Reza Rafati

Cyber Attack Cycle: Installation Phase
One critical but often underestimated stage in the cyber attack cycle is the installation phase. This is the moment when the attacker secures their presence on the victim’s system, setting the stage for ongoing control or damage. Understanding this phase is crucial for effectively defending against and responding to cyber threats. The Significance of the…

Cyber Attack Cycle: Exploitation Phase
This is the stage where attackers turn identified vulnerabilities into actual attacks, using known methods to breach security. Today, I’ll explain why this phase is pivotal, outline common techniques attackers use, and show you how to defend your systems effectively. Understanding the Exploitation Phase In the exploitation phase, the action heats up: attackers have already…
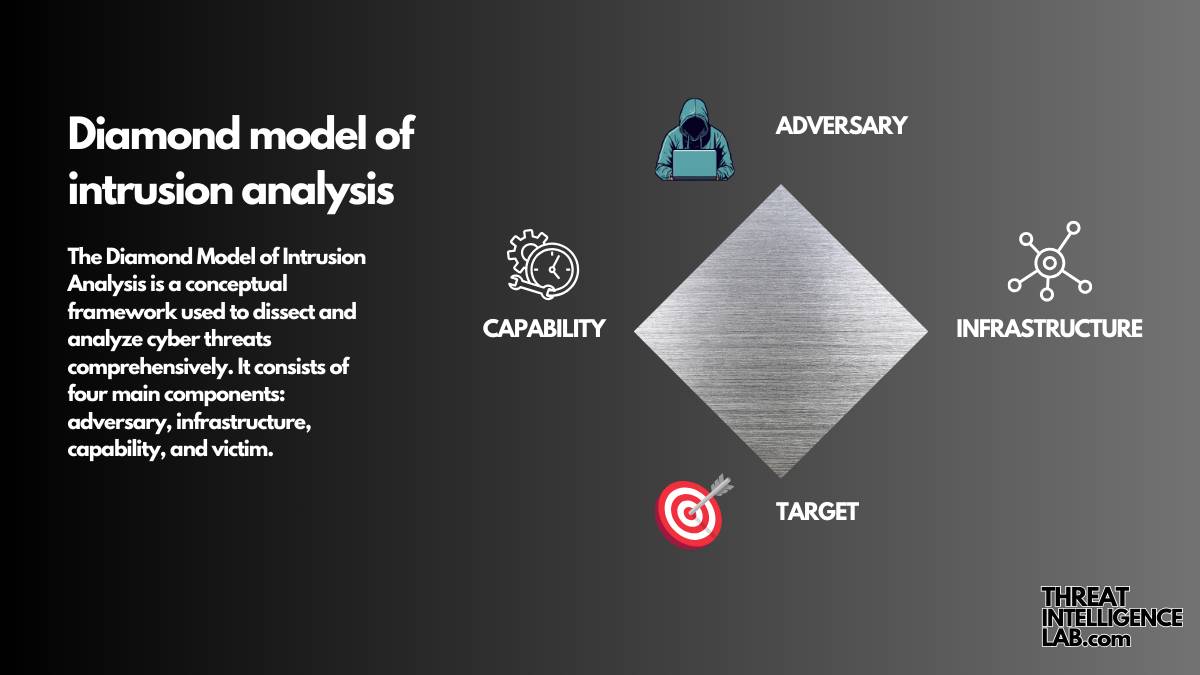
Understanding the Diamond Model of Intrusion Analysis
The Diamond Model of Intrusion Analysis framework stands out for its clarity and effectiveness. Today, I’m going to share why this model is pivotal in understanding cyber attacks and how it can significantly enhance your security posture. What is the Diamond Model of Intrusion Analysis? The Diamond Model was developed to provide a more structured…
