Your cart is currently empty!

Understanding Threat Intelligence Platforms (TIPs)
In the world of cyber threat intelligence, one tool stands out: the Threat Intelligence Platform (TIP). As someone with years of experience in cybersecurity and threat intelligence, I can say that TIPs are essential. But what exactly are TIPs, and why are they so crucial? Ill try to explain this.
What is a Threat Intelligence Platform (TIP)?
A Threat Intelligence Platform (TIP) is a software solution designed to gather, analyze, and understand threat data from multiple sources. TIPs help cybersecurity teams detect, understand, and stop potential threats more effectively.
They act as a central hub for collecting threat intelligence, providing actionable insights to improve an organization’s security.
- Why Data Breach Report Feeds Are Important
- The Top 10 Essential Log Sources for IT Monitoring
- Dark Web Cybercrime Forums You Should Monitor
- How to Parse and Use VirusTotal feeds
- Getting The Most Out Of URLscan.io
Why Are TIPs Essential?
Cyber threats are getting more advanced and widespread. Traditional security measures often can’t keep up. TIPs gather threat data from various sources like open-source intelligence (OSINT), commercial threat feeds, and social media.
This centralized approach ensures no potential threat is missed. TIPs use machine learning and artificial intelligence to analyze and find patterns in data, spotting anomalies that may indicate a threat. This helps organizations predict and stop threats before they cause harm.
TIPs provide detailed intelligence, helping security teams make informed decisions. By understanding the threat, organizations can implement targeted defenses.
TIPs also enable information sharing and teamwork within an organization and with external partners. This collective intelligence strengthens overall security.
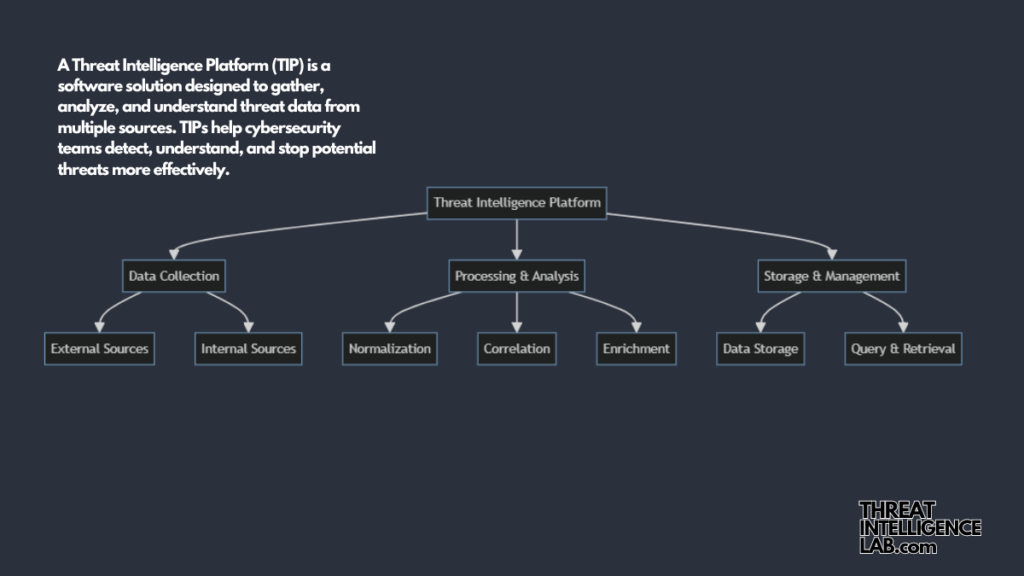
How Do TIPs Work?
TIPs follow a series of steps. First, the platform collects threat data from various sources like internal logs, external threat feeds, and dark web monitoring.
Next, TIPs clean and standardize the data, then correlate it to find relationships and patterns that could indicate a threat. The platform then adds context to the data, such as threat actor profiles, attack methods, and historical data.
This helps understand the threat landscape better. TIPs analyze the enriched data and score threats based on their potential impact and likelihood. This helps prioritize the most critical threats.
Finally, TIPs generate reports and alerts, providing security teams with the information they need to respond effectively.
TIP Ebook by ThreatConnect
- Why Threat Intelligence Matters
- What are Threat Intelligence Platforms
- TIP key points and benefits

