Your cart is currently empty!

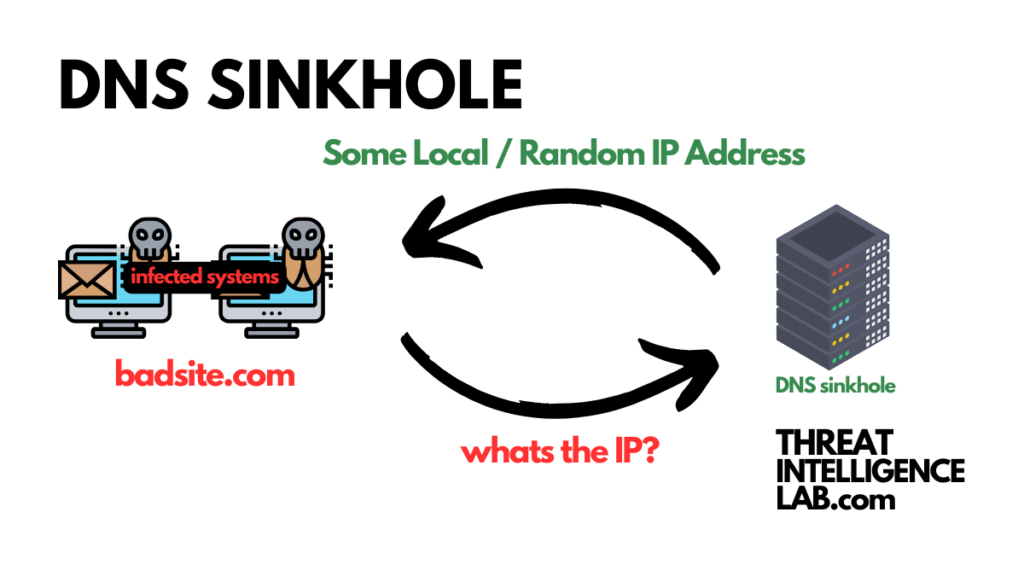
A DNS sinkhole is a defensive mechanism designed to protect users from malicious or unwanted domains. A DNS sinkhole intercepts DNS requests attempting to connect to these harmful sites and returns a controlled IP address instead.
This address leads to a sinkhole server managed by the DNS sinkhole administrator. Essentially, it acts as a filter and a trap for malicious and unwanted traffic.
Let’s understand the Domain Name Service (DNS) first. DNS acts like the internet’s phone book, translating human-readable domain names into numerical IP addresses.
For example, the Google website, www.google.com, currently translates to the IP address 142.251.36.14. This service is part of the TCP/IP protocol suite, which sets the standards for data exchange on the internet.
In a typical home setup, devices connect to the internet using the ISP’s DNS server, configured on the Customer-premises equipment (CPE).
These devices can also use the home router as a DNS server, which then forwards DNS requests to the ISP’s servers. To speed up connections, computers cache DNS responses, avoiding repeated DNS requests for future connections.
The Mechanics of DNS Sinkholing
Sinkholing can be implemented at various levels, from ISPs and Domain Registrars to system administrators within an organization.
Even individual users with administrative privileges can modify their host files to achieve similar results.
Many open-source and commercial lists of known malicious domains are available to populate a DNS sinkhole.
When a device tries to connect to a known malicious domain, such as a botnet Command & Control (C&C) server, the sinkhole redirects this request to the controlled IP address.
This redirection prevents the host from establishing a malicious connection and aids in identifying compromised machines.
The Benefits and Challenges of Sinkholing
DNS sinkholing offers two primary benefits:
- Preventing Malicious Connections: By diverting traffic away from harmful domains, it protects networks from potential threats.
- Identifying Compromised Hosts: Analysis of sinkhole logs can reveal which hosts are attempting to connect to malicious domains, indicating possible infections.
However, implementing a DNS sinkhole comes with challenges, notably the legal and privacy concerns.
Logging data through a sinkhole requires adherence to legal boundaries to avoid privacy breaches.
Therefore, sinkholing is often conducted under special conditions by trusted third parties, sometimes involving law enforcement.
