In my experience working in threat intelligence, I’ve come to understand the critical distinctions between cybersecurity and cyber intelligence.
These two fields, though often intertwined, address different aspects of information security. Let’s break down the differences.
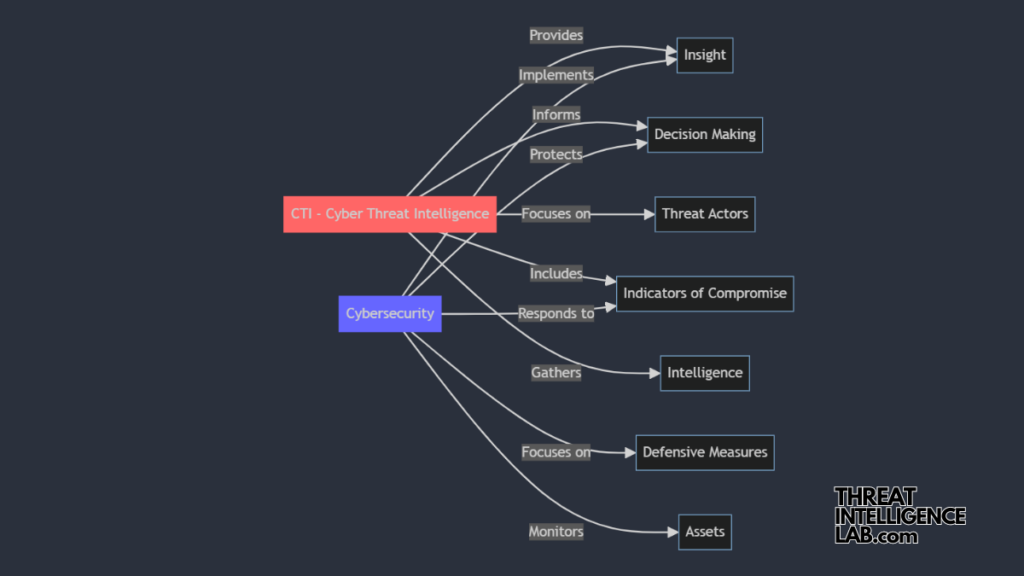
The Realm of Cybersecurity
Cybersecurity focuses on the protection of IT infrastructure, networks, and data from cyber threats and attacks. It involves the deployment of security measures like firewalls, antivirus software, and intrusion detection systems to guard against unauthorized access, data breaches, and other malicious activities.
Essentially, cybersecurity is your digital fortress—it defends your systems and data from external attacks.
Diving into Cyber Intelligence
On the other hand, cyber intelligence involves gathering, analyzing, and disseminating information about potential and current threats. This field is proactive rather than reactive.
By monitoring and evaluating the tactics, techniques, and procedures of adversaries, cyber intelligence professionals can anticipate threats before they manifest. This predictive capability is invaluable; it informs security strategies and helps prevent attacks before they can cause harm.
The synergy between Cybersecurity and CTI
In my role, I often emphasize the symbiotic relationship between cybersecurity and cyber intelligence.
While cybersecurity provides the tools and protocols to defend against attacks, cyber intelligence offers the insights needed to predict and prepare for them.
Together, they form a comprehensive security strategy that not only reacts to incidents but also anticipates and mitigates potential threats.
| Topic | Cybersecurity | Cyber Threat Intelligence (CTI) |
|---|---|---|
| Threat Detection | Utilizes threat intelligence feeds to enhance detection capabilities and identify potential threats. | Provides threat intelligence data and analysis to improve threat detection and identify emerging threats. |
| Incident Response | Responds to security incidents, containing and mitigating threats as they occur. | Provides actionable intelligence on threats, aiding in incident response and recovery efforts. |
| Vulnerability Management | Identifies and patches vulnerabilities in systems and applications to reduce the risk of exploitation. | Supplies information on vulnerabilities and exploits to prioritize patching and mitigate risks. |
| Threat Intelligence Sharing | Shares threat intelligence with other teams and organizations to improve overall security posture. | Collaborates with other teams to share threat intelligence, enhancing overall cybersecurity awareness. |
| Proactive Defense | Implements proactive defense measures such as intrusion prevention systems, honeypots, and deception technology. | Provides insights into emerging threats and attacker techniques, allowing for proactive defense measures implementation. |
Enhancing Cybersecurity with Cyber Intelligence
Cyber Intelligence (CTI) is not merely about information gathering; it’s about transforming information into actionable guidance. CTI can enhance cybersecurity efforts by offering detailed insights into potential threats and suggesting specific countermeasures.