Benefits of Using a TIP
Using a TIP offers many advantages. By continuously analyzing threat data, TIPs help organizations identify and address threats before they escalate.
With detailed threat intelligence, security teams can respond more quickly and effectively to incidents.
TIPs help prioritize threats, allowing security teams to use their resources more efficiently. Many industries have strict cybersecurity regulations. TIPs help meet these requirements by providing comprehensive threat intelligence and documentation.
7 Ways to Apply The Cyber Attack Cycle in TIPs

The Cyber Attack Cycle
- Cyber Attack Cycle: Actions Phase
- Cyber Attack Cycle: Command & Control (C2)
- Cyber Attack Cycle: Installation Phase
- Cyber Attack Cycle: Exploitation Phase
- Cyber Attack Cycle: Weaponization and Delivery
- Cyber Attack Cycle: Reconnaissance Attacks
How Analysts Can Make Use of TIPs
Threat Intelligence Platforms are powerful tools, but their effectiveness depends on how well analysts use them. Here’s how analysts can make the most out of TIPs:
Centralized Intelligence Gathering
Analysts can use TIPs to gather threat intelligence from multiple sources in one place.
This centralization saves time and ensures that all relevant data is considered. By integrating feeds from OSINT, commercial providers, and internal data, analysts can get a comprehensive view of the threat landscape.
Data Correlation and Analysis
With the data aggregated, analysts can use TIPs to correlate information from different sources.
This helps identify patterns and connections that might not be evident when looking at data in isolation. For example, correlating IP addresses from a threat feed with internal logs might reveal a previously unnoticed intrusion attempt.
Enriching Data for Context
TIPs allow analysts to enrich raw data with additional context, such as details about threat actors and their tactics, techniques, and procedures (TTPs). This enriched data helps analysts understand the threat better and predict potential future actions.
Prioritizing Threats
Not all threats are equal. TIPs help analysts prioritize threats based on factors like potential impact, likelihood, and relevance to the organization. This prioritization ensures that the most critical threats are addressed first, optimizing resource use.
Generating Actionable Insights
TIPs provide analysts with actionable insights by translating complex data into understandable and relevant information.
Analysts can use these insights to make informed decisions about how to respond to threats, whether through immediate action or longer-term strategic changes.
Facilitating Collaboration
TIPs support collaboration by allowing analysts to share insights and data with other teams and external partners. This collaborative approach can lead to a more comprehensive understanding of threats and more effective responses.
Automated Responses
Many TIPs include automation features that can take predefined actions in response to certain threats. Analysts can set up these automated responses to handle routine threats, freeing up time to focus on more complex issues.
Enhancing Your TIP with a Custom Malware Analysis Sandbox
Integrating your own malware analysis sandbox into a Threat Intelligence Platform (TIP) is a game-changer. It allows you to analyze malware samples in-depth, providing unique and actionable insights that enhance the overall threat intelligence.
Why Add a Malware Analysis Sandbox?
A custom malware analysis sandbox allows you to dissect and understand malware behavior in a controlled environment.
This deeper analysis helps you identify specific tactics, techniques, and procedures (TTPs) used by threat actors, which can then be integrated into your TIP. By analyzing malware in-house, you gain several advantages:
- Detailed Behavioral Insights: Understand how malware interacts with systems, what changes it makes, and how it communicates with its command and control (C2) servers.
- Customized Reporting: Generate reports tailored to your specific needs, highlighting the most relevant information for your organization.
- Proactive Threat Mitigation: Use the insights gained to proactively defend against similar threats, improving your overall security posture.
Benefits for Your TIP
Integrating a custom malware analysis sandbox into your TIP provides a continuous feed of high-quality threat intelligence. It enables you to:
- Enhance Detection Capabilities: Improve your ability to detect and respond to advanced threats.
- Gain Competitive Advantage: Stay ahead of threat actors by understanding and mitigating new malware variants quickly.
- Strengthen Collaboration: Share detailed analysis reports with other teams and partners, fostering a collaborative defense approach.
Conclusion
Threat Intelligence Platforms are indispensable tools in modern cybersecurity. They provide the necessary intelligence to detect, understand, and mitigate threats effectively.
As cyber threats continue to evolve, TIPs will play a crucial role in helping organizations stay one step ahead.
For anyone looking to bolster their cybersecurity defenses, I recommend exploring TIPs and understanding how they can be integrated into your existing security infrastructure. The best way to get results is by staying informed and proactive, leveraging the power of threat intelligence to protect your assets.