6 DNS Sinkhole Functionalities
In short, a DNS sinkhole is filled with functionalities that help to combat cybercrime.
They are essential in both understanding and combating various cyber threats:
1. Traffic Redirection and Isolation
One of the primary functions of a DNS sinkhole is to redirect traffic from potentially compromised or malicious sources. By rerouting this traffic to a server controlled by cybersecurity teams, the sinkhole isolates it from the rest of the network.
This redirection not only prevents the malicious traffic from reaching its intended target but also keeps the network’s other segments secure from potential contamination.
2. Data Collection and Analysis
Once the traffic is redirected to the sinkhole server, it subsequently becomes a rich source of data for analysis. This data includes crucial details, such as the origin of the attack, the type of malware, and the behavior of the compromised systems.
Consequently, by examining this data, cybersecurity professionals can identify emerging patterns. Furthermore, this understanding of the nature of the threat enables them to devise effective strategies to counter similar attacks in the future.
3. Identification of Compromised Hosts
A DNS sinkhole helps in identifying compromised hosts within a network.
Therefore, when a host attempts to connect to a known malicious domain and is redirected to the sinkhole, it signals a potential compromise.
This functionality is crucial for early detection of infections, allowing IT teams to respond swiftly to contain and remediate the threat.
4. Disruption of Command and Control Communications
Many malware families and types, especially botnets, rely on command and control (C&C) servers to operate. DNS sinkholing disrupts this line of communication by redirecting requests meant for C&C servers to the sinkhole server. This disruption can effectively neutralize a botnet’s ability to execute coordinated attacks or exfiltrate data.
5. Compliance and Legal Considerations
DNS sinkholing must be conducted within the boundaries of legal and compliance frameworks. As such, one of its functionalities includes ensuring that any data collection and analysis adhere to privacy laws and regulations. This is especially important when handling personal or sensitive data inadvertently caught in the sinkhole.
6. Threat Intelligence Sharing
Information gathered from DNS sinkholing can be shared with other organizations and law enforcement to enhance overall threat intelligence. This collaboration is vital for developing a more comprehensive understanding of emerging cyber threats and strengthening collective defense mechanisms across different sectors.
Sinkholing operations by law enforcement
Over the years, law enforcement agencies have successfully executed several high-profile sinkholing operations against various botnets.
These operations often involve intricate planning and international collaboration.
Here are some notable instances where law enforcement successfully used sinkholing to disrupt botnet activities.
Gameover Zeus Botnet (2014)
This was a significant operation led by the FBI and international law enforcement. Gameover Zeus was a notorious botnet used for banking fraud and distributing the CryptoLocker ransomware. Law enforcement agencies managed to seize and redirect the botnet’s command and control servers, using sinkholing to capture traffic and weaken the network.
Avalanche Network (2016)
This was one of the largest botnet takedowns in history, involving law enforcement from over 30 countries.
The Avalanche network was used for various cybercrimes, including phishing and distributing malware.
The operation involved sinkholing the botnet’s domains, which allowed the authorities to redirect traffic from the infected computers to servers controlled by law enforcement, thereby dismantling the botnet’s infrastructure.
Andromeda Botnet (2017)
A collaborative effort between various international law enforcement agencies, including the FBI, Europol, and the private sector, led to the takedown of Andromeda (also known as Gamarue). This botnet was associated with a range of criminal activities, including stealing credentials. The operation involved taking control of the botnet’s servers and redirecting traffic to law enforcement-controlled servers.
Trickbot Botnet (2020)
The Trickbot botnet, known for its role in distributing ransomware and conducting cyber espionage, was targeted by a coalition of tech companies and law enforcement agencies. The operation included disabling the IP addresses associated with Trickbot’s command and control servers and redirecting traffic to servers controlled by the coalition, significantly disrupting the botnet’s operations.
Emotet Botnet (2021)
In a coordinated action by law enforcement agencies from the Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine, the infrastructure of the Emotet botnet was taken over and disrupted.
