Your cart is currently empty!

Software Supply Chain Attacks: Insights and Defense Strategies
I often encounter questions about software supply chain attacks. These attacks can devastate organizations, especially as our reliance on third-party software components grows.
Knowing how to identify and mitigate these threats is critical. Let’s explore what software supply chain attacks are, their impact, and effective defense strategies.
What Are Software Supply Chain Attacks?
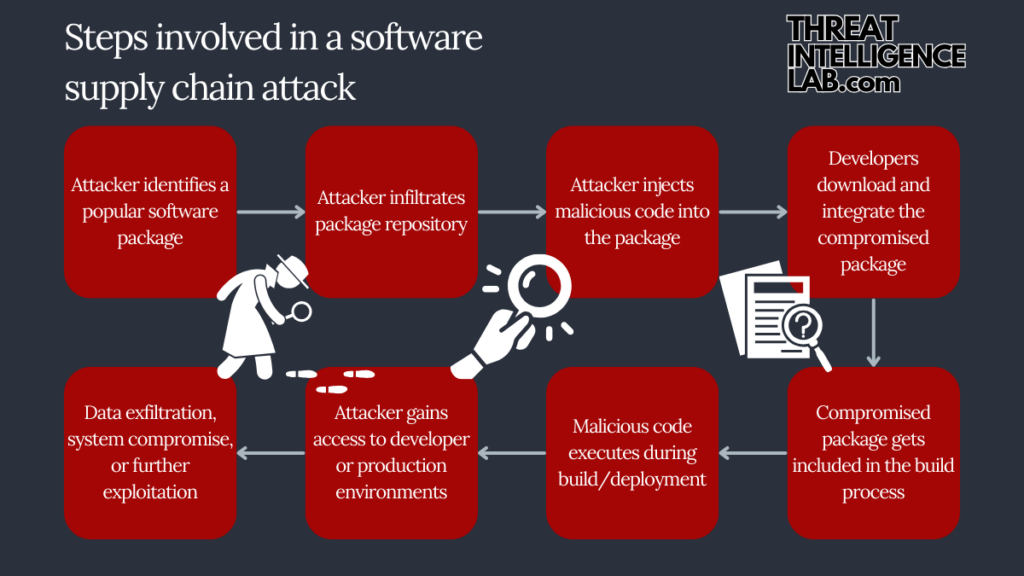
Software supply chain attacks target the processes, tools, and components involved in developing and delivering software. Attackers exploit vulnerabilities in this supply chain to compromise software integrity and security1.
This includes manipulating source code repositories, package managers, compilers, and the infrastructure used to build and distribute software.
The difference between Software Supply Chain attacks and Traditional Supply Chain Attacks
Software supply chain attacks target the digital aspects of software development, such as source code repositories, package managers, and build systems.
These attacks involve injecting malicious code, taking over accounts, and compromising software infrastructure to gain unauthorized access or cause data breaches.
Traditional supply chain attacks focus on the physical supply chain, targeting manufacturers, suppliers, and logistics companies. These attacks involve counterfeiting, tampering with goods, theft, and causing delivery delays to disrupt operations and introduce fraudulent products.
In essence, software supply chain attacks exploit cyber vulnerabilities, while traditional supply chain attacks manipulate physical goods and logistics.
| Aspect | Software Supply Chain Attacks | Traditional Supply Chain Attacks |
|---|---|---|
| Definition | Compromise of software development processes and tools. | Disruption or manipulation of physical goods and logistics. |
| Targets | Source code repositories, package managers, build systems. | Manufacturers, suppliers, logistics companies. |
| Methods | Injecting malicious code, repojacking, account takeovers. | Counterfeiting, tampering, theft, delivery delays. |
| Attack Vector | Cyber vulnerabilities in software components and infrastructure. | Physical access, logistics manipulation, supply chain disruptions. |
| Impact | Unauthorized access, data breaches, system compromises. | Delayed shipments, counterfeit products, financial loss. |
| Examples | SolarWinds, Log4j, Codecov. | Counterfeit electronics, food contamination, cargo theft. |
| Detection | Code analysis, security monitoring, audit logs. | Physical inspections, supply chain audits, tracking systems. |
| Mitigation | SCA tools, two-factor authentication, continuous monitoring. | Vendor vetting, secure transport, inventory management. |
| Primary Goal | Exploit software vulnerabilities to gain broader access. | Disrupt supply chain operations or introduce fraudulent goods. |
| Primary Medium | Digital and cyber channels. | Physical and logistical channels. |
The Rise of Software Supply Chain Attacks
Software supply chain attacks have surged, largely due to our increasing reliance on third-party components.