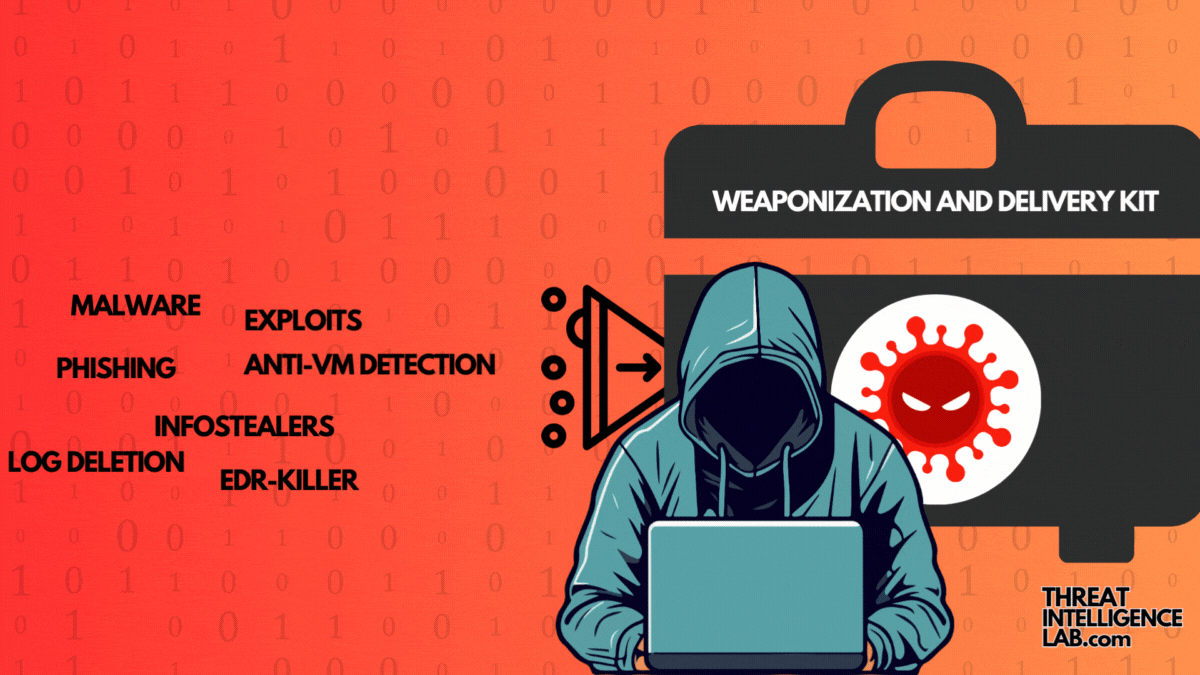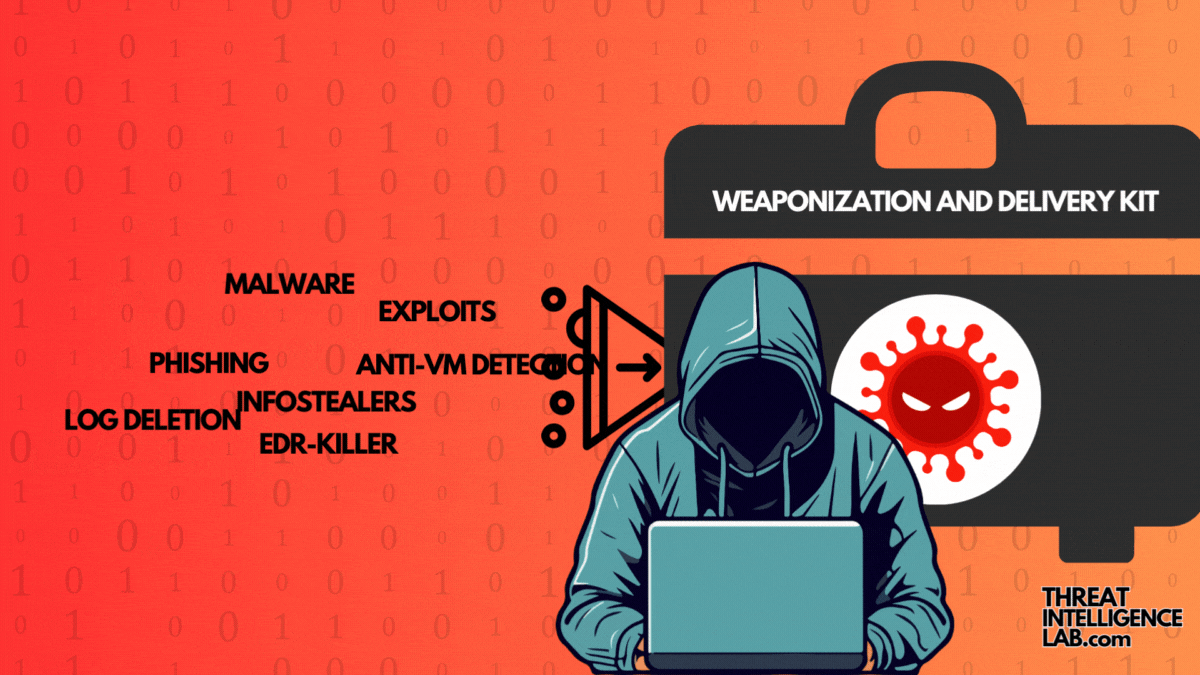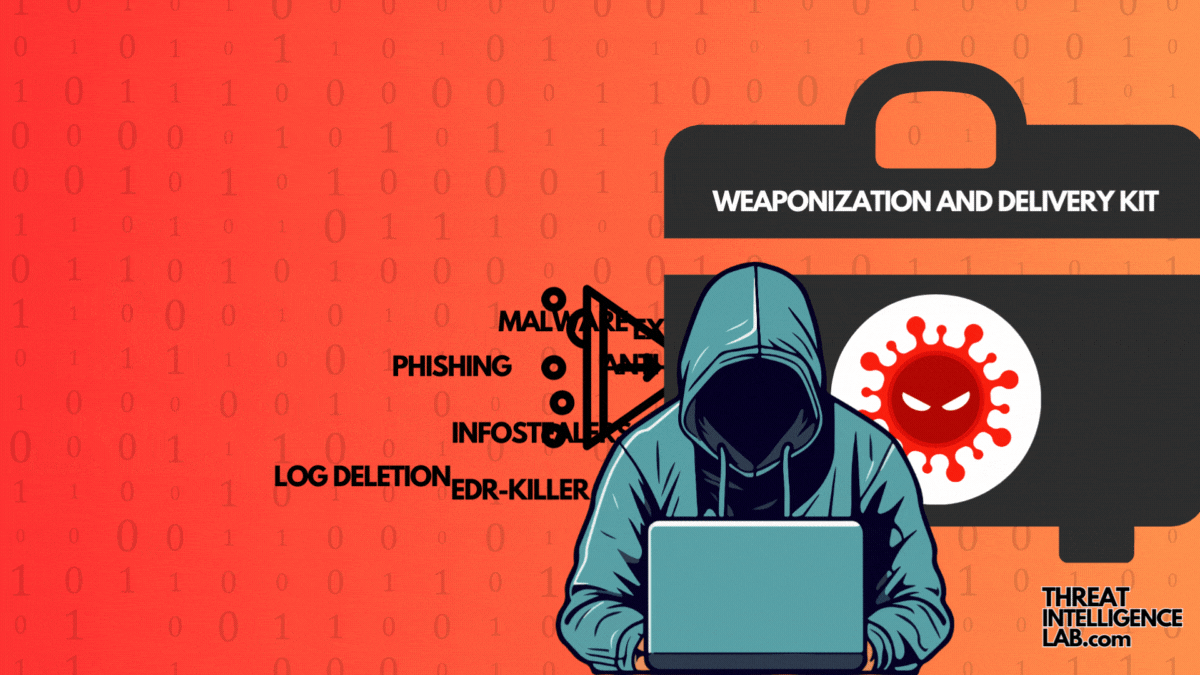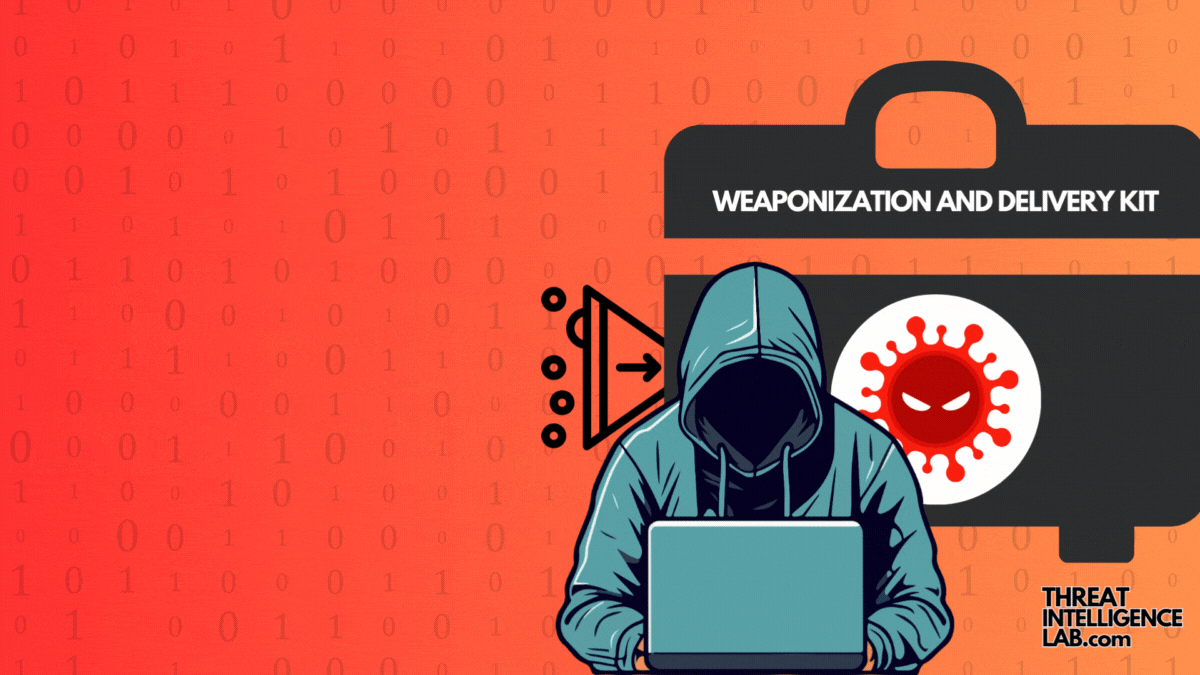
Cyber Attack Cycle: Weaponization and Delivery
Today, let’s delve into the second step: Weaponization and Delivery. Here, attackers prepare and send their malicious payload to the target. Understanding this phase is crucial because it’s where the groundwork is laid for the impending attack. By dissecting this process, we can better prepare and defend against these tactics. What is Weaponization in Cyber…