For instance, if CTI identifies a new malware variant used by cybercriminals, this information can be used to update antivirus signatures and firewall rules before the malware reaches the organization’s network.
This preemptive action transforms cybersecurity from a traditionally reactive stance to a proactive shield.
Reza Rafati
Skill Sets for Cybersecurity vs. Cyber Intelligence Professionals
The skill sets required in cybersecurity and cyber intelligence are distinct yet complementary.
Cybersecurity professionals are often involved in the direct implementation of defensive technologies. They must understand complex technical details and be proficient in various security tools to protect organizational assets.
Conversely, cyber intelligence professionals require a blend of technical acumen and analytical prowess. They analyze trends and tactics in the cyber threat landscape and must understand the motives and methods of cyber adversaries.
These professionals often use sophisticated software tools to parse large datasets and extract meaningful patterns. For example, using machine learning algorithms, CTI professionals can predict the likelihood of certain types of cyber attacks.
| Skill Sets | Cybersecurity | Cyber Intelligence |
|---|---|---|
| Technical Knowledge | Strong understanding of network security, encryption protocols, firewalls, and endpoint security solutions. | In-depth knowledge of threat actors, malware analysis, intrusion detection, and incident response techniques. |
| Analytical Skills | Ability to analyze security breaches and vulnerabilities, and implement defensive measures to protect systems. | Proficient in analyzing data from various sources to identify potential threats and inform decision-making. |
| Threat Intelligence | Awareness of threat intelligence platforms and feeds, and integration with security tools for proactive defense. | Expertise in gathering, analyzing, and interpreting threat intelligence to identify emerging threats. |
| Incident Response | Proficient in incident response procedures and handling security incidents, including containment and recovery. | Ability to lead or participate in incident response teams, coordinating efforts to mitigate cyber threats. |
| Communication | Strong communication skills for effectively communicating security risks, threats, and mitigation strategies to stakeholders. | Ability to convey complex technical information to non-technical audiences, and collaborate with other departments. |
Tools and Technologies in Cybersecurity and Cyber Intelligence
The technological backbone of both cybersecurity and cyber intelligence is robust and ever-evolving.
In cybersecurity, tools such as advanced endpoint protection (EPP), network traffic analysis, and secure access service edge (SASE) are critical for protecting digital assets.

These technologies help detect, prevent, and respond to attacks in real-time.
In cyber intelligence, tools like threat intelligence platforms (TIPs) aggregate and correlate data from multiple sources to provide a more comprehensive threat landscape.
Additionally, automated threat hunting tools help identify potential threats before they manifest into attacks. The integration of artificial intelligence in these tools allows for the rapid processing of vast amounts of data, providing insights that were previously unattainable.
Challenges and Limitations
Despite the best efforts, both cybersecurity and CTI face several challenges. One major challenge is the pace at which new threats emerge and evolve.
Cybersecurity measures can quickly become outdated, and cyber intelligence can sometimes struggle to keep up with the speed of new threat development.
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
- The Cyber Threat Intelligence Capability Maturity Model (CTI-CMM)
Furthermore, ethical and privacy concerns are significant when it comes to cyber intelligence activities. The collection and analysis of data must be conducted in a manner that respects privacy laws and ethical standards. This balance is critical to maintaining trust and legality in intelligence operations.
Future Trends
Looking ahead, the integration of artificial intelligence and machine learning in cybersecurity and cyber intelligence is poised to redefine these fields.
AI can automate the detection of anomalies and potential threats, allowing human analysts to focus on higher-level strategy and response planning.
As cyber threats become more sophisticated, the synergy between AI-enhanced CTI and cybersecurity will be critical for developing more resilient digital defenses.
- BianLian Ransomware Group: A Rising Threat in Cybercrime
- The Black Basta Cyber Threat
- Rhysida Ransomware Group
- The Akira Ransomware Gang
- Cl0p Ransomware Gang: The Unseen Cyber Menace
In conclusion, while cybersecurity and cyber intelligence are distinct fields, their integration is essential for a holistic security strategy.
By combining the protective capabilities of cybersecurity with the predictive insights of cyber intelligence, organizations can achieve a more proactive and robust defense posture against the ever-evolving landscape of cyber threats.

Leave a Reply
You must be logged in to post a comment.