Your cart is currently empty!
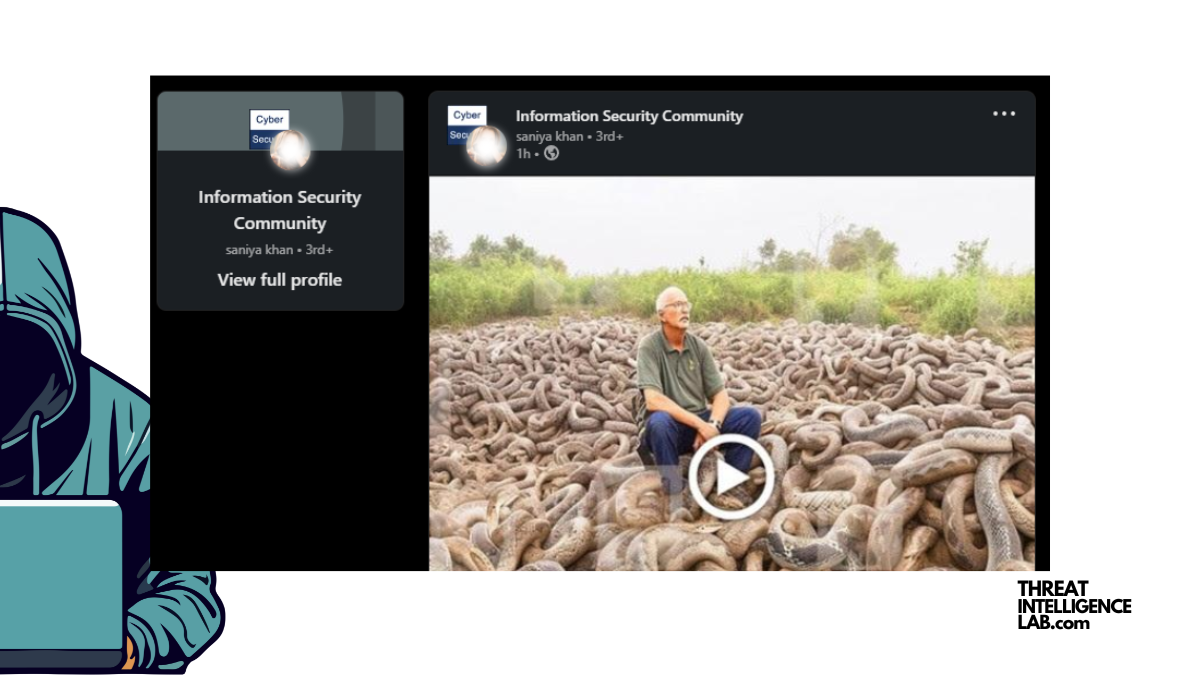
Be cautious of these Shocking LinkedIn posts
Don’t waste your time. Be aware. These types of post are here with only 1 reason. To make you click.
What happens when you click such posts? Are they bad? Will you get ransomware? Will you lose your Crypto stash? — Post continues below.
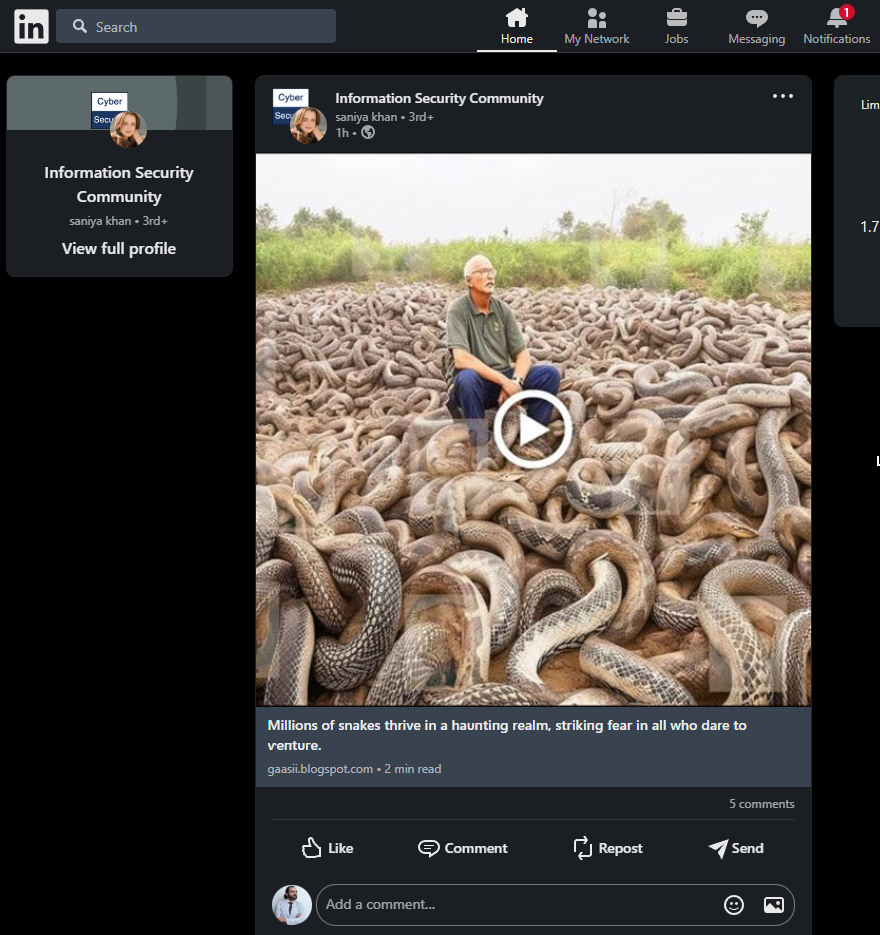
History
These type of posts are not new to the cybersecurity industry. Back in 2014, this was one of the fastest working methods to get clicks (and build website authority) on Facebook.
