Your cart is currently empty!
The MongoDB Ransomware Experiment
Imagine setting up a honeypot, a decoy system, to mimic a vulnerable MongoDB database, just to see what might happen. That’s exactly what we did.
Within an hour, our honeypot was not only discovered but also compromised, with all its data encrypted and replaced by a ransom note.
Our MongoDB Honeypot Experiment
Our honeypot was designed to attract attention from potential attackers, simulating a poorly secured MongoDB instance.
It was an intentional setup with no real data at risk. Yet, the swift and effective ransomware deployment on this decoy system served as a strong reminder of the threats lurking in the digital shadows.
The attackers didn’t know it was a honeypot; all they saw was an opportunity.
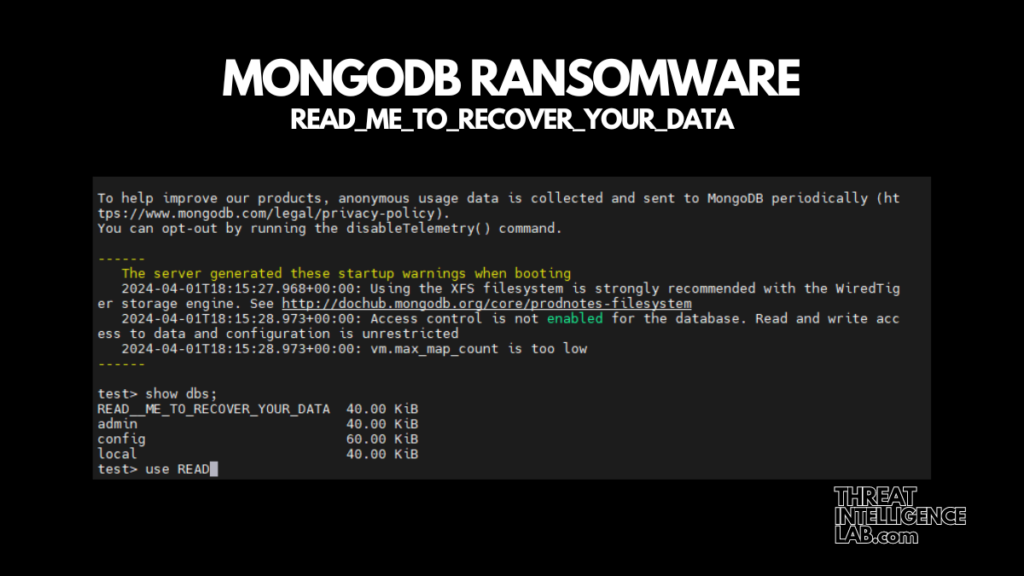
When we launched our MongoDB honeypot to the internet, it was a matter of time before attackers took the bait.
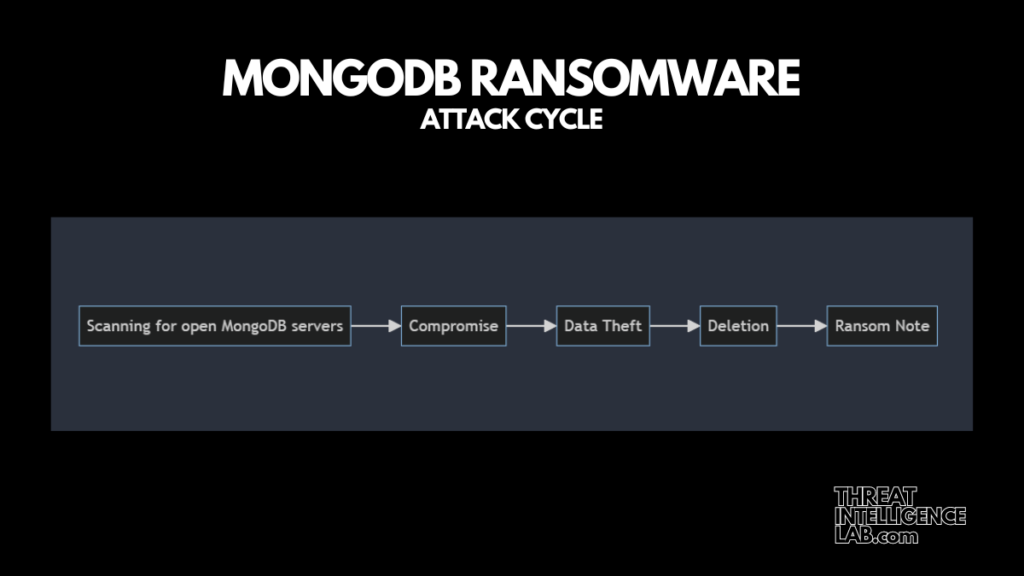
Here’s the sequence of events in brief:
- Going Online: We set up the honeypot with intentional vulnerabilities and went live, exposing it to the internet.
