Your cart is currently empty!

Top Malware Analysis Platforms & Tools (2024)
From an email attachment masquerading as benign to an application downloaded off the internet or even a snippet of malicious code on a legitimate website, the avenues through which malware can infiltrate our digital lives are vast and varied.
In response, the cybersecurity community has stepped up, developing a variety of malware analysis tools designed to combat the surge of cyber threats effectively.

These tools are crucial for security analysts, enabling them to dissect malware samples, understand their functionalities, and aid in investigative efforts.
In this article, I’ll guide you through a selection of premier, yet entirely free, malware analysis tools and platforms. These resources are indispensable for bolstering your cybersecurity defenses without incurring additional costs.
Top Malware Analysis Platforms & Tools
VirusTotal
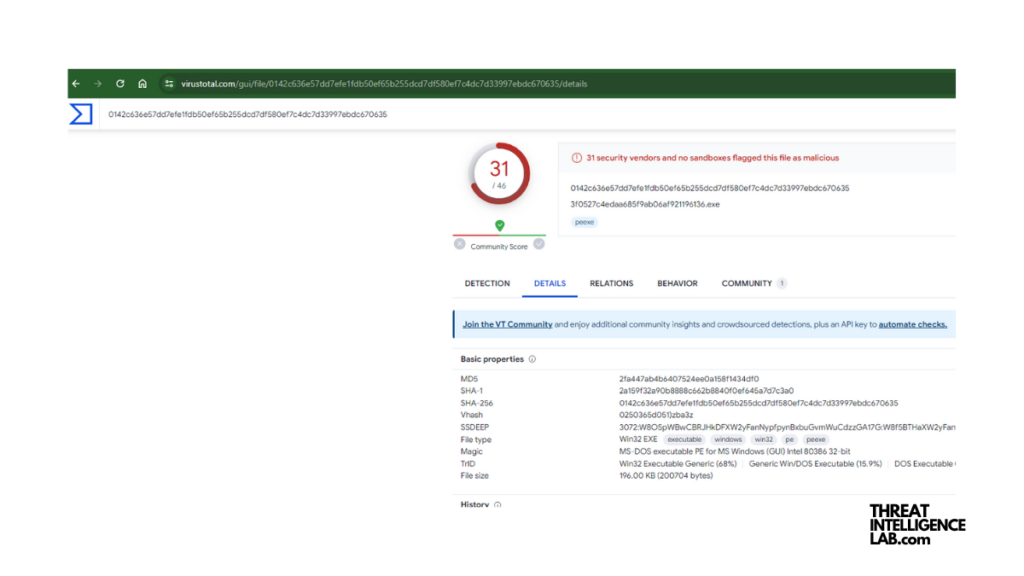
VirusTotal is a highly respected malware analysis platform that stands out for its ability to scan suspicious files or URLs using over 70 antivirus scanners and URL/domain blocklisting services.
It compiles these results to deliver a thorough report on the file’s reputation, complete with behavior analysis and sandbox execution features.
- Pros: VirusTotal offers extensive antivirus engine coverage, scans for suspicious domains, and provides detailed reports through an easy-to-use interface.
- Cons: Be aware that files uploaded to VirusTotal become publicly accessible, and there’s a 32 MB upload limit, though larger files can be accommodated through a special upload URL.
DOCGuard
DOCGuard introduces a novel approach to malware analysis through structural analysis. This technique disassembles malware relative to its file structure components, allowing for rapid detection and the extraction of indicators of compromise (IoCs) free from false positives.
- Pros: DOCGuard is recognized for its speed, user-friendly interface, and detailed reporting capabilities. It’s free for use in the cloud and offers a “Real World Example” service.
- Cons: While cloud use is free, accessing DOCGuard through its API requires a license.
Hybrid Analysis