Attackers understand that compromising a widely-used component can give them access to numerous systems.
High-profile incidents like the SolarWinds breach and the Log4j vulnerability have underscored the severity of these attacks. The stakes are high2, and attackers are growing more sophisticated.
- Cyber Attack Cycle: Actions Phase
- Cyber Attack Cycle: Command & Control (C2)
- Cyber Attack Cycle: Installation Phase
- Cyber Attack Cycle: Exploitation Phase
- Cyber Attack Cycle: Weaponization and Delivery
- Cyber Attack Cycle: Reconnaissance Attacks
Common Types of Software Supply Chain Attacks
Here are some common methods attackers use to infiltrate the software supply chain.
1. Malicious Installation Scripts
Malicious installation scripts are a common attack vector. Attackers inject harmful scripts into installation packages.
When these packages are installed, the scripts execute, compromising the system. This can occur on a developer’s local machine or during the build process. Attackers can steal sensitive data, install backdoors, or execute other malicious activities.
To hunt for these threats, it’s crucial to:
- Monitor Developer Machines: Use tools like Sysmon to detect anomalies in processes and network traffic. Check for unusual process trees and payloads from legitimate software.
- Inspect Build Servers: Whether using vendor-hosted or self-hosted build servers, review workflow logs for unintended actions. Look for unusual network traffic and verify the legitimacy of installation scripts.
2. Secrets Leak
Secrets such as API keys, passwords, and cryptographic keys are critical to security. If these secrets leak, attackers can gain unauthorized access to systems, leading to data breaches and further attacks.
To prevent secrets leaks:
- Configure Audit Logs: Monitor source code management systems for events like login attempts, file modifications, and permission changes.
- Scan for Embedded Secrets: Use tools to scan container images and codebases for forgotten or hardcoded secrets.
3. Malicious Artifacts
Public registries like PyPI, NPM, and Maven are frequent targets for attackers.
They upload malicious packages that appear legitimate but contain harmful code3. These packages can bypass security measures and get integrated into numerous projects.
To mitigate this threat:
- Verify Integrity: Implement integrity checks for all third-party components.
- Use Threat Intelligence: Monitor for Indicators of Compromise (IoCs) related to malicious artifacts and keep abreast of known threats.
- Continuous Monitoring: Regularly scan your codebase for malicious packages using Software Composition Analysis (SCA) tools.
4. Repojacking
Repojacking, or repository hijacking, involves taking over a legitimate code repository’s name or identifier. If a developer changes their repository name and doesn’t secure the old one, attackers can create a new repository with the same name.
This can lead to users inadvertently downloading malicious code.
Prevent repojacking by:
- Monitoring Repository Changes: Track ownership changes and repository name modifications.
- Auditing Old Repositories: Regularly review old and deleted organization names to ensure they aren’t reactivated maliciously.
- Using SCA Tools: Monitor open-source components to ensure they are not susceptible to this type of attack.
5. Account Takeover
In account takeover attacks, attackers gain control of a developer’s account on a code hosting platform.
They can then introduce malicious changes to the codebase. This can be achieved through phishing, stolen credentials, or exploiting weak passwords.
Mitigate account takeovers by:
- Implementing Two-Factor Authentication: Require two-factor authentication for all users with access to code repositories.
- Monitoring for Suspicious Activity: Continuously watch for unauthorized code modifications and irregular login activities.
- Using Strong Passwords: Ensure all accounts use strong, unique passwords to reduce the risk of brute-force attacks.
Mitigating Software Supply Chain Attacks
Mitigating software supply chain attacks requires a proactive and multi-layered approach.