- Scanning: Almost immediately, it was scanned by attackers searching for such vulnerabilities.
- Compromise: The attackers quickly exploited default credentials to gain unauthorized access.
- Data Theft: They proceeded to steal our deliberately fake “sensitive” data.
- Deletion: After stealing the data, they deleted it from our database.
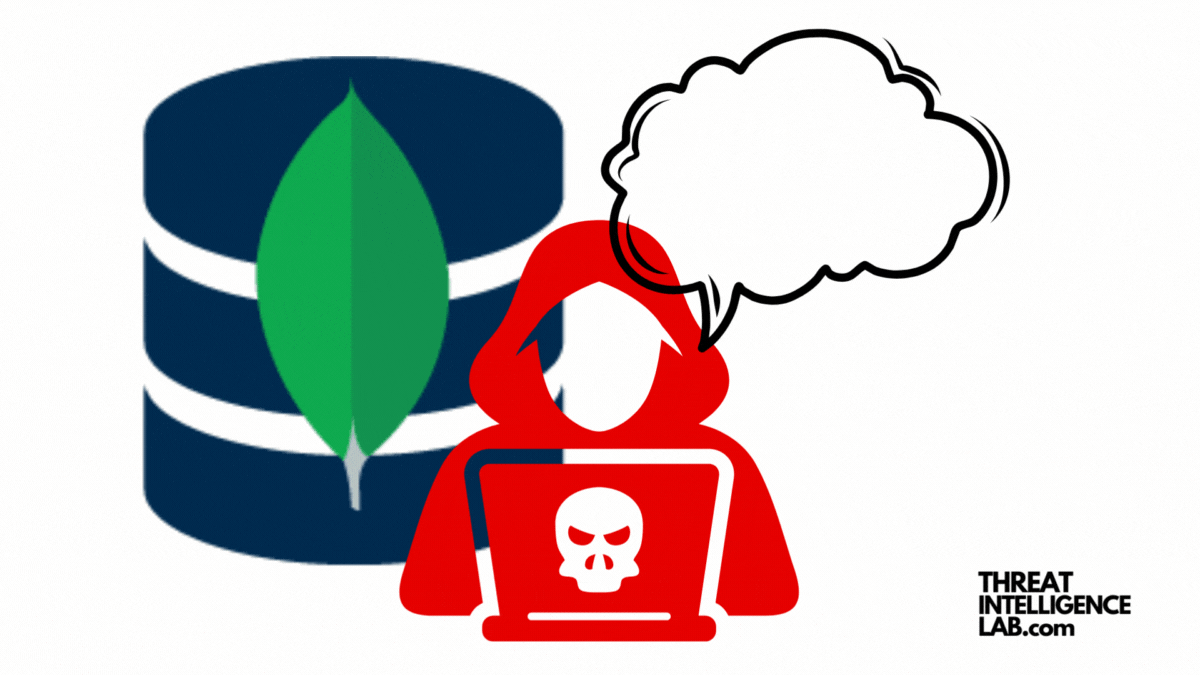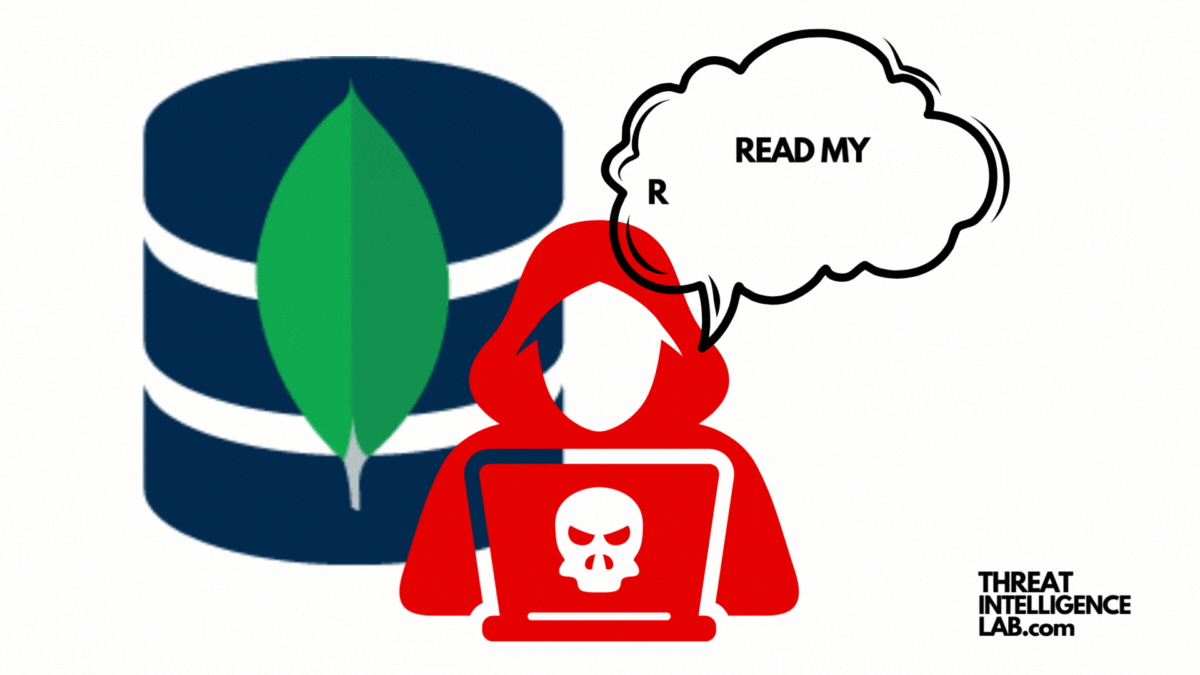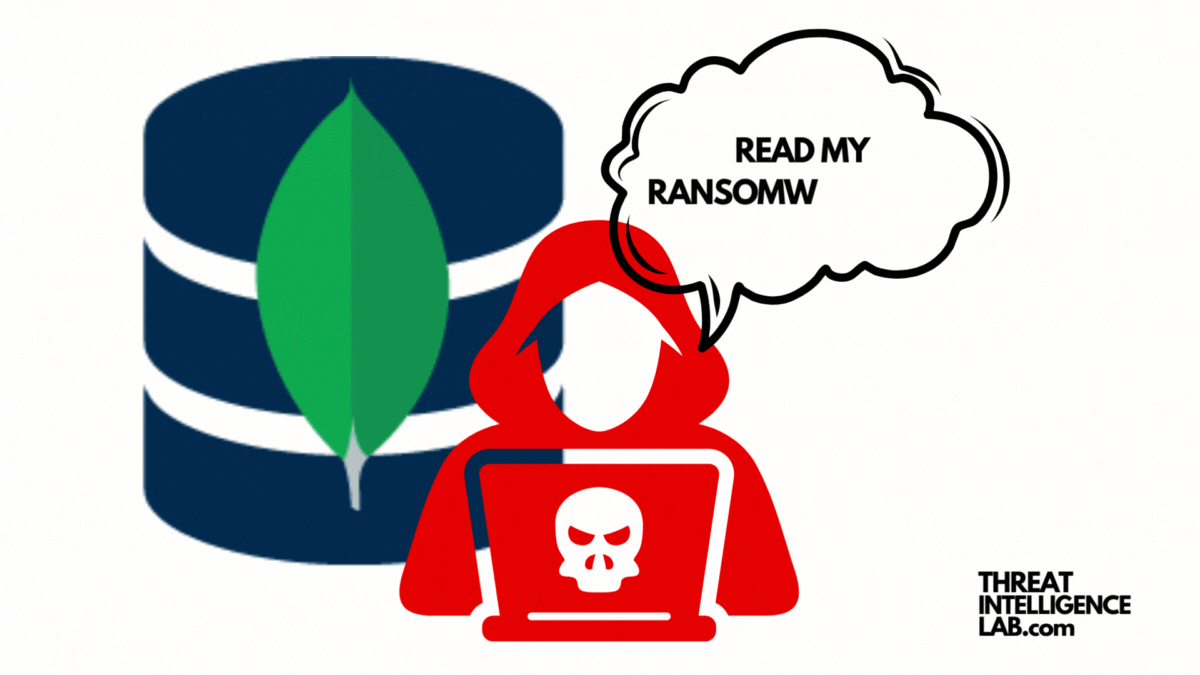