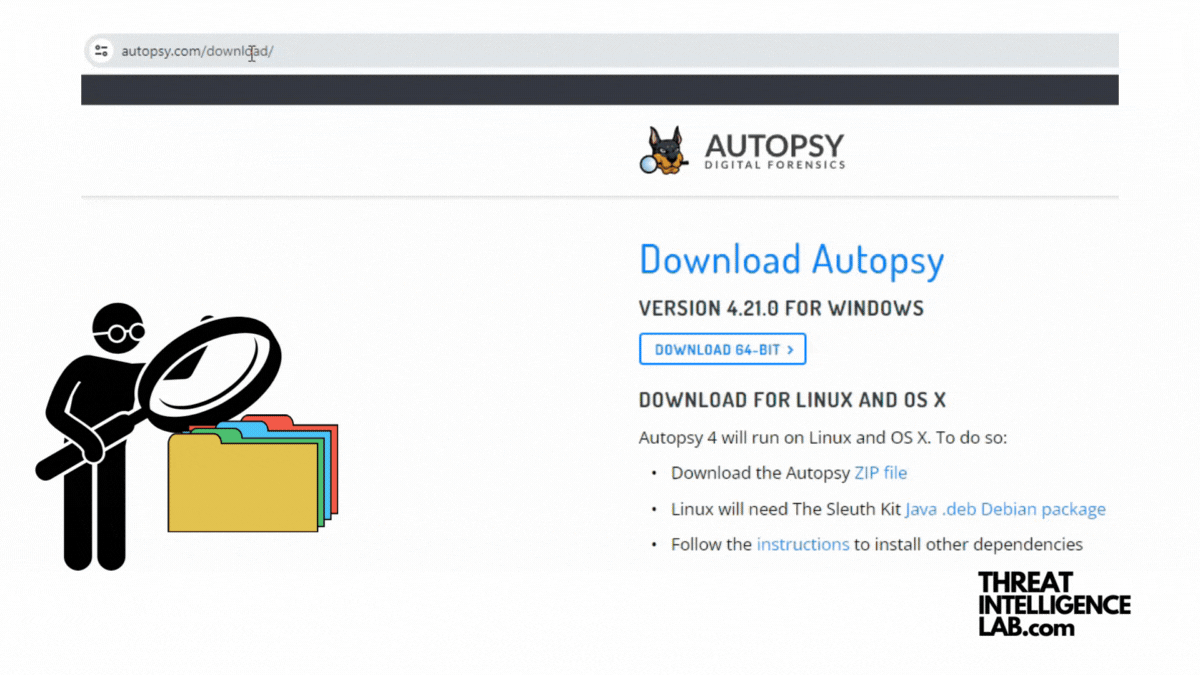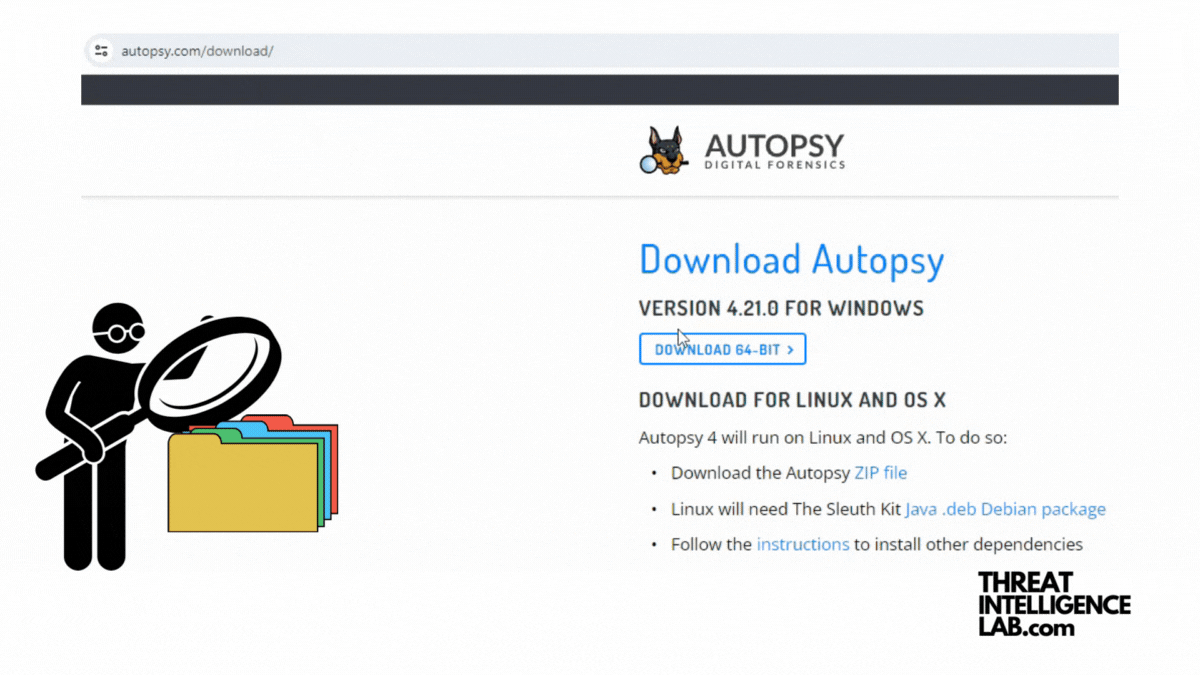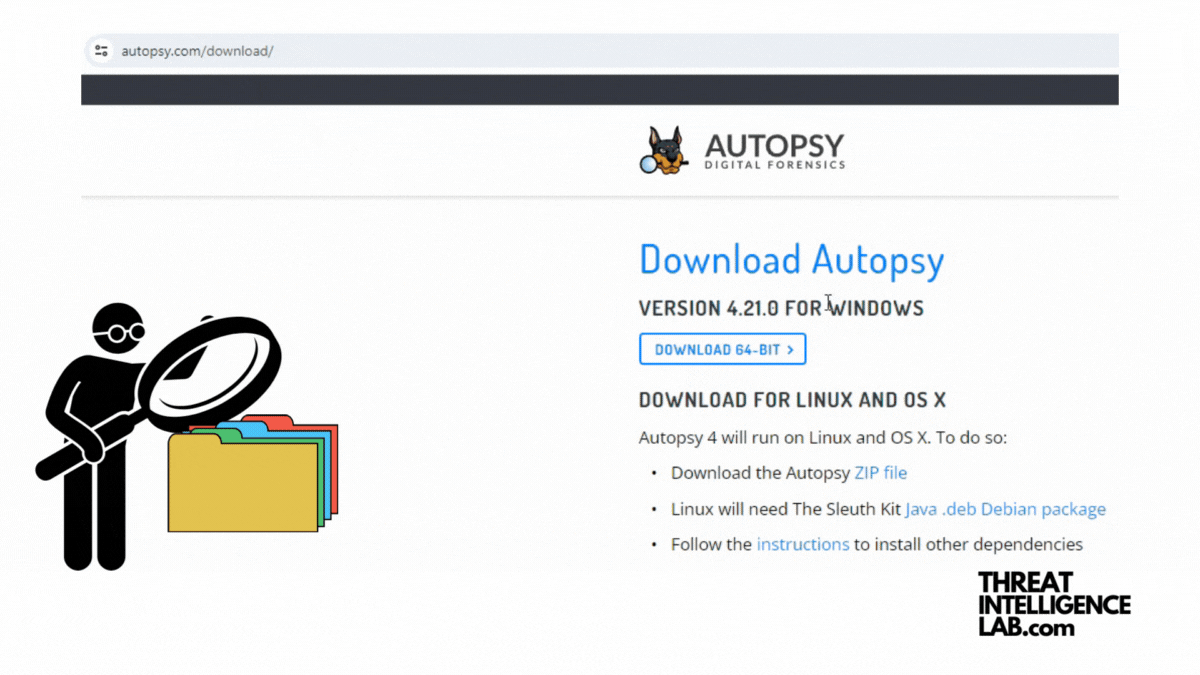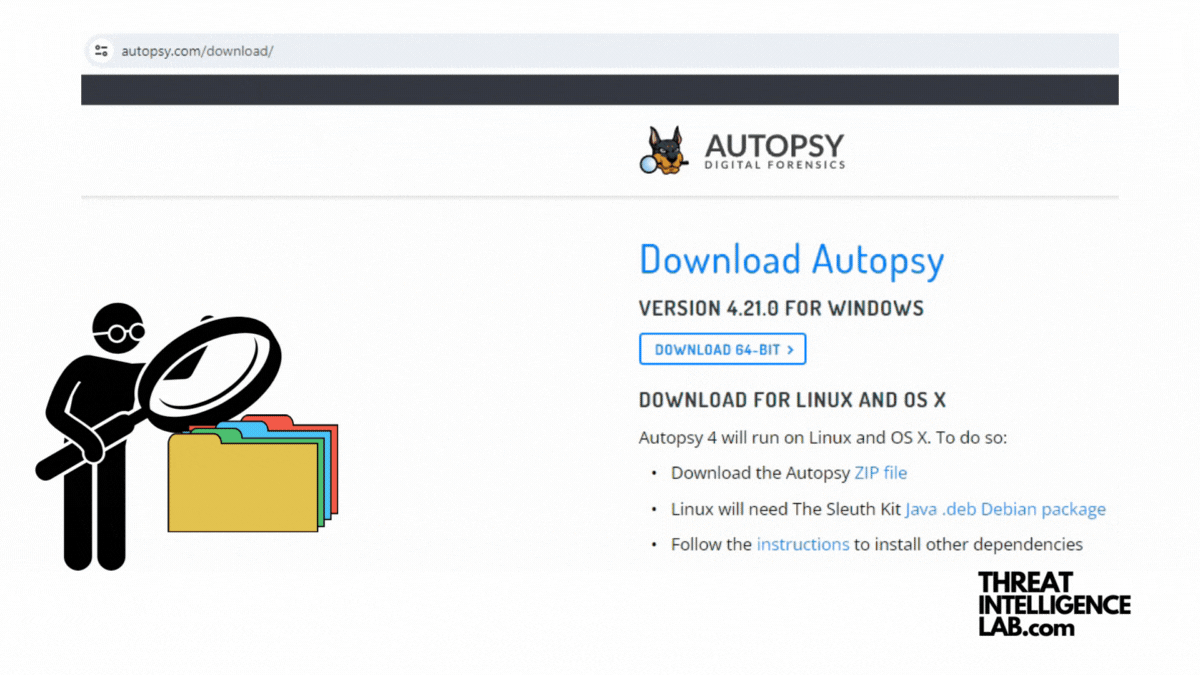
Introduction to Disk Analysis Using Autopsy
Today, I’ll take you through Autopsy, a comprehensive digital forensics platform. Autopsy is made for analyzing disk images, recovering deleted files, and uncovering user activities. Installing Autopsy on Windows Prerequisites Step-by-Step Installation Installing Autopsy on Linux Prerequisites Step-by-Step Installation Installing Older Versions You can find other versions of Autopsy at: Starting up 1. Setting Up…
