Your cart is currently empty!

KV Botnet Disrupted by U.S. Government Action
In December 2023, the U.S. government carried out a special operation, approved by a court, to deal with a big problem caused by hackers from China.
These hackers had taken control of hundreds of small routers in people’s homes and offices across the U.S. using a malware called “KV Botnet“.
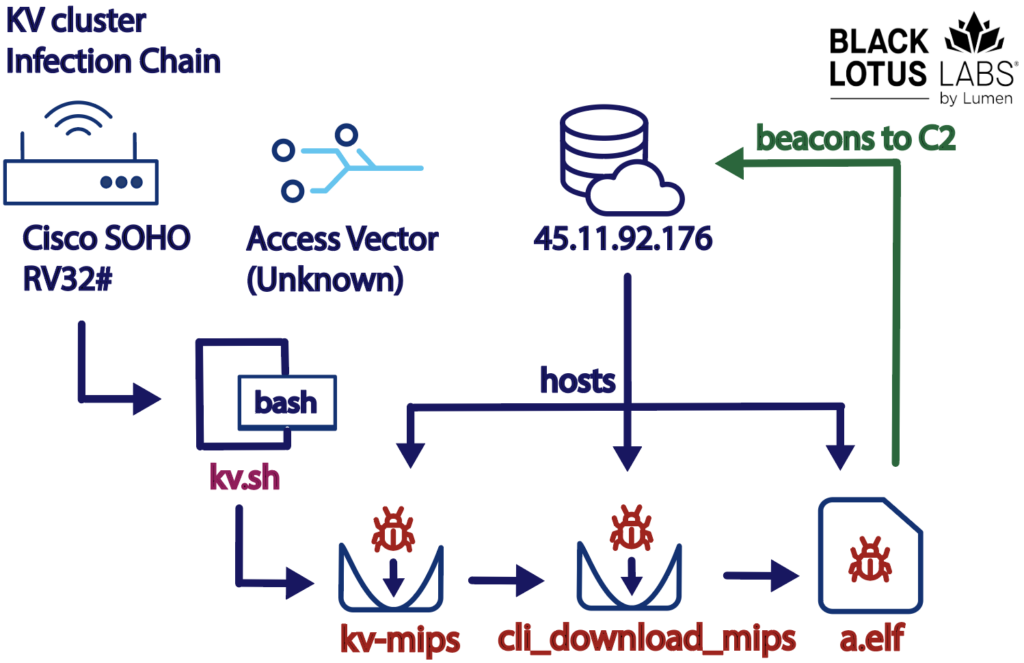
They were using these routers to hide their tracks and attack important U.S. and foreign targets, including critical infrastructure like communications and energy sectors.
Most of these routers were made by Cisco and NetGear and were vulnerable because they were old and no longer getting security updates from the manufacturers.
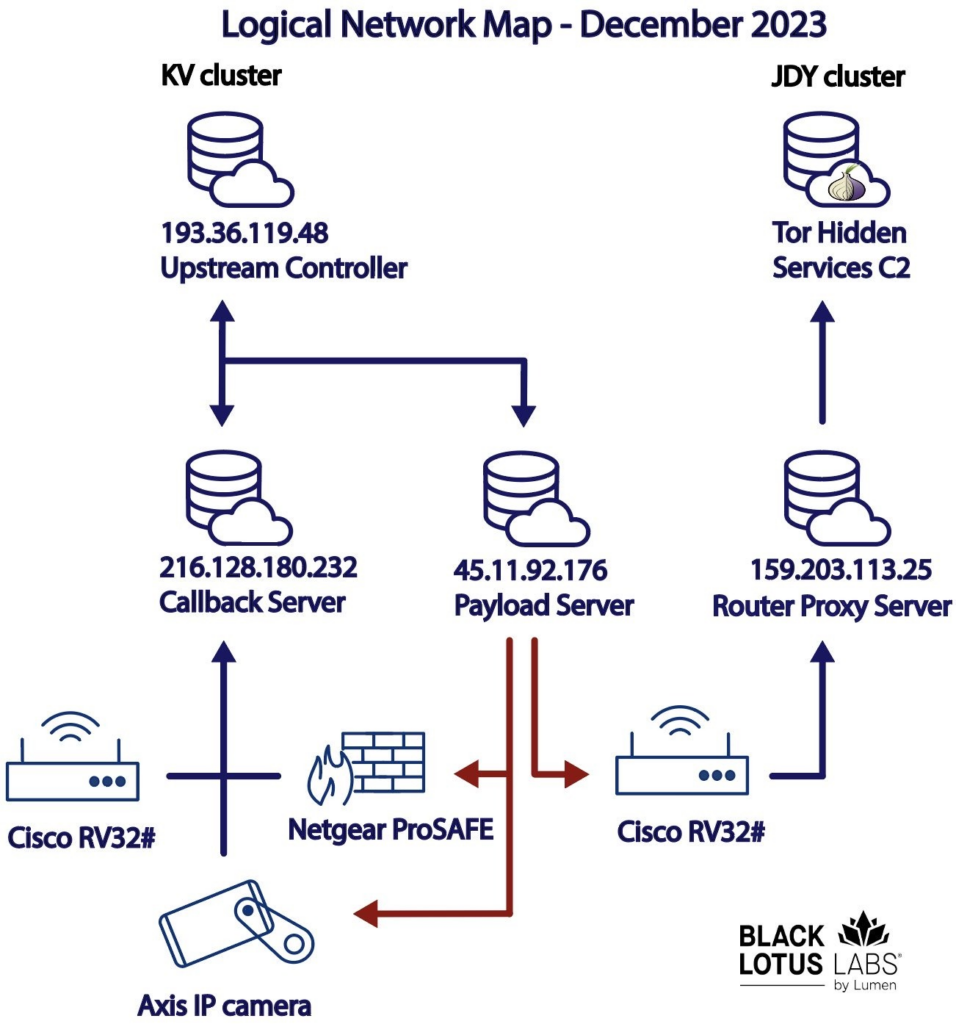
The government’s operation involved removing the harmful malware from these routers and taking steps to make sure they couldn’t be easily hacked again, like blocking certain communications.
U.S. officials, including the Attorney General and FBI Director, said this operation was important to stop these Chinese hackers from doing more damage, especially to critical infrastructure in the U.S.
They also emphasized the importance of working with private companies and the public to fight against these cyber threats.
The government tested their actions on the affected routers to make sure they didn’t interfere with how they normally work.
They also notified the owners of these routers about what they did. The fixes they made are temporary, and the owners can undo them by restarting their routers. However, if they don’t take similar security steps, their routers could get hacked again.
The FBI continues to investigate these Chinese hackers and encourages people to replace old routers that could be vulnerable to attacks. If someone thinks their router is compromised, they can report it to the FBI or CISA.
- People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection
- Volt Typhoon targets US critical infrastructure with living-off-the-land techniques
- Routers Roasting On An Open Firewall: The KV-Botnet Investigation
- Secure by Design Alert: Security Design Improvements for SOHO Device Manufacturers