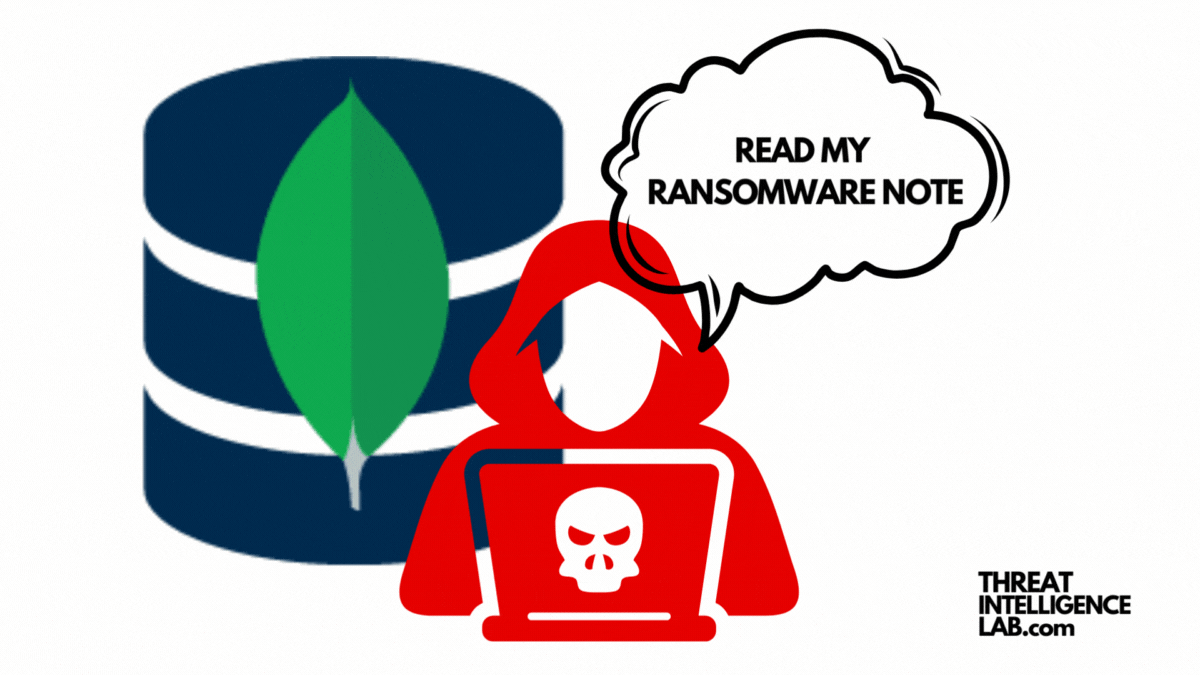
- Ransom Note: Finally, they left a ransom note within the database. This note included payment instructions, claiming that fulfilling their demands would restore the stolen and deleted data.
