Your cart is currently empty!

Host-based Intrusion Detection Systems (HIDS) stand out as a critical component in safeguarding individual hosts like servers, workstations, and mobile devices.
Let’s delve into how HIDS1 operate, their benefits, and the nuances of choosing and using them effectively.
How Host-based Intrusion Detection Systems Work
HIDS are installed directly on the host they’re meant to protect, diligently monitoring system files, logs, processes, and applications.
Their role is akin to a vigilant guard, constantly on the lookout for threats specifically targeting the host, such as malware, unauthorized access, or data theft.

What sets HIDS apart is their ability to offer a detailed view of host activity and behavior, aiding in verifying system integrity and compliance.
However, they are not without challenges. Being resource-intensive and requiring frequent updates, HIDS demand careful management.
Moreover, they’re potentially vulnerable to tampering by attackers, a risk that necessitates robust security practices.
Common HIDS and NIDS detection methods
I’ve found that understanding the different detection methods used by Host-based Intrusion Detection Systems (HIDS) and Network-based Intrusion Detection Systems (NIDS) is crucial.
These systems primarily utilize two methods: anomaly-based detection and signature-based detection.
Both HIDS and NIDS can employ either of these strategies, offering unique advantages in safeguarding systems.
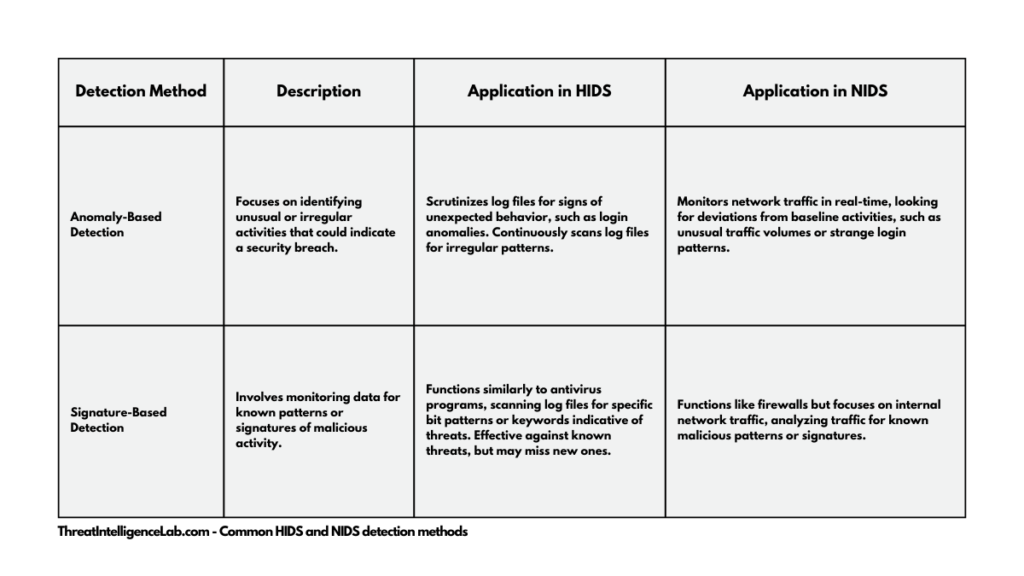
Anomaly-Based Detection
Anomaly-based detection focuses on identifying unusual or irregular activities that could indicate a security breach.
This method is akin to finding a needle in a haystack – the needle being any activity that deviates from the norm.
- In HIDS: This approach involves scrutinizing log files for signs of unexpected behavior. For example, if a user’s credentials are used to access the network from multiple global locations within a short time, it’s flagged as anomalous. HIDS using this method continuously scan log files, searching for these irregular patterns.
- In NIDS: The approach is more real-time. NIDS monitor network traffic as it happens, looking for anomalies that deviate from the established baseline of normal network activity. This could include unusual traffic volumes, strange login patterns, or uncharacteristic data transfers.
Signature-Based Detection
The second major method is signature-based detection, which involves monitoring data for known patterns or signatures of malicious activity.
- In HIDS: This method functions similarly to antivirus programs. HIDS scan log files, much like how antivirus software scans program files, searching for specific bit patterns or keywords indicative of a threat. This method is highly effective against known threats but can struggle to identify new, unknown attacks.
- In NIDS: Here, it’s similar to the functioning of firewalls, but with a focus on internal network traffic. NIDS running signature-based detection analyze the traffic within the network, checking for known patterns or signatures that match predefined criteria of malicious activities.
The Benefits of Host-based Intrusion Detection Systems
From my experience, the benefits of HIDS in a cybersecurity framework are undeniable:
- Targeted Protection: HIDS are uniquely capable of defending the host against specific threats, offering a tailored shield against various forms of cyberattacks.
- In-depth Monitoring: The level of detail Host-based Intrusion Detection Systems provide in monitoring host activities is broad. This allows for early detection and response to potential threats, a crucial factor in mitigating risks.
- Compliance Assurance: For businesses where compliance is non-negotiable, HIDS are invaluable in ensuring systems adhere to required standards and regulations.