Cyber Attack Cycle: Reconnaissance Attacks
The reconnaissance stage, the initial step in the widely recognized Cyber Attack Cycle or “Cyber Kill Chain” developed by Lockheed Martin, focuses on actively gathering information. In this detailed exploration, I will try to explain the reconnaissance phase. The Anatomy of Cyber Reconnaissance Reconnaissance1 fundamentally serves as an intelligence-gathering mission. Cyber attackers use this phase…

Understanding Bits and Bytes
Learn more about Bits and Bytes: Unlock the essentials of digital data and how they power our digital world.
Responding to a Potentially Compromised Firewall
When you suspect that your firewall has been compromised, it’s crucial to act swiftly and effectively to secure your network. This guide outlines the steps network engineers should take to respond to such a security incident. Why Didn’t My EDR Protect My Firewall? Some people think EDR includes firewalls. But firewalls don’t have EDR software,…
The difference between cybersecurity and cyber intelligence
In my experience working in threat intelligence, I’ve come to understand the critical distinctions between cybersecurity and cyber intelligence. These two fields, though often intertwined, address different aspects of information security. Let’s break down the differences. The Realm of Cybersecurity Cybersecurity focuses on the protection of IT infrastructure, networks, and data from cyber threats and…
The MongoDB Ransomware Experiment
Imagine setting up a honeypot, a decoy system, to mimic a vulnerable MongoDB database, just to see what might happen. That’s exactly what we did. Within an hour, our honeypot was not only discovered but also compromised, with all its data encrypted and replaced by a ransom note. Our MongoDB Honeypot Experiment Our honeypot was…
