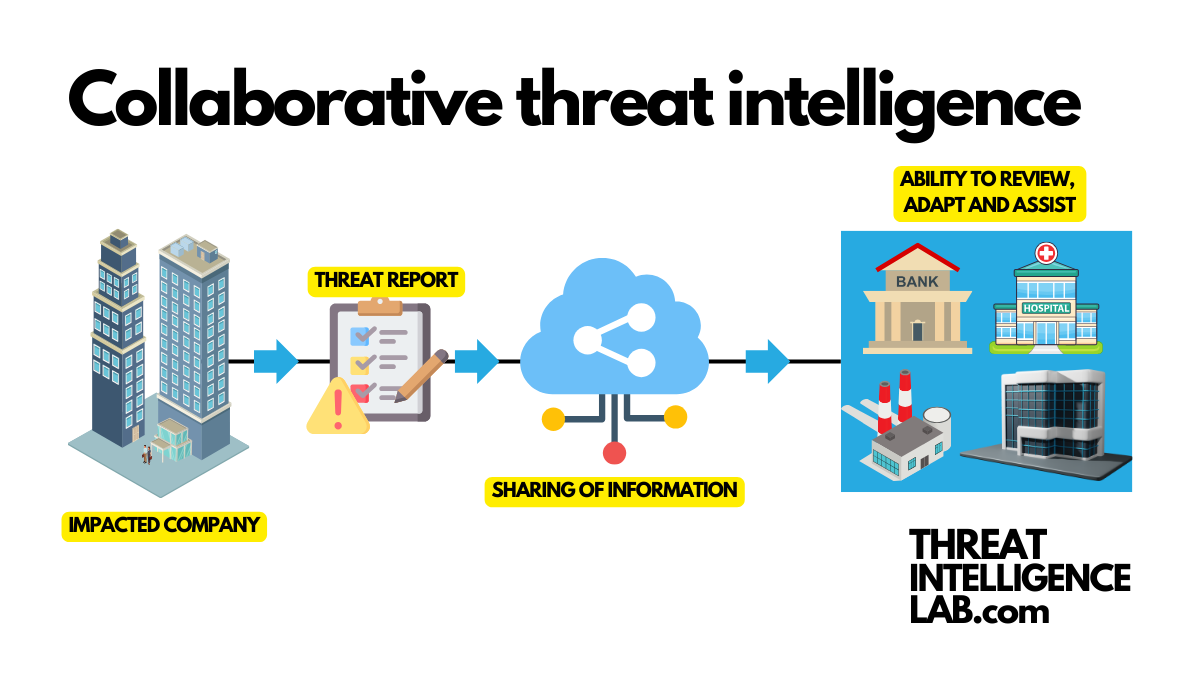
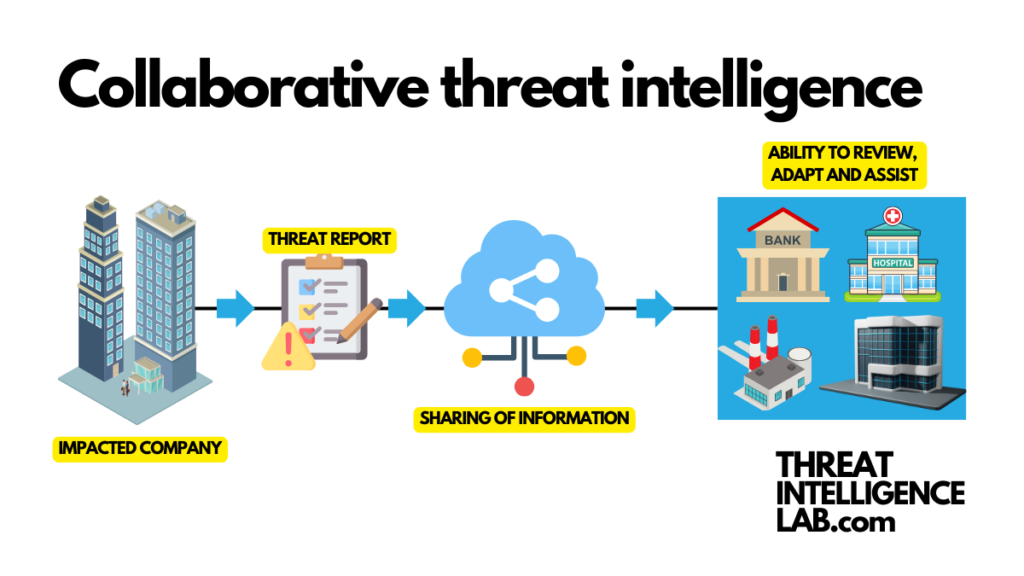
Collaborative threat intelligence – this term encapsulates a revolutionary approach in the dynamic and challenging world of cybersecurity.
Working in cybersecurity is like playing a never-ending game of ‘whack a mole’. As cybersecurity professionals, we constantly face a barrage of cyber threats, each one more cunning and elusive than the last.
In this high-stakes environment, relying solely on our own resources and insights can feel like a Sisyphean task.
Establishing a dedicated Threat Intelligence function is not just costly but complex.
And here lies a pivotal realization: focusing only within the confines of our own sectors limits our perspective, depriving us of critical insights from diverse industries that are essential to the security of our national infrastructure and economy.
Broadening the Horizon Beyond Individual Sectors
Cybersecurity teams, regardless of their resources, often face limitations in what they can achieve single-handedly.
Such as:
- Rapidly evolving malware and ransomware tactics.
- Identifying and mitigating insider threats.
- Keeping up with the increasing sophistication of phishing attacks.
This reality underscores the importance of Cyber Threat Intelligence (CTI) – a capability that empowers teams to understand and defend against cyber adversaries more effectively and economically.
Financial services organizations, for instance, invest heavily in both technical and human intelligence resources to proactively understand threats.
This level of investment is not feasible for all, particularly smaller companies, who rely on generic security controls based on frameworks like The Essential 8, NIST, or ISO 27001.
- The Essential 8: This is a set of strategies developed by the Australian Cyber Security Centre to help organizations mitigate cyber security incidents.
- NIST Framework: The National Institute of Standards and Technology (NIST) framework provides a comprehensive set of guidelines for managing cybersecurity risks
- ISO 27001: This is an international standard for managing information security. It offers a systematic approach to managing sensitive company information.
Learning from Each Other
Some large companies are already engaging in this practice. When incidents like those involving Medibank or Optus occur, their threat intelligence teams spring into action, gathering and analyzing information to bolster their defenses.
This approach of sharing and analyzing intelligence across all sectors is vital in making a cyber-secure nation.
It eliminates silos, reduces duplicated efforts, and allows for a unified defense strategy.
Benefits of Collaborative threat intelligence in Cybersecurity
The real value of threat intelligence lies in generating timely, relevant, and actionable insights from analyzed data.
This process often requires technical specialists to transform raw information into something that can be actioned.
Here’s where the power of collaboration becomes evident.
By sharing intelligence and insights, cybersecurity teams can gain a comprehensive understanding of the evolving threat landscape without duplicating efforts.
Benefits
Embrace a Cooperative Model in Cybersecurity
Cybercriminals have become increasingly sophisticated, forming specialized teams for different stages of an attack – from initial access to data exfiltration.
To counter this, defenders need to adopt a similar level of specialization and cooperation. Collaborative threat intelligence is key to focusing resources effectively.
It enables teams to gain actionable insights, assess threats specific to their environments, and implement stronger security measures.

This cooperative approach in cybersecurity isn’t just about saving time and resources; it’s about creating a more resilient and robust defense against the ever-evolving threat landscape.