Here are some essential strategies.
Implement Proper Access Controls
Limit access to repositories and build pipelines. Only trusted users should have access, and permissions should be regularly reviewed to minimize the risk of unauthorized changes.
Regularly Review Pipeline Configurations
Pipeline configurations, typically stored in .yml files, should be regularly reviewed for any suspicious or unintended changes. This proactive approach helps identify and prevent tampering.
Use Static Code Analysis Tools
Static code analysis tools can identify vulnerabilities early in the development process.
Integrating these tools into your CI/CD pipeline ensures that code quality and security standards are maintained.
Monitor Third-Party Components
Regularly monitor the third-party components used in your software. Use SCA tools to detect and remediate vulnerabilities in these components. Staying updated with the latest threat intelligence can also help in identifying potentially malicious packages.
- Why Data Breach Report Feeds Are Important
- The Top 10 Essential Log Sources for IT Monitoring
- Dark Web Cybercrime Forums You Should Monitor
- How to Parse and Use VirusTotal feeds
- Getting The Most Out Of URLscan.io
Educate Your Team
Training your development and security teams on the latest threats and best practices is crucial.
Awareness is the first step in prevention4. Ensure that everyone understands the importance of maintaining a secure software supply chain and is equipped to identify potential threats.
Scenarios of Supply Chain Threats
Scenario 1: Malicious Package Hunting
To illustrate the hunting process, consider a scenario where a seemingly innocent application incorporates a malicious package.
The package is added to the project, compromising both the local development environment and the entire software project.
The steps involve:
- Cloning a Repository: Start with an existing application and add a malicious package.
- Deployment Workflow: Add a deployment GitHub Action workflow to deploy the app, making the supply chain vulnerable.
- Monitoring: Scan the project with an SCA tool to detect malicious packages. Check process trees and network traffic for anomalies.
Scenario 2: Spoofing a Malicious Commit
In another scenario, an attacker gains access to a developer’s SSH/GPG keys through social engineering. They then spoof a commit, introducing a malicious GitHub Action Workflow that exfiltrates sensitive information.
The steps involve:
- Gaining Unauthorized Access: The attacker uses stolen credentials to gain access to the repository.
- Spoofing Commits: Modify metadata in commits to push malicious code.
- Monitoring Logs: Use tools to detect unfamiliar workflows and check logs for malicious commands.
Enhancing Security Post-Build
Beyond threat hunting, an effective post-build prevention mechanism is crucial for software supply chain security. Here’s how to enhance your security measures post-build:
- Set Up Alert Systems: Notify development teams about newly added packages in a build. This system detects changes and requires approval before integration, helping teams assess risks associated with unfamiliar components.
- Implement Static Code Analysis and Linting Tools: These tools analyze the codebase for issues like coding errors, style violations, and security vulnerabilities. Early detection of bugs leads to more robust software.
- Enforce Code Quality Standards: Ensure all code meets quality standards through continuous integration and delivery (CI/CD) pipelines.
Conclusion
Software supply chain attacks are a growing threat in today’s interconnected world. Understanding common attack vectors and implementing robust security measures can help mitigate these risks.
I recommend investing in proactive threat hunting and continuous monitoring to stay ahead of potential threats.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- Hide anything in everything
- Hack and Leak Crime
- Supply Chain Attacks: Why Your Vendors Could Be Your Biggest Risk
- Cybersecurity Board Communication: How to Engage with Impact
By doing so, you can ensure the integrity and security of your software supply chain. Implement proper access controls, regularly review pipeline configurations, and educate your team on best practices to build a resilient defense against these sophisticated attacks.
- https://www.mend.io/wp-content/media/2024/05/Essential-Guide-to-Threat-Hunting-2024-Report.pdf ↩︎
- https://naderman.de/slippy/slides/2024-04-23-PHPTEK-Composer-Guide-To-Supply-Chain-Security.pdf ↩︎
- https://github.com/ossf/malicious-packages ↩︎
- https://cybersecurity-centre.europa.eu/document/download/d096a9aa-f032-4bef-8832-853cf7c019d5_en?filename=19%20March%20Webinar.pdf ↩︎