Emotet was one of the most significant malware threats at the time, known for its capabilities as a “loader” to deliver other types of malware. The operation involved seizing control of the botnet’s infrastructure and implementing a sinkhole to capture the traffic from infected machines.
Limitations of DNS Sinkholing
Deploying DNS sinkholes, comes with several constraints that can impact their effectiveness:
1. Dependency on Organizational DNS Usage
For a DNS sinkhole to effectively block malware traffic, it is essential that the malware uses the organization’s DNS server.
However, when malware comes equipped with hardcoded DNS server information or specific IP addresses, it can entirely bypasses the DNS sinkhole.
Nonetheless, this limitation can be somewhat mitigated by strategically configuring perimeter firewalls to block outbound DNS queries that are not directed at the organization’s DNS servers.
2. Inability to Prevent Malware Execution and Spread
A significant limitation of DNS sinkholing is that it does not prevent the execution or spread of malware on the network. It’s purely a means of redirecting traffic; it doesn’t remove malware from infected machines or stop it from infecting other computers within the network.
3. Dependence on Accurate Indicators of Compromise
The effectiveness of a DNS sinkhole relies heavily on the accuracy of the indicators of compromise (IoCs) used to identify malicious traffic.
Consequently, these IoCs require thorough analysis beforehand.
Additionally, malicious IP information gathered from open sources to populate the DNS sinkhole might contain false positives. As a result, this can lead to the unintended blocking of legitimate websites.
4. Need for Isolation and Secrecy
Isolate the sinkhole from external networks. This prevent sending signals to attackers that their command and control (C&C) traffic is influenced.
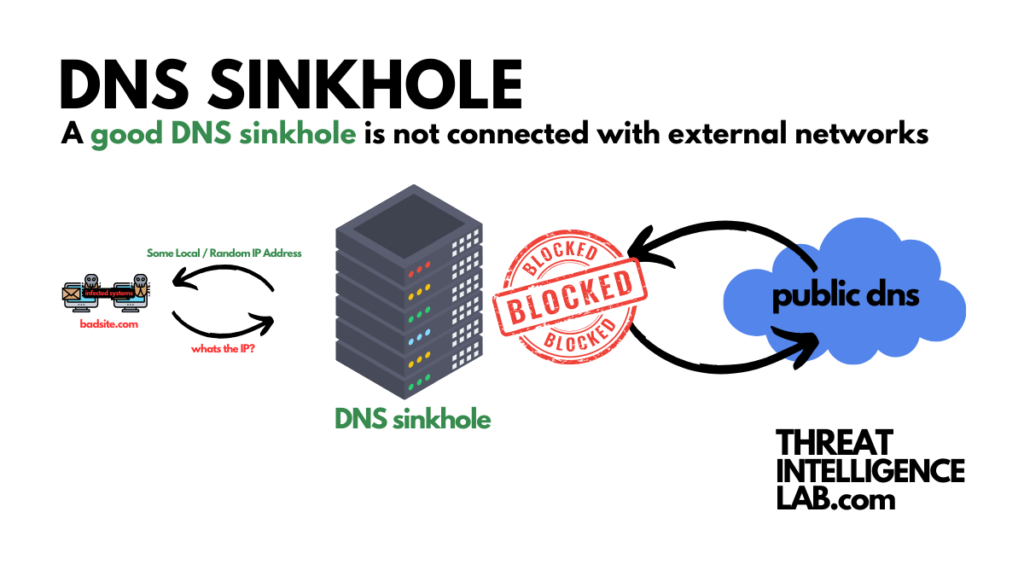
If attackers become aware of the sinkhole, they might manipulate its entries for malicious purposes, leading to a reverse effect where the sinkhole inadvertently aids the attackers.
5. Time-to-Live (TTL) Settings Management
Limit the DNS records within the sinkhole with short Time-to-Live (TTL) values. This diminishes the effectiveness of the sinkhole in responding to rapidly evolving threats.
While sinkholing is a valuable tool for redirecting malicious traffic and gathering intelligence, it must be complemented with other security measures to prevent malware execution, ensure accurate threat detection, and maintain network integrity.
