential for malware analysts.
Certifications
Certifications such as Certified Malware Analyst (CMA) and GIAC Reverse Engineering Malware (GREM) provide formal recognition of expertise in malware analysis and reverse engineering.
Online Courses
Numerous online platforms offer courses on malware analysis, including SANS Institute, Coursera, and Udemy. These courses cover various aspects of malware analysis, from basic to advanced levels.
Books and Publications
Books like “Practical Malware Analysis” by Michael Sikorski and Andrew Honig, and “The Art of Memory Forensics” by Michael Hale Ligh, Andrew Case, Jamie Levy, and Aaron Walters are valuable resources for learning.
Community and Forums
Engaging with the cybersecurity community through forums like Reddit’s r/Malware, Stack Exchange, and professional groups on LinkedIn can provide support, share knowledge, and stay updated on the latest threats and techniques.
Cloud-Based Analysis
Cloud-based malware analysis solutions will offer scalability and flexibility, allowing organizations to analyze large volumes of malware without significant infrastructure investments.
This approach will also facilitate collaboration and sharing of threat intelligence across organizations.
Staying informed about these trends will help organizations prepare for future challenges and leverage new technologies to enhance their cybersecurity defenses.
Forecast for Malware Analysis
The malware analysis market is expected to grow significantly over the next five years. Several factors drive this growth:
- Increased Cyberattacks: The rising frequency of cyber assaults creates an urgent need for effective malware analysis.
- False Positives: Existing threat detection systems often produce false positives. Malware analysis helps accurately identify and prioritize real threats.
This anticipated growth is driven by the increasing complexity of cyber threats. As cybercriminals become more sophisticated, the need for advanced malware analysis tools and techniques will grow. Organizations will invest more in these technologies to protect their systems and data.
Conclusion
Malware analysis is a vital component of any robust cybersecurity strategy. It helps identify, understand, and mitigate the impact of malicious software.
By leveraging various types of analysis and utilizing specialized tools, organizations can enhance their defenses against ever-evolving cyber threats.
I recommend staying informed about the latest trends and tools in malware analysis to effectively safeguard your systems and data.
In summary, malware analysis is essential for any organization looking to protect its digital assets. By understanding how malware works and using the right tools and techniques, you can stay ahead of cybercriminals and ensure your systems remain secure.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
- The Cyber Threat Intelligence Capability Maturity Model (CTI-CMM)
- Top 10 Dark Web Forums Dominating Cybercrime
- CVE-2024-38396: A Critical Vulnerability in iTerm2
- What is Malware Analysis?
- Why Cybercriminals Chase Your Personal Information