Hybrid Analysis employs both static and dynamic analysis methods, offering a comprehensive view of malware. Users can submit files and URLs for analysis, which are then executed in a controlled environment to monitor their behavior.
- Pros: Offers in-depth behavioral analysis and supports a range of environments, including Windows, Linux, and Android.
- Cons: Public report availability is limited, and free users may face usage restrictions.
Cuckoo Sandbox
Cuckoo Sandbox is an open-source solution that specializes in behavioral analysis. It observes the behavior of submitted files in an isolated environment, generating detailed reports on network activities and system changes.
- Pros: Features extensive customization options, robust behavioral analysis capabilities, and strong community support.
- Cons: Setup requires technical knowledge, and compatibility issues with certain file formats may arise.
Any.Run
Any.Run stands out as an interactive malware analysis platform that allows real-time observation of malware behavior in a sandbox environment through a web browser.
- Pros: Facilitates real-time behavior analysis and interactive sandboxing, with features designed to foster collaboration.
- Cons: Paid subscriptions offer advanced features, restricting free users’ access.
Joe Sandbox
Joe Sandbox caters to both static and dynamic analysis needs, offering detailed insights into malware’s behavioral activities, network connections, and system changes.
- Pros: Comprehensive feature set, extensive analysis capabilities, and customizable configurations.
- Cons: Free users face monthly submission limits, and registration requires a business email.
Viper 2 Framework
The Viper 2 Framework serves as a binary analysis and management tool, allowing users to upload and analyze files and create exportable analysis profiles.
- Pros: Open-source, supports multiple analysis techniques, and encourages collaboration.
- Cons: Primarily functions as a collection organizer, relying on external sources for analysis.
Tria.ge
Triage Sandbox, developed by Hatching, is an advanced solution that supports automated malware analysis across various platforms.
- Pros: Offers static analysis and a user-friendly sandbox environment for a wide range of platforms.
- Cons: Currently lacks support for Windows 11, and reports are public unless an enterprise membership is purchased.
FileScan.IO
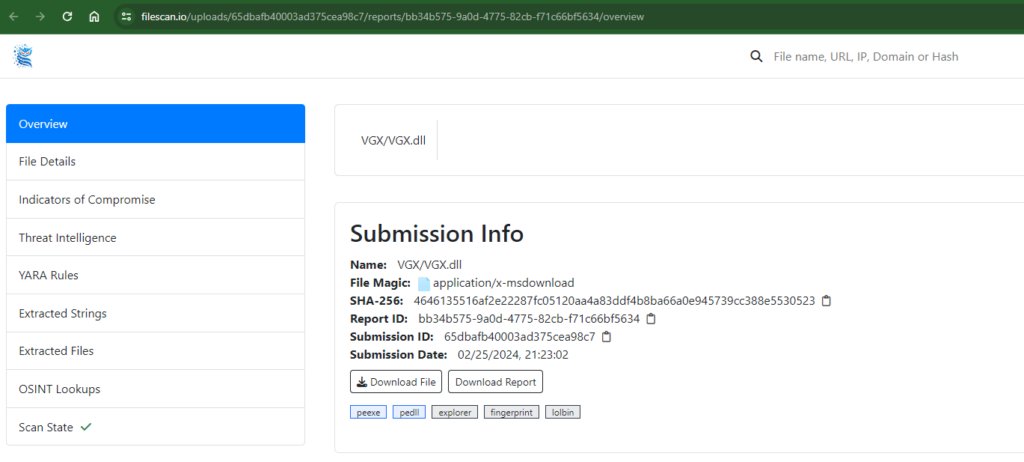
FileScan.IO distinguishes itself with adaptive threat analysis technology for zero-day malware detection and comprehensive IoC extraction, all at no cost to the user.
- Pros: Enables secure private file uploads with encryption options and excels in IoC extraction.
- Cons: Some users report inaccuracies in the analysis results.
Cape Sandbox
CAPE Sandbox, derived from Cuckoo, excels in detecting evasive malware by implementing dynamic countermeasures and Yara signatures.
- Pros: Open-source, provides effective detection of evasive malware, and is community-accessible.
- Cons: Performance can be slow, and activation requires engagement on social media platforms.
Additional Tools for Malware Analysis
- Ghidra: An NSA-developed open-source software reverse engineering framework that supports a wide range of file formats.
- x64dbg: A debugger for Windows offering a user-friendly interface and powerful scripting capabilities.
- IDA Pro: A venerable disassembler and debugger known for its comprehensive architecture analysis.
- CyberChef: Created by GCHQ. This tool helps to analyse malware and more.
Why do We Use These Tools?
The use of malware analysis tools is not just a matter of preference but a necessity.
The primary reason for leveraging these tools is to conduct swift and comprehensive analyses of malware samples. This capability is critical for several reasons:
- Quick Identification and Response: These tools enable security teams to rapidly analyze suspicious files and URLs, identifying malware strains and their functionalities.
- Understanding Anti-Detection Techniques: Analysis tools help unravel these tactics, including polymorphism, encryption, and exploitation of zero-day vulnerabilities.
- Enhancing Cyber Threat Intelligence (CTI) and Incident Response (IR) Capabilities: Malware analysis tools enrich CTI efforts by providing detailed insights into the tactics, techniques, and procedures (TTPs) of threat actors. This intelligence is vital for defending against attacks.
- Comprehensive Behavioral Analysis: Beyond merely identifying malware, these tools offer in-depth behavioral analysis. This includes monitoring how the malware interacts with system processes, its network communication patterns, and any modifications it makes to the system.
- Supporting Forensic Investigations: In the aftermath of a security incident, forensic analysis is crucial for understanding how the breach occurred and for preventing future incidents.
- Enhancing Security Awareness and Education: Finally, these tools serve an educational purpose. By dissecting malware, security professionals and researchers gain a deeper understanding of malicious software’s inner workings.
To finalize
The strategic use of malware analysis tools significantly bolsters an organization’s cybersecurity posture.
By enabling quick and detailed analysis of malware, understanding its anti-detection capabilities, and enhancing CTI and IR capabilities, these tools are indispensable for maintaining the integrity and security of digital assets in a landscape where threats are constantly evolving.