The actors behind this attack would share their posts in crowded Groups1 with the idea to lure unaware internet users to their pages.
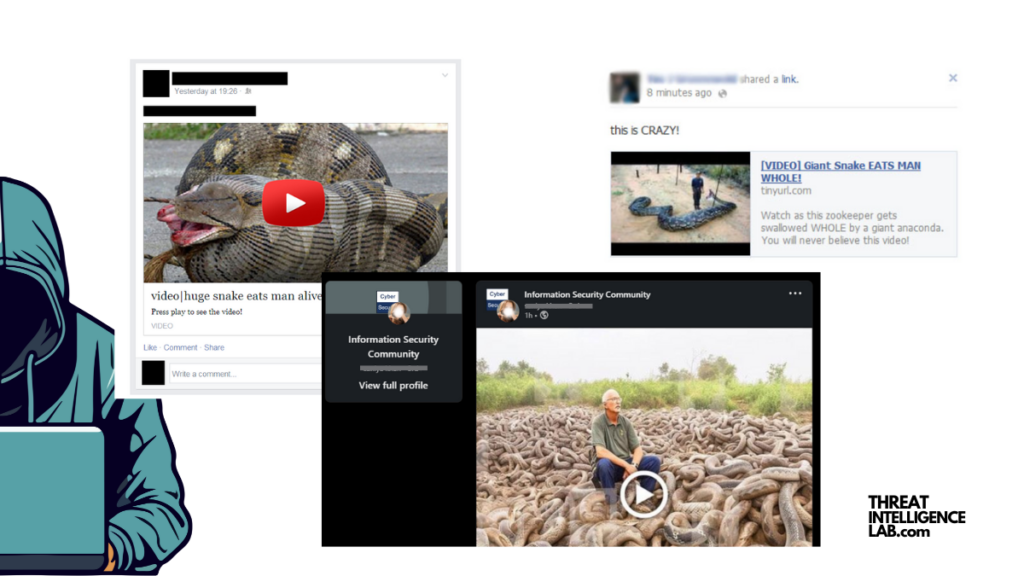
Some of the clickbait titles they would use were:
- “Huge Snake Eats Man Alive!”
- “Video Rollercoaster Crash”
Rogue Browser Extension
The Facebook Rogue Browser Extension scams typically involve deceptive posts or ads that lure users with sensational or shocking content headlines like “OMG Snake eats man alive!2” or “Horrific rollercoaster crash!” These scams exploit our human curiosity and the urge for sensational news to trick users into clicking on links.
When clicked, these links lead users not to the promised video or article but to pages that prompt them to install a browser extension or plugin.
Here’s how the scam typically unfolds:
- Sensational Content: The scam starts with a post or advertisement that claims to link to sensational content, creating a strong incentive for users to click.
- Installation Prompt: Instead of leading to the promised content, the link directs the user to install a browser extension or plugin, claiming it’s necessary to view the content.
- Malicious Extension: The extension or plugin is, in fact, malicious. It may have various harmful capabilities, such as:
- Stealing personal information or login credentials by monitoring the user’s web activity.
- Hijacking the user’s social media accounts to spread the scam further by posting the same or similar deceptive content.
- Injecting ads into web pages the user visits or redirecting the user’s browser to other malicious sites.
- Downloading and installing additional malware onto the user’s device.
The success of these scams lies in their exploitation of social engineering techniques to prey on natural human curiosity and the trust users place in content shared by friends. Once the malicious extension is installed, it can be difficult to remove, and the effects can be wide-ranging, from privacy breaches to financial loss.
Track the attack
Bad Adaption to LinkedIn (For Now)
The adaptation of the Facebook Rogue Browser Extension scam to LinkedIn follows a similar pattern. You would expect it to be tailored to the professional context and audience of the platform, but no.. it is still the same “[INSERT SHOCKING TITLE]” scheme.
Here’s how this scam typically unfolds on LinkedIn:
- Professional Bait: Scammers post articles or updates with eye-catching headlines that seem relevant to professional interests or current events. These might include shocking industry news, incredible job offers, or exclusive research reports, designed to pique the curiosity of LinkedIn users.
- Requirement for Action: When users click on the link to access the purported content, they are redirected to a page that instructs them to install a browser extension or a piece of software to proceed. The reasons given can range from viewing exclusive content to compatibility issues with LinkedIn features.
- Malicious Software: The software or extension in question is malicious. It can perform a variety of harmful actions, such as:
- Stealing personal and professional data, including login credentials.
- Taking control of the LinkedIn account to spread the scam further by sending messages to connections or posting the scam on the user’s behalf.
- Monitoring the user’s web activity to gather sensitive information.
- Installing additional malware that can lead to further compromise of the user’s device.
Porting this scam to LinkedIn leverages the platform’s professional setting, where users might be more inclined to trust content that appears to be relevant to their careers or industry.
This makes the scam potentially more dangerous, as users may let their guard down due to the professional nature of LinkedIn compared to more casual social networking sites.
Preventive Measures
To protect against such scams on LinkedIn or any other professional network, it’s crucial to apply a critical mindset towards any sensational or unusually enticing content, especially when it prompts the download of additional software or extensions. Some specific tips include:
- Verify the source of the content and check for other reputable reports or mentions before taking action.
- Be cautious of any request to install software or extensions as a prerequisite to access content. Legitimate professional resources typically do not require such actions.
- Regularly review and manage the browser extensions you have installed, removing any that are unnecessary or unrecognized.
- Use reputable antivirus and internet security software to help detect and block malicious downloads and websites.