- Adaptive Threat Response: With HIDS, you can configure responses to threats in diverse ways, enhancing the agility and effectiveness of your cybersecurity strategy.
The downsides of only using a HIDS
Using only a Host-based Intrusion Detection Systems in your cybersecurity strategy, while beneficial in certain aspects, presents several downsides:
Limited Scope of Coverage
Host-based Intrusion Detection Systems are designed to monitor individual hosts or devices. This means they lack the capability to analyze network-wide traffic patterns. As a result, broader network attacks or anomalies that don’t directly affect a single host might go undetected.
Resource Intensity
HIDS can be resource-intensive, as they require processing power and memory on the host systems where they are installed. This can lead to reduced performance of the host device, especially if it’s already under heavy use.
Blind to Encrypted Network Traffic
HIDS generally do not have the ability to inspect encrypted network traffic. This limits their effectiveness in detecting threats within encrypted communications, which are increasingly common in modern network environments.
Vulnerability to Host Compromise
If a host system is compromised, the Host-based Intrusion Detection Systems installed on it may also be vulnerable. Attackers who gain administrative privileges could potentially disable the HIDS or manipulate its logs and alerts, rendering it ineffective.
Complex Management
In large organizations, managing HIDS on each individual host can become complex and time-consuming. Each system might require separate configuration, updates, and maintenance, increasing the workload for IT security teams.
Limited Contextual Information
Host-based Intrusion Detection Systems focus on activities within their specific host, which can sometimes lead to a lack of contextual information about broader network activities.
This can result in difficulty in distinguishing between malicious activities and benign anomalies, potentially leading to a higher rate of false positives or negatives.
Dependence on Host Integrity
HIDS effectiveness is heavily reliant on the integrity of the host system. If the host is already compromised or not properly secured, the HIDS may not function optimally.
Delayed Detection of Network-Based Attacks
Since HIDS are not designed to analyze network traffic, they may be slower or unable to detect network-based attacks until these attacks interact with the host, potentially leading to delayed responses.

Choosing and Using One
Selecting and deploying HIDS is not a straightforward task; it requires a nuanced approach.
Here are some key considerations
Understand Your Environment
The nature of your network and hosts will significantly influence the type of HIDS you need. Size, complexity, and specific vulnerabilities should guide your choice.
Anticipate Potential Threats
Knowing the types of cyber threats you’re most likely to face enables you to choose a solution capable of countering them effectively.
Align with Security Goals
Your broader security goals and policies should be in harmony with the solution you choose, ensuring a cohesive cybersecurity strategy.
Budgetary and Resource Constraints
The financial and human resources at your disposal will affect both the selection and maintenance of HIDS.
Continuous Improvement
The cybersecurity landscape is dynamic, with new threats emerging constantly. Regular testing and updating of your HIDS are crucial to maintain efficacy.
Integrate into a Wider Strategy
HIDS should not operate in isolation but as part of a comprehensive security strategy encompassing prevention, detection, response, and recovery.
- https://csrc.nist.gov/glossary/term/host_based_intrusion_detection_and_prevention_system ↩︎
