The dark web is a bustling marketplace for stolen data. The types of data traded there have evolved over the years, reflecting the growing sophistication of cybercriminals.
Let’s delve into what types of data are most sought after and sold by these illicit actors, backed by recent statistics and trends from 2023 and 2024.
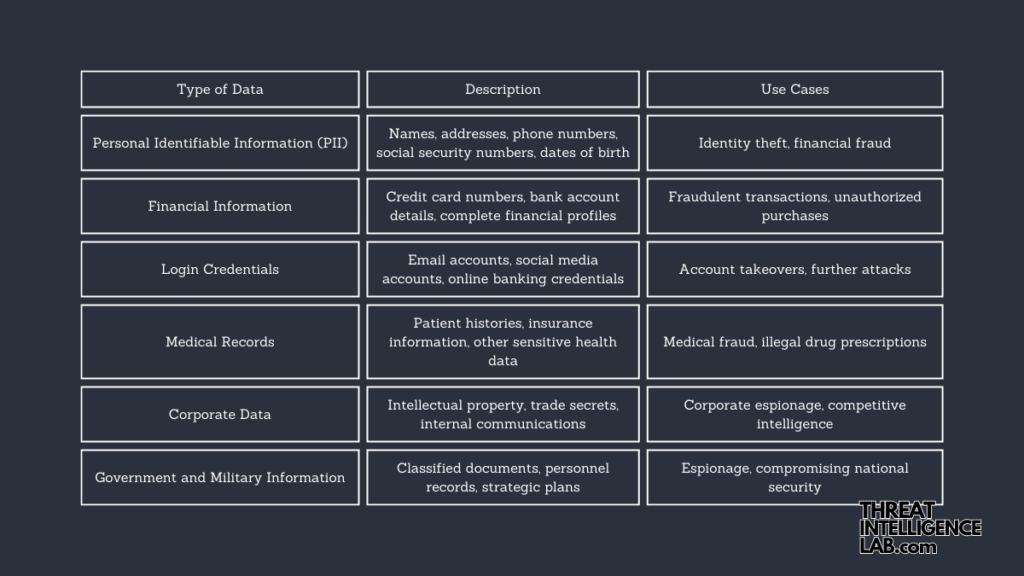
Types of Data Cybercriminals Sell
Here’s a small table summarizing the types of data cybercriminals sell on the dark web:
| Type of Data | Description | Use Cases |
|---|---|---|
| Personal Identifiable Information (PII) | Names, addresses, phone numbers, social security numbers, dates of birth | Identity theft, financial fraud |
| Financial Information | Credit card numbers, bank account details, complete financial profiles | Fraudulent transactions, unauthorized purchases |
| Login Credentials | Email accounts, social media accounts, online banking credentials | Account takeovers, further attacks |
| Medical Records | Patient histories, insurance information, other sensitive health data | Medical fraud, illegal drug prescriptions |
| Corporate Data | Intellectual property, trade secrets, internal communications | Corporate espionage, competitive intelligence |
| Government and Military Information | Classified documents, personnel records, strategic plans | Espionage, compromising national security |
Personal Identifiable Information (PII)
One of the most commonly sold types of data on the dark web is personal identifiable information (PII).
This includes names, addresses, phone numbers, social security numbers, and dates of birth. According to recent data, there has been a significant rise in the sale of PII, driven by the increasing number of data breaches affecting large databases.
Cybercriminals use this information for identity theft, financial fraud, and other malicious activities.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
Financial Information
Credit card numbers, bank account details, and other financial information remain highly valuable on the dark web. The average cost for credit card information can vary, but a complete set of financial information that includes the card number, expiration date, CVV, and associated PII can fetch a higher price.
The demand for this type of data has remained steady, with cybercriminals continually finding new ways to exploit these details for financial gain.

Login Credentials
The sale of login credentials for various online services, including email accounts, social media accounts, and online banking accounts, has surged.
These credentials are often obtained through phishing attacks, malware, or direct breaches of websites. In 2023, posts offering Redline stealer logs, a type of malware that captures login details, tripled compared to the previous year (CIO Africa).
These credentials can be used to access personal information, commit fraud, or even launch further attacks on other systems.

Medical Records
Medical records have become a prime target for cybercriminals due to their comprehensive nature and high black-market value. These records can include a patient’s full medical history, insurance information, and other sensitive details.
The healthcare sector has seen an 86% increase in attacks, highlighting the growing threat to this industry (Prey Security). These records are often used for medical fraud, creating fake insurance claims, or obtaining prescription drugs illegally.
Corporate Data
Cybercriminals are increasingly targeting and selling corporate data, including intellectual property, trade secrets, and internal communications, on the dark web. This data holds immense value for corporate espionage and competitive intelligence.
Access to corporate systems can sell for substantial amounts, ranging from $2,000 to $4,000, depending on the organization’s size and importance (The Tech Report).
Additionally, ransomware attacks locking up corporate data have become more prevalent, with attackers demanding significant ransoms for its release (Kaspersky).
Government and Military Information
Nation-state actors and other sophisticated threat groups aggressively seek out data related to government and military operations due to its high sensitivity.
- Cyber Attack Cycle: Actions Phase
- Cyber Attack Cycle: Command & Control (C2)
- Cyber Attack Cycle: Installation Phase
- Cyber Attack Cycle: Exploitation Phase
- Cyber Attack Cycle: Weaponization and Delivery
- Cyber Attack Cycle: Reconnaissance Attacks
Monitoring the Dark Web
Tracking dark web activities is crucial but highly challenging. The dark web is a haven for cybercriminals, where they trade stolen data and plan sophisticated attacks.
Staying ahead of these threats requires constant vigilance and specialized skills. The anonymity and encryption used on the dark web make it difficult for traditional monitoring tools to access and analyze data.

Specialized companies, such as cybersecurity firms and threat intelligence providers, play a vital role in this effort.
They employ advanced techniques and tools to infiltrate dark web forums, monitor transactions, and gather intelligence on emerging threats. These companies often use automated systems combined with expertise to identify and track illicit activities.
Partnering with expert cybersecurity firms is the best way to stay ahead of dark web threats and protect sensitive data from falling into the wrong hands.
Reza Rafati
These specialized services are essential for businesses that lack the resources or expertise to monitor the dark web themselves. Outsourcing dark web monitoring allows companies to focus on their core operations while ensuring they are protected against cyber threats.
Emerging Trends and Predictions
Looking ahead, several trends are expected to shape the dark web market in 2024.
These include:
- Increased Use of AI and Machine Learning: Cybercriminals are leveraging AI to automate and enhance their attacks. This includes using machine learning algorithms to identify vulnerabilities more efficiently and execute sophisticated attacks.
- Crypto-Drainer Services: With the growing interest in cryptocurrencies, there has been a rise in services designed to drain crypto wallets. These services are expected to become more prevalent as more people invest in digital assets (Kaspersky).
- Enhanced Malware Services: The dark web market for malware is evolving, with an increase in services that provide advanced evasion techniques and loader malware. These services make it easier for cybercriminals to deploy malware without detection (CIO Africa).
Therefore, In conclusion, the dark web continues to be a dynamic and evolving marketplace for stolen data. As cybercriminals refine their tactics and expand their reach, staying informed and vigilant is essential.
I recommend regular monitoring of dark web activities and adopting robust cybersecurity measures to protect sensitive information. The best way to stay ahead of these threats is to understand the ever-changing landscape and prepare accordingly.