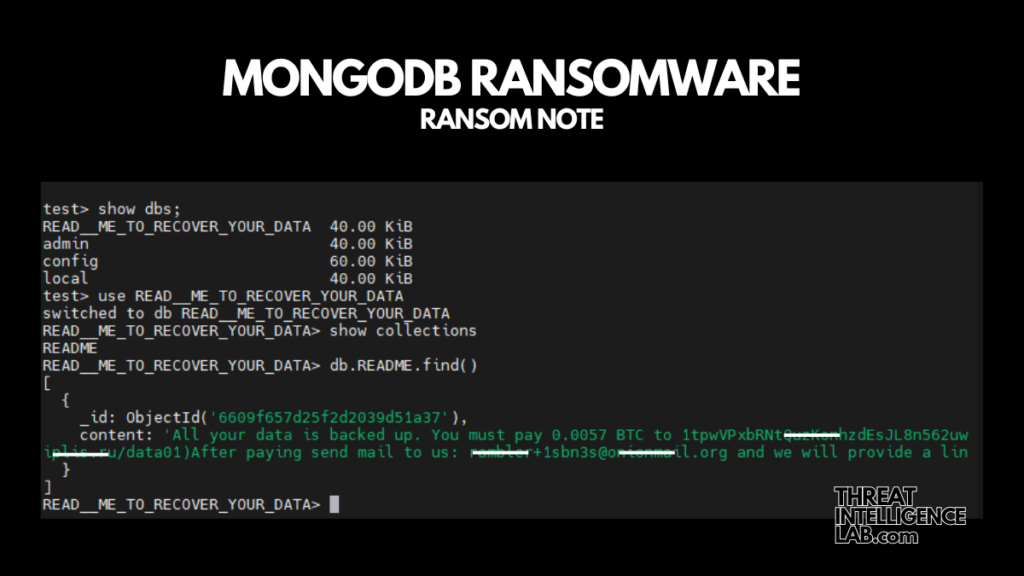
The ransomware note reads:
All your data is backed up. You must pay 0.0057 BTC to [REDACTED] In 48 hours, your data will be publicly disclosed and deleted. (more information: go to http://[REDACTED].ru/data01)After paying send mail to us: [REDACTED]@onionmail.org and we will provide a link for you to download your data. Your DBCODE is: [REDACTED]'
If It Had Been Your Database…
Now, imagine this wasn’t a controlled experiment. If a similar vulnerability existed in your MongoDB database, the impact could be huge.
Data loss, operational disruption, financial demands, and reputational damage are just the tip of the iceberg. It’s a scenario no organization wants to face, yet many inadvertently do, simply due to oversight or underestimation of the risks.
How Threat Actors find their victims
Threat actors use tools like Shodan, Mass Scan, Nmap, and other advanced scanners to find their next victims. Originally for network security testing, attackers now use these tools to spot vulnerable servers.
They scan the internet quickly, looking for open ports, outdated software, or wrong database settings.
Here’s a startling fact: A vulnerable server can go online and face a high risk of attack within seconds. The compromise process is lightning fast.
- BianLian Ransomware Group: A Rising Threat in Cybercrime
- The Black Basta Cyber Threat
- Rhysida Ransomware Group
- The Akira Ransomware Gang
- Cl0p Ransomware Gang: The Unseen Cyber Menace
Proactive Measures to Safeguard Your MongoDB
Learning from our experiment, here are crucial steps to fortify your MongoDB against such ransomware attacks:
1. Tighten Access Controls
Implement strong authentication mechanisms. Ensure that your database requires secure, complex passwords, and employ role-based access control to minimize the potential impact an attacker could have if they do gain access.
2. Stay Updated
Regularly update your MongoDB instance. Attackers often exploit known vulnerabilities that have already been patched in newer versions of software. Staying current with updates is a key line of defense.
3. Encrypt and Backup
Encrypt your sensitive data to add an extra layer of security. More importantly, maintain regular, secure backups. In the event of an attack, having recent backups is your best bet for a swift recovery without giving in to ransom demands.
4. Monitor and Respond
Implement monitoring tools to detect unusual activities indicative of an attack. The sooner you can identify a breach, the quicker you can respond and mitigate its impact. Cyber Threat Intelligence can help with this.
5. Network Security
Utilize firewalls and network security measures to restrict incoming and outgoing traffic to your databases. Consider network segmentation to further isolate and protect sensitive data.
6. Educate Your Team
Ensure that everyone involved understands the importance of security practices. Human error is often the weakest link in cybersecurity. Regular training can significantly reduce this risk.
A lesson
Approach this experiment as a valuable lesson rather than just a narrative.
Use it as an opportunity to assess your current security measures rigorously, identifying any potential vulnerabilities and weaknesses. Take proactive and decisive actions to fortify your organization’s defenses against potential threats.

Leave a Reply
You must be logged in to post a comment.