Your cart is currently empty!

Steps to Mitigate The Coathanger Malware
In my journey through cybersecurity and threat intelligence, I’ve encountered an array of challenges and evolutions in the threat landscape.
The recent discovery1 by the Dutch Military Intelligence and Security Service (MIVD) and the General Intelligence and Security Service (AIVD) of new malware targeting FortiGate devices is a prime example. I think you would agree.
It underscores a troubling trend: the growing interest of cyber adversaries in publicly accessible edge devices.
This particular incident not only showcases the sophisticated nature of modern cyber threats but also the critical need to bolster the security of edge devices2, which often act as the first line of defense for our networks.
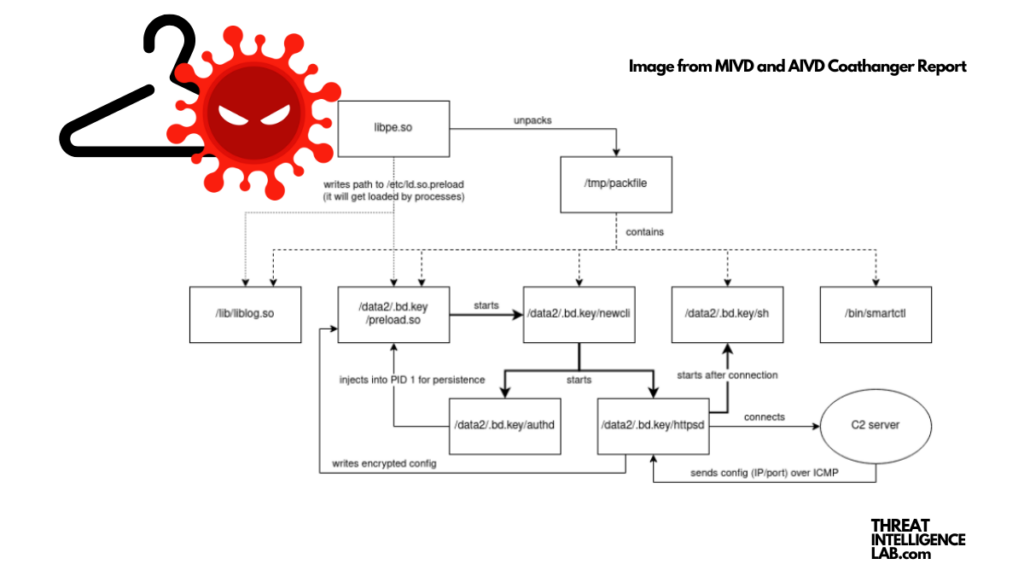
The Coathanger malware
The investigation by MIVD and AIVD unveiled a new Remote Access Trojan (RAT) malware dubbed Coathanger. It’s specifically engineered for FortiGate appliances. This RAT represents a targeted, enduring threat that stealthily bypasses security measures.
Its goal is not just to infiltrate but to persist, exploiting the CVE-2022-42475 vulnerability in FortiGate devices.
The Dutch National Cyber Security Centre (NCSC) flagged this vulnerability as high-risk in December 2022, signaling its potential for significant harm.
The Shift Towards Edge Devices
This incident is part of a wider trend where cyber attackers are increasingly exploiting vulnerabilities in publicly accessible edge devices3. These include firewalls, VPN servers, and email servers.
Edge devices are appealing targets because they sit at the network’s perimeter, often directly connected to the internet, and are typically outside the protection of Endpoint Detection and Response (EDR) solutions.
This leaves malicious or unusual behavior on these devices harder to spot.
The cybersecurity landscape has undergone a significant transformation, moving from widespread, indiscriminate attack campaigns to more precise, targeted attacks on specific infrastructure components.
Recent emphasis on exploiting vulnerabilities in Fortigate VPN, Pulse Secure, and Ivanti Connect Secure further evidences this shift.
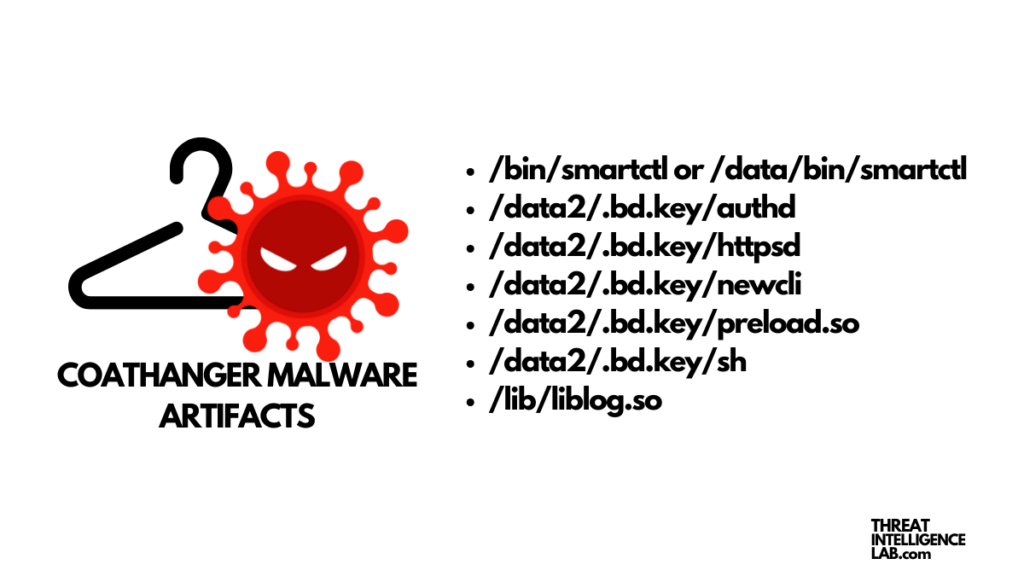
Must have information (IOC)
I took a dive into the MIVD and AIVD report on the Coathanger malware, and I noted down the most important information here for you. Use it wisely and protect your assets.
Steps to Mitigate Risks
Should you suspect a COATHANGER malware infection, consider the following possibilities:
- The threat may have extended to other hosts accessible through the compromised FortiGate appliance and possibly to devices beyond those.
- Expect a higher chance of targeted, direct intervention by attackers, indicating that the attack is not just opportunistic but involves longer-term engagement.
To address this, we advise:
- Immediately isolate any FortiGate devices you suspect are affected.
- Gather and scrutinize logs, data, and artifacts from those devices. Create a forensic image for an in-depth attack analysis.
- Think about reaching out to a third-party incident response expert. Their follow-up can help ensure the complete removal of the threat from your network and prevent re-entry by the same actors.
- Notify the incident to your National Cyber Security Centre (NCSC). In the Netherlands this would be NCSC.nl.
Insights from Experience
Two key lessons have emerged from my experiences:
- First, complete network visibility, especially regarding edge devices, is crucial. Without it, identifying and responding to threats is almost impossible.
- Second, incorporating threat intelligence into your security strategy is invaluable. Knowing the tactics, techniques, and procedures (TTPs) adversaries use can lead to better defense mechanisms.
To wrap up, the discovery of malware targeting FortiGate devices by MIVD and AIVD highlights the ongoing interest of cyber adversaries in edge devices.
Download the Coathanger Report
Stay in the loop with everything you need to know.
Still here? Continue reading